- Cisco Community
- Technology and Support
- Security
- Network Security
- 1 website is blocked on Cisco ASA5505
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
1 website is blocked on Cisco ASA5505
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 08:42 AM - edited 02-21-2020 06:23 AM
Hey everyone,
Let me preface this by saying I have very little xp with Cisco's in general but know enough to provide logs and configs if necesarry.
The problem my client is having is trying to access the website www.sjrwmd.com
For some reason the Cisco is blocking this one website and I can't figure out why.
Let me know what info you need from me and I will be sure to post it.
Thanks!
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 10:12 AM
While it's technically possible to use an ASA 5505 to block individual websites, it's a very seldom used feature.
A more likely scenario is a misconfiguration of DNS or such. Can the user resolve the IP address of that web site correctly? For me it comes up as:
Name: sjrwmd.com
Address: 202.71.99.194
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 10:19 AM
Hi Marvin,
It does resolve an IP although it is different than what you are showing.
Name: sjrwmd.com
Address: 67.225.240.249
However when I perform an nslookup from my machine (Not behind or associated with the ASA) I receive the same IP address as above and the site works fine from my computer.
Any other suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 10:24 AM
You can check the ASA configuration for a URL blocking rule or an access-list entry blocking that IP address.
Try the following to check for those:
show run regex
show run | i 67.225.240.249
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 12:12 PM
When I ran those commands nothing showed up
ciscoasa# show run regex
ciscoasa# show run | i 67.225.240.249
ciscoasa#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 09:19 PM
The lack of any confguration commands relevant to that web site or ip address would seem to indicate that the ASA 5505 is not the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2017 06:06 AM
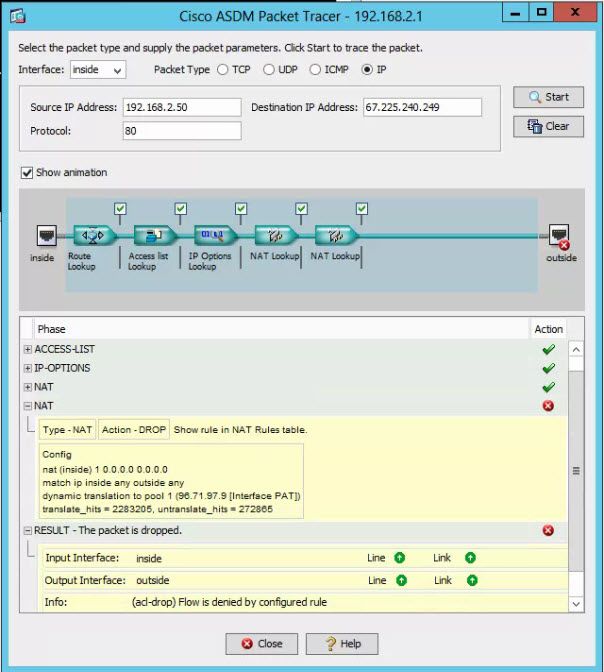
Hey Marvin,
Does this Packet Trace tell you anything?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 06:26 AM
It's not immediately obvious why the NAT is affecting one site that way.
Are you able to share the sanitized ASA configuration or at least "show run nat"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2017 09:42 AM
Hey Marvin,
Here is the show run nat.
ciscoasa# show run nat
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
ciscoasa#
here is the Show Run
!
hostname ciscoasa
enable password (hidden) encrypted
passwd (hidden) encrypted
names
name 192.168.2.50 (hidden)
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address (hidden) 255.255.255.248
!
interface Vlan5
no nameif
security-level 50
ip address dhcp
!
ftp mode passive
object-group service RDP tcp
port-object eq 3389
object-group icmp-type DM_INLINE_ICMP_1
icmp-object echo
icmp-object echo-reply
object-group service RDC46524 tcp-udp
description RDC Port
port-object eq 46524
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
access-list outside_access_in extended permit object-group TCPUDP any interface outside eq 46524
access-list outside_access_in extended permit icmp any any object-group DM_INLINE_ICMP_1
access-list outside_access_in extended permit ip any any inactive
access-list inside_nat0_outbound extended permit ip any 192.168.2.160 255.255.255.224
access-list inside_access_in extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool RemoteVPN 192.168.2.175-192.168.2.180
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface 46524 (hidden) 3389 netmask 255.255.255.255
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 (default gateway)1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
aaa-server LDAP_SVR_GRP protocol ldap
aaa-server LDAP_SVR_GRP (inside) host (hidden)
timeout 5
server-type auto-detect
http server enable
http 192.168.1.0 255.255.255.0 inside
http 192.168.2.0 255.255.255.0 inside
http 74.93.173.29 255.255.255.255 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
auth-prompt prompt Please use your network credentials, These are the same as your Domain (LG2) Login.
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.168.2.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy RemoteVPN internal
group-policy RemoteVPN attributes
dns-server value 192.168.2.50
vpn-tunnel-protocol IPSec
default-domain value (hidden)
username nettech password (Hidden)
tunnel-group RemoteVPN type remote-access
tunnel-group RemoteVPN general-attributes
address-pool RemoteVPN
authentication-server-group LDAP_SVR_GRP
default-group-policy RemoteVPN
tunnel-group RemoteVPN ipsec-attributes
pre-shared-key *****
!
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:7e7a7c1856e6493386f82ea334600df4
: end
ciscoasa#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2017 12:47 AM
Sorry for the delay but nothing in that running config seems incorrect to me. Have you had any progress meanwhile?
The only thing I observe is that you appear to be running old code (8.2 or earlier) from the syntax of the NAT rules. Have you rebooted the firewall at all lately (like in the past several months)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2017 06:41 PM
Hey Marvin,
I haven't made any progress on this. Tonight I rebooted the ASA and the issue persists. I will look into updating the ASA as well and see if that helps and then post it here.
I read something about asymmetrical routing possibly cuasing the issue.... Any ideas?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide