- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Cisco Router C891F IKEv2 Site-to-Site Setup
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Router C891F IKEv2 Site-to-Site Setup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 10:08 AM
I have recently taken over a site that utilizes a Cisco Router to act as their public facing device/firewall. I have been tasked with setting up a IKEv2 S2S tunnel with one of our external vendors, and it will need to be setup on this router.
I have watched a few videos and read through many articles to attempt to set up the connection, but as soon as I applied it to the WAN interface, I brought the site down. I have reverted this change, but I am stuck on where I went wrong.
The site I am connecting to uses the following setting to information on their side of the tunnel.
remote Public IP:
1.1.1.1
Local Public IP:
2.2.2.2
Pre-Shared Keys:
SharedKey123
Protocol - IKEv2
Phase 1:
Encryption: aes-256
Auth: sha256
dh group: group 20,21,19,14 (can take any of these)
lifetime: (24 hours)
Phase 2:
Protocol: ESP
Encryption: aes-256
Auth: sha256
dh group: no pfs
lifetime: 4 hours
The commands I used on the router to try and set up our end of the connection is as follows. Things were good until I applied the crypto map to the Interface (last command).
crypto ikev2 keyring keyring-tickets
peer tickets
address 1.1.1.1
pre-shared-key local SharedKey123
pre-shared-key remote SharedKey123
crypto ikev2 proposal proposal-tickets
encryption aes-cbc-256
integrity sha256
group 14
crypto ikev2 profile profile-tickets
match identity remote address 1.1.1.1 255.255.255.255
identity local address 2.2.2.2
authentication remote pre-share
authentication local pre-share
keyring local keyring-tickets
crypto ikev2 policy policy-tickets
proposal proposal-tickets
crypto ipsec transform-set trans-tickets esp-aes 256 esp-sha256-hmac
mode tunnel
ip access-list extended acl-tickets
permit ip any any
crypto map map-tickets 10 ipsec-isakmp
set peer 1.1.1.1
set transform-set trans-tickets
set ikev2-profile profile-tickets
match address acl-tickets
interface gigabitEthernet 8
crypto map map-tickets
What am I missing here? First time managing a Cisco router, so I am learning as I go, unfortunately on a production environment.
Thanks!
- Labels:
-
Other Routers
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 10:22 AM
The config is correct
Did you ping from Lan to Lan?
Also I am sure you config the ACL but I need confirmation
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 10:32 AM
I did not have the chance to ping LAN to LAN. I work remote, and applying the Crypto Map to the interface dropped my connection to the environment. Calling the site, I found internet access to the entire environment went down.
I ended up having an on site user, reboot the router to revert the changes to bring them back online.
What do you mean by config the ACL?
If it helps any, the config to the WAN port I added to the Crypto Map too is the following (before I applied the Crypto Map):
interface GigabitEthernet8
ip address 2.2.2.2 255.255.255.248
ip access-group FIREWALL_ACL in
ip flow ingress
ip nat outside
ip inspect FIREWALL_INSPECT out
ip virtual-reassembly in
duplex auto
speed auto
no cdp enable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 10:35 AM
The config for interface explain the issue of Ipsec VPN, I will check some note and answer you max tomorrow
Thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 02:18 PM
##For Ipsec VPN I see you use any any this wrong change it to allow local-lan to remote-lan
##interface GigabitEthernet8
ip address 2.2.2.2 255.255.255.248
ip access-group FIREWALL_ACL in<-this need to included
Udp 500
Udp 4500
Esp
Udp 50
These four port need for Ipsec VPN
ip flow ingress
ip nat outside <-you use NAT overload so you need to excluded the traffic from local Lan to remote Lan in acl of NAT using deny IP local-lan remote-lan
ip inspect FIREWALL_INSPECT out<-this inspect if it include any rule deny traffic to remote Lan remove it
ip virtual-reassembly in
duplex auto
speed auto
no cdp enable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 12:38 PM
@IWSup your crypto ACL acl-tickets that defines the interesting traffic to encrypt is matching on all/any traffic, so if the tunnel established it would want to encrypt and tunnel all traffic to the peer.
ip access-list extended acl-tickets
permit ip any any
You'd want to amend the acl-tickets ACL to explictly specify which traffic should be tunneled to the peer, not any. This ACL would need to be mirrored on the peer side.
Example:
ip access-list extended 101
permit ip 10.10.3.0 0.0.0.255 192.168.8.0 0.0.3.255
Also check the ACL FIREWALL_ACL permits IPSec traffic (udp/500, esp and possibly udp/4500, if NAT between peers) from the peer IP, in order to establish a tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 01:50 PM - edited 03-27-2024 02:16 PM
@Rob IngramThanks for the information, that makes sense. So the IP access list should only define the LAN to LAN traffic from each side of the VPN tunnel?
ip access-list extended 101
permit ip LocalLAN Subnet RemoteLAN Subnet
Regarding the Firewall_ACL, I am not seeing those on the list. Would I want something along the following lines added to the Fireawall_ACL?
Permit udp host 1.1.1.1 host 2.2.2.2 eq 500
Permit udp host 1.1.1.1 host 2.2.2.2 eq 4500
Is there a need to define a destination, or would the following be better?
Permit udp host 1.1.1.1 any eq 500
Permit udp host 1.1.1.1 any eq 4500Note, there appears to be a "permit esp any any" already in place, so we should be good there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 02:00 PM
@IWSup yes, correct for the crypto ACL.
For the inbound Firewall_ACL is NAT used between the path between you and the peer? If no then you need to permit ESP instead of NAT-T udp/4500. If NAT is used then you need NAT-T.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 02:24 PM
@IWSup I note you've edited your post since my last response.
Ideally you should permit from the trusted source(s) IP address to the Gi8 IP address. If permit ESP any any is already in place that will work, but you are obviously allowing from all sources. If you only allow VPNs from a couple of networks you could restrict this to known/trusted IP addresses, more secure and less noise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 03:07 PM - edited 03-27-2024 03:08 PM
Appreciate the information. I am currently waiting to hear back from my external vendor on their Internal IP and if NAT will end up being needed, so I can get the ACLs properly setup. Planning to make the changes in the morning once I get the information.
If NAT is not used on either side, it's port 500 and ESP?
If NAT is needed by one side or the other, it's Port 4050 and ESP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 03:13 PM - edited 03-27-2024 03:20 PM
@IWSup almost correct....
If there is NAT in between you and the peer you will need udp/500 and udp/4500. ESP cannot be translated and is encapsulated inside udp/4500.
If there is NO NAT between you and the peer then you need udp/500 and ESP.
Here is an example to secure IPSec VPN, which maybe of help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 10:38 AM
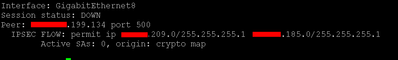
Quick update, I was able to get the tunnel applied without brining down the site with the above information. Really appreciate all the help. However, the tunnel is showing DOWN, and I was just informed I will need to implement a NAT on our side of the tunnel, so all traffic leaving the internal network will show as a single IP they just gave me.
Working on trying to sort out how to go about that currently. However, I do not think whether a NAT is properly setup or not will affect whether the tunnel is up or not, just for routing and connectivity purposes through the tunnel.
Hunting down some debug commands to see what information I can gleam from them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 03:35 PM
Friend open udp 4500 not depend on if you use NAT in router in both sides, the udp 4500 is use if any router behind NAT device.
We usually open above ports, you can tune acl for these ports by using host <ip of peer you use in crypto map> in acl.
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide