- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Secure AP onboarding- An Introduction to Enhanced Network Security
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-01-2024 10:55 AM - edited 04-04-2024 02:38 AM
Introduction:
Catalyst Center's release 2.2.3 marked the introduction of the Secure AP Onboarding feature, a significant advancement for network administrators seeking robust security measures. This feature facilitates the seamless integration of access points into the network in environments where the access layer, or fabric edge within a Software-Defined Access (SDA) framework, mandates closed authentication.
The Plug and Play (PnP) process has been significantly improved to support the dissemination of supplementary information to access points. This enhancement encompasses the provision of crucial elements like 802.1X credentials and the designated authentication methods. Leveraging the Catalyst Center as the PnP server, the system authorizes access points to initiate a network connection by employing the credentials distributed via the PnP protocol, thereby guaranteeing their authentication. The Plug and Play (PnP) enhancements were introduced with IOS XE version 17.6. Ensure that both the access point (AP) and the Wireless LAN Controller are running a version of the IOS XE software that is 17.6 or higher.
This feature serves a dual purpose: it restricts network connectivity exclusively to authorized access points, while allowing authorized access point to allow establishment of a Control and Provisioning of Wireless Access Points (CAPWAP) session between the access points and the Wireless LAN Controller. Consequently, this mechanism significantly reinforces the security posture of the network infrastructure by allowing only verified access points to participate, thereby maintaining the integrity and reliability of the wireless network.
Procedure to enable Secure AP onboarding:
To enable Secure AP Onboarding, follow the outlined procedure below:
- Access the Catalyst Center: Begin by logging into the Catalyst Center interface, which serves as the central point for managing your network configurations.
- Navigate to Wireless Design Settings: Once logged in, proceed to the ‘Wireless' section where you can modify settings that affect the overall wireless design.
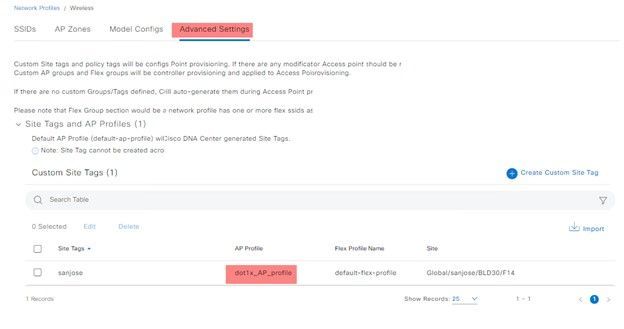
Enable AP Authentication: Create an AP profile which allows the option to enable AP authentication' This setting is crucial as it determines whether access points are required to authenticate before joining the network.
The next step is to map the Access Point (AP) profile to the appropriate Wireless Network. Map the created AP profile to a customized site tag:
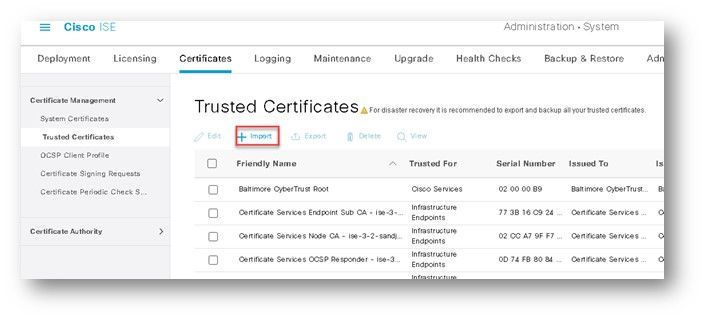
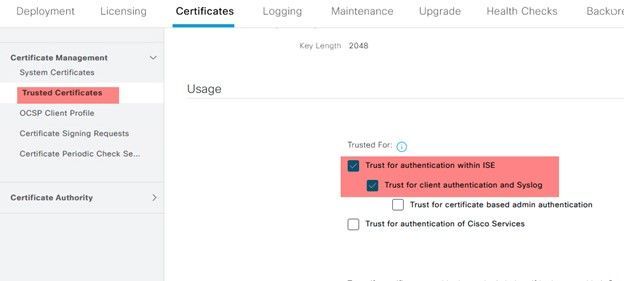
Ensure that, during the import process, the certificate is enabled for client authentication
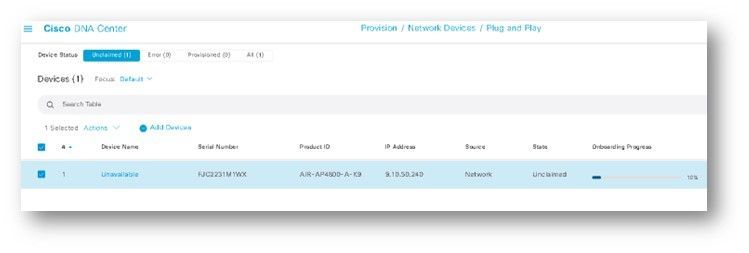
An access point, in factory default mode, is not configured with a 802.1X supplicant. The switchport to which the access point is attached should be configured with dot1x authentication as the first priority and MAB as the second priority. The fallback from dot1x to MAB only happens if the endpoint fails dot1x authentication. Upon initial connection to the network, the access point undergoes a MAC Authentication Bypass (MAB) process, which provides restricted network access for the purposes of locating the Plug and Play (PnP) server, along with enabling DNS and DHCP functionalities. The PnP server is identified through Option 43 specified in the DHCP transaction.
