Umbrella offers a broad set of security functions that until now required separate firewall, web gateway, threat intelligence, and cloud access security broker (CASB) solutions.
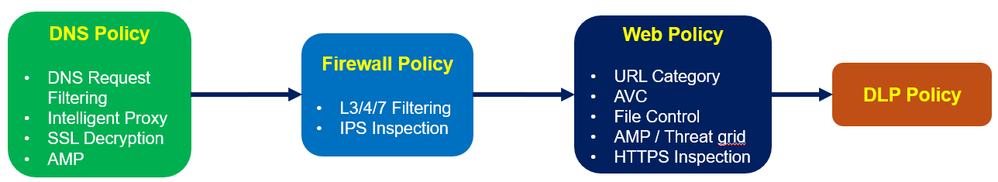
Umbrella DNS is resolved first. It is the first check for malicious or unwanted domains and is based on the defined DNS policies. This reduces the quantity of traffic that is sent to the CDFW and SWG, improving responsiveness and performance
All traffic that has made it through DNS checks will be inspected by the CDFW. The firewall provides visibility and control for outbound internet traffic across all ports and protocols (L3/L4) as well as L7
The SWG will inspect any traffic that is destined for 80/443 after it has been permitted by the CDFW to provide a deeper security inspection. It will also apply application, visibility and control policies.
Umbrella’s cloud access security broker (CASB) detects and reports on cloud applications in use across your environment while Umbrella data loss prevention (DLP) analyzes sensitive data to provide visibility and control over sensitive data to avoid data exfiltration.
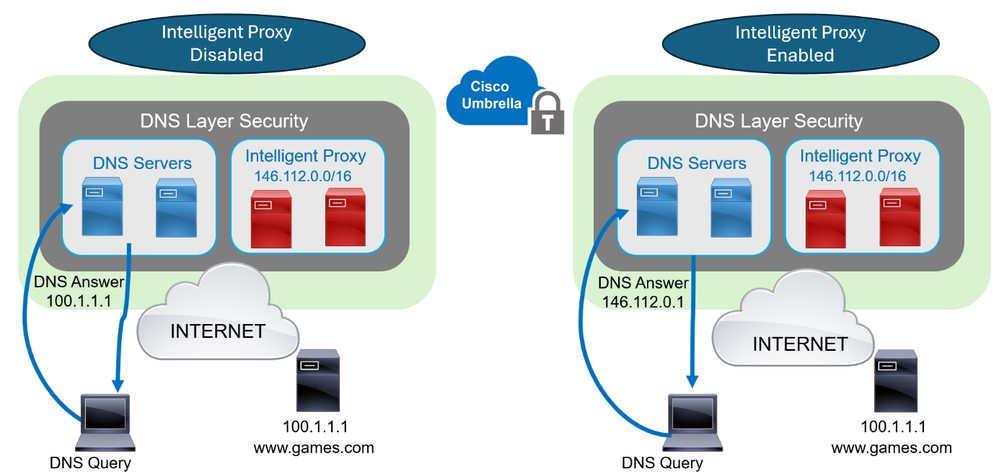
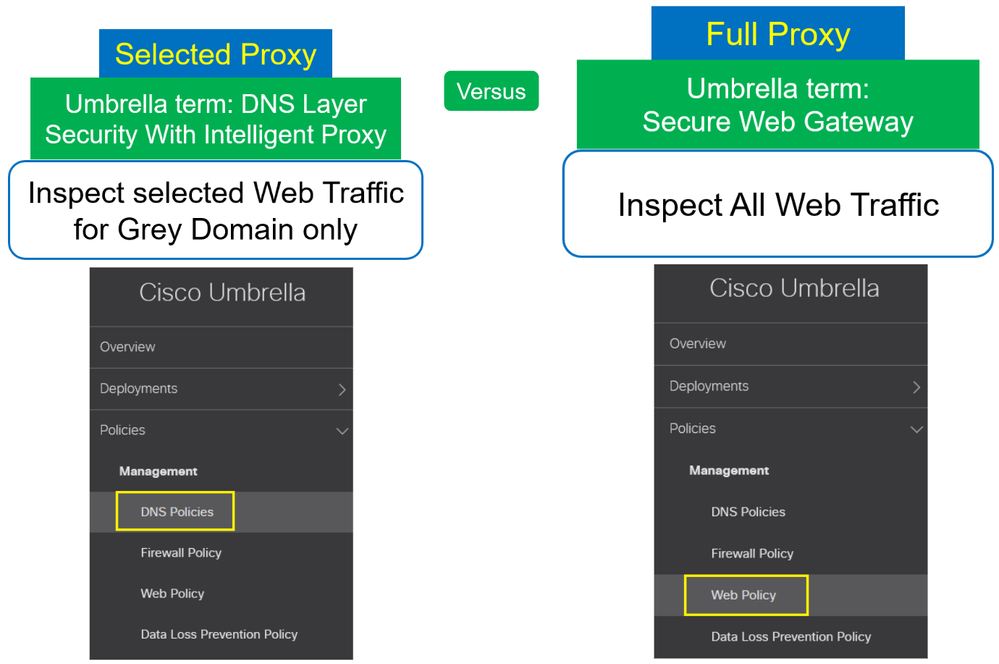
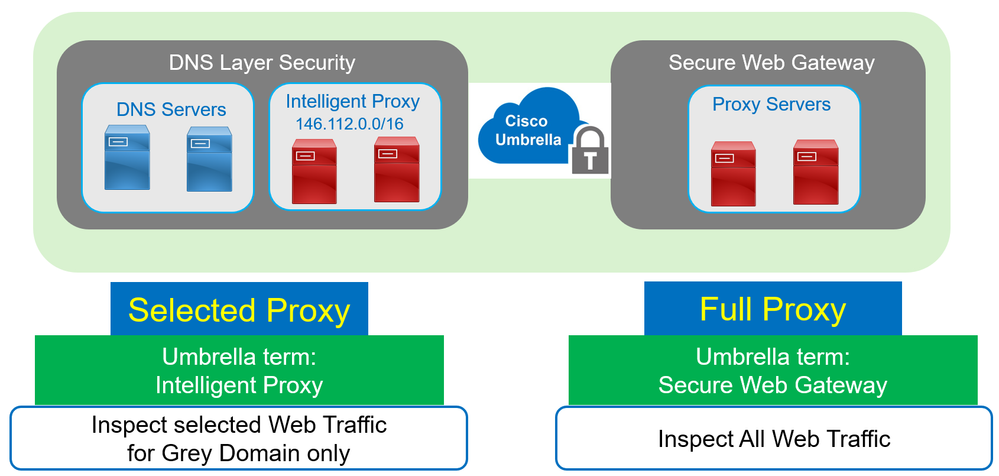
Unlike proxying all web traffic, Cisco Umbrella DNS-Layer protection use “selective” proxy mechanism to intercepts the web traffic, in Cisco Umbrella terms this feature is called “Intelligent” proxy.
Umbrella classify all domains into three category – Good, Bad and Grey.
Umbrella’s intelligence is able to determine what gets proxied; thus, not all traffic is proxied.
- Domains that are bad: those are stopped immediately by Umbrella at the DNS Layer.
- Domains that are good: Cisco Umbrella returns the ip address of the legimate website and never proxied.
- Domains that are on the grey list and present a risk: Cisco Umbrella returns the IP address of the Intelligent Proxy, Umbrella cloud proxy servers uses the ip address in the range 146.112.0.0/16.
To summarize, Cisco Umbrella DNS Layer Security with Intelligent Proxy is called Selective Proxy. Because proxying or not web traffic is done automatically based on the reputation of the domain (Good and Bad not proxied, Grey is proxied). This is why we call it Selected Proxy.
Unlike with Selective Proxy using Intelligent Proxy at the DNS Layer. Cisco Umbrella includes a new layer of security called Secure Web Gateway or SWG. This component provides a Full Proxy of all web traffic. SWG is your Web Security Appliance in Cisco Umbrella. Unlike with Intelligent Proxy feature at the DNS Layer Security, Secure Web Gateway provides additional security such as :
- Threat Grid sanboxing
- Application Visibility Control
- Granular logs Web Transaction and
- File Type Control
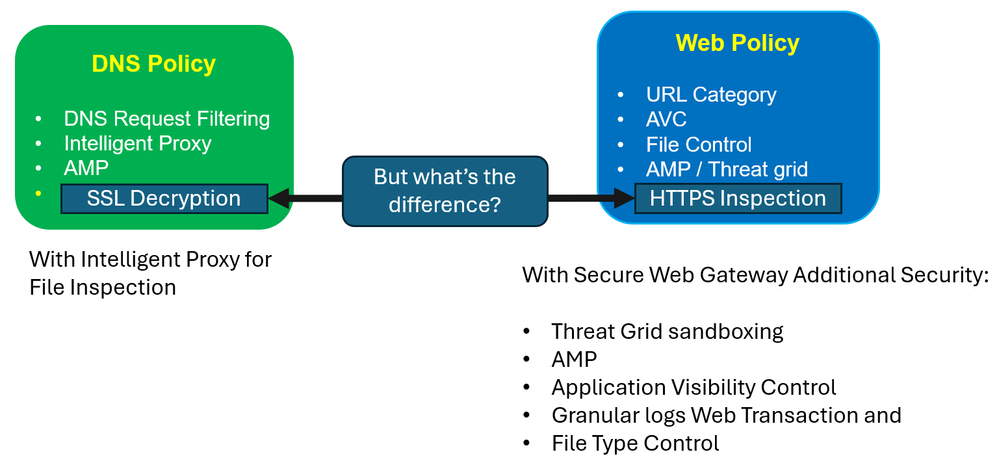
DNS Layer Security is implemented using DNS Policies and you can decide to enable or not Intelligent Proxy in each policy.
Secure Web Gateway is implemented using Web Policy.
Traffic forwards to Umbrella from networks, IPsec tunnels, network devices, and client connectors and forwarders. Umbrella represents a network entity, user, or group as an identity in an Umbrella policy. Umbrella policy settings apply to an identity and a destination.
When Umbrella receives a destination request from an identity, Umbrella applies the enabled DNS policies to the destination. If the Umbrella DNS-layer security does not block the destination, Umbrella forwards web traffic to the cloud-delivered firewall and the secure web gateway. If HTTPS inspection is enabled on the web policy, the DLP policy monitors and blocks sensitive data transmission in outbound web traffic.
The following diagram displays how traffic flows from network entities and client connectors through Umbrella.
How packet is processed
- Upon receiving a DNS request, Umbrella matches an enabled DNS policy to an identity and destination. The DNS-layer security applies the action defined in the DNS policy.
- If you enable a Firewall policy, Umbrella forwards any requests allowed by the DNS-layer security to the cloud-delivered firewall. The Umbrella cloud-delivered firewall either filters the request or forwards the web traffic on port 80 or 443 to the secure web gateway (SWG).
- If you enable a web policy, the Umbrella secure web gateway (SWG) evaluates web traffic on ports 80 and 443 and applies the actions defined in the web policy.
- If you enable HTTPS inspection in the web policy, the DLP policy monitors and optionally blocks sensitive data detected in outbound web traffic.
- Next, allowed traffic egresses through Network Address Translation (NAT).