Upon successful authorization of the port on the fabric edge for MAC Authentication Bypass (MAB), the access point (AP), upon receipt of the Plug and Play (PnP) server information via Option 43, can proceed to discover the PnP server, the Catalyst Center. The AP then initiates a PnP call to the Catalyst Center, and a claim must be made to enable the PnP process to provision the 802.1X credentials and method to the Access Point.
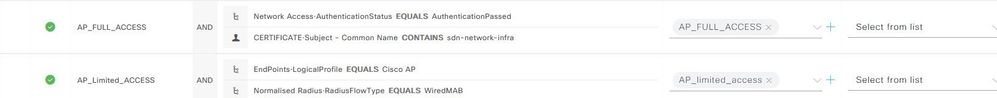
For an access point (AP) to initially obtain limited access and subsequently full network access, specific policies must be configured within Cisco Identity Services Engine (ISE). These policies typically include:
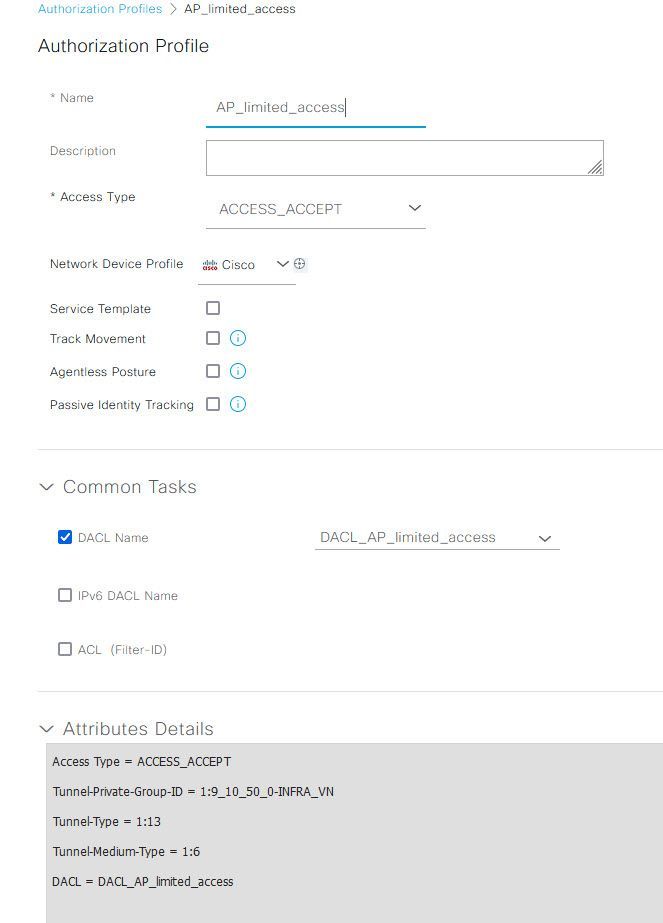
- MAB Policy for Limited Access: A policy that grants limited access to the network through MAC Authentication Bypass (MAB) must be in place. This initial access is often restricted to allow the AP to perform essential tasks such as locating the PnP server, and accessing DNS and DHCP services.
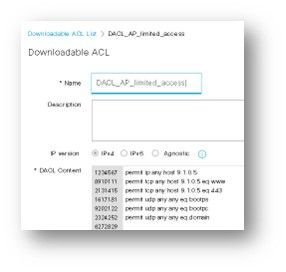
- Authorization Profile for Limited Access: An authorization profile connected to the MAB policy, detailing the specific access rights, such as ACLs or VLANs that define the scope of limited access.
- 802.1X Policy for Full Access: Once the AP is provisioned with the necessary 802.1X credentials, a full access policy using 802.1X authentication should be applied. This policy dictates the conditions under which the AP is granted full access to the network.
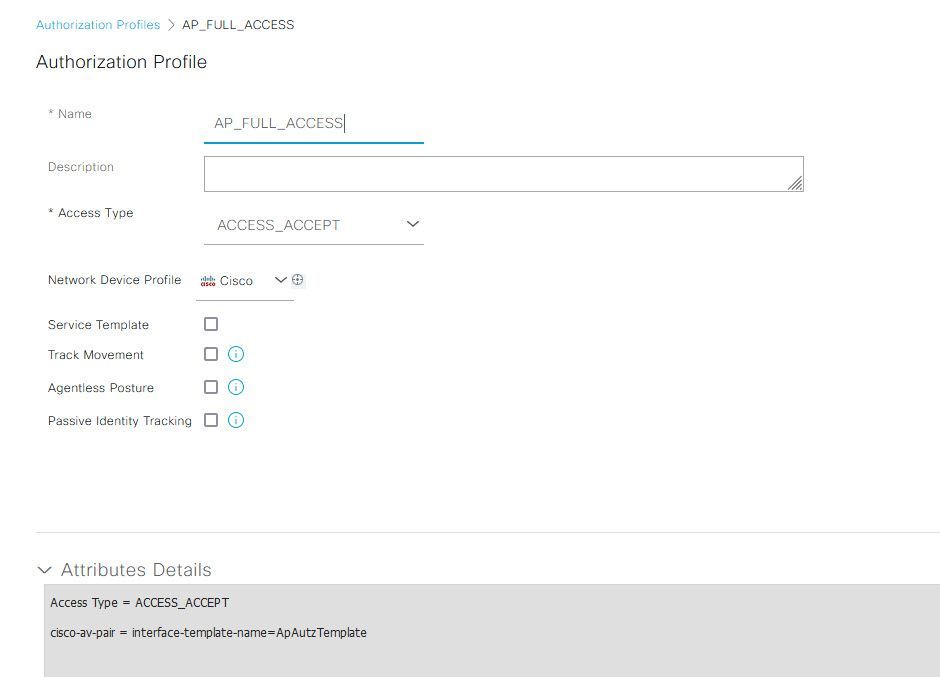
- Authorization Profile for Full Access: The corresponding authorization profile specifies an interface template that grants full access to the network. Once full access is granted, the access point (AP) is able to initiate the Control and Provisioning of Wireless Access Points (CAPWAP) session with the Wireless LAN Controller (WLC)..
It is important to ensure that these policies are correctly ordered and configured in Cisco ISE to provide a seamless transition from limited to full access for the APs as they come online.
An access point initially undergoes MAC Authentication Bypass (MAB) authentication on the switchport:

After the completion of the Plug and Play (PnP) process, the access point reboots and initiates 802.1X authentication with the switchport:

Credential Lifecycle Management:
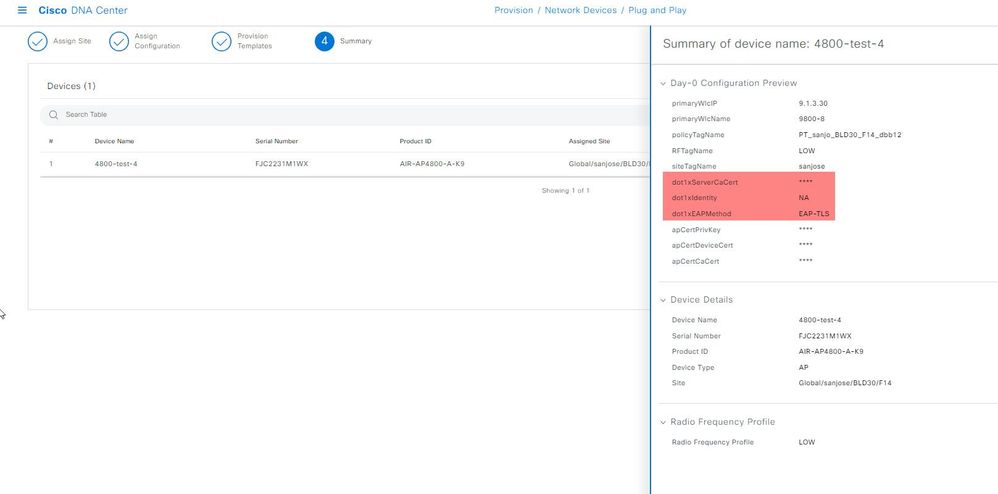
In instances where an administrator decides to update the credentials—such as a username and password—the access point is required to undergo a Day-0 workflow to be assigned new credentials for authentication. To initiate the Day-0 workflow, the access point must be factory reset through the Wireless LAN Controller.
Similarly, when a certificate is utilized for authentication, as in the case of EAP-TLS, the access point must also engage in a Day-0 workflow to refresh its certificate. The distinction with certificate-based authentication is that the access point is programmed to automatically perform a factory reset upon reloading after certificate expiry. Upon booting up, the access point will verify the certificate's validity. If it detects that the certificate has expired, it will disregard its current configuration and revert to factory default settings. If there is a need to issue a new certificate to an access point before the existing one expires, a script can be employed to reset the access point to its factory defaults.
For those interested in automating this process, a sample script for resetting an access point can be found in the following GitHub repository: SecureAP_cert_renewal.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: