The firewall uses a certificate with the role of CA Certificate of Authority to perform SSL Decryption for outbound traffic.
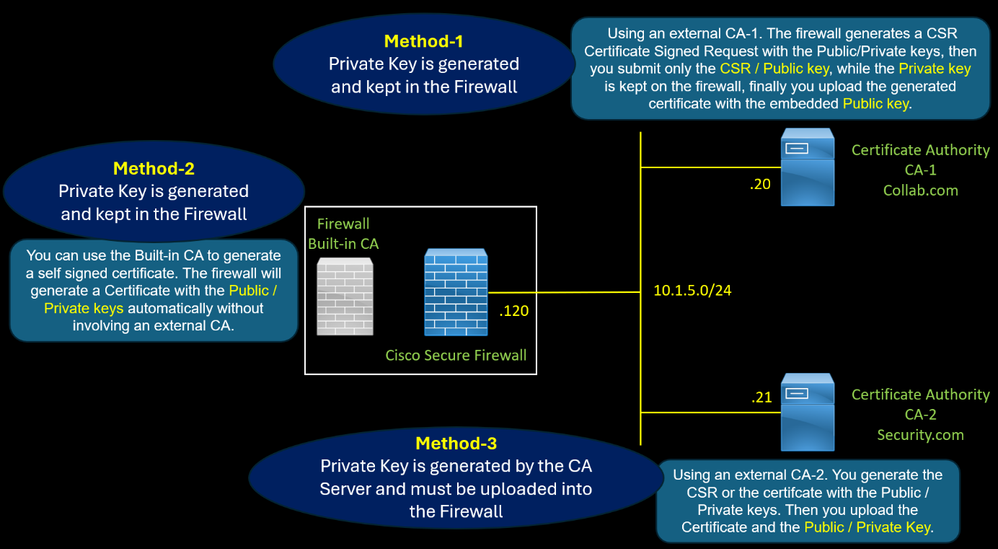
There are three methods to generate this certificate.
- Method 2 : Using an external CA. The firewall generates a CSR Certificate Signed Request with the Public/Private keys, then you submit only the CSR / Public key, while the Private key is kept on the firewall, finally you upload the generate certificate with the embedded Public key.
- Method 1 : You can use a self-signed certificate. The firewall will generate a Certificate with the Public / Private keys automatically without involving an external CA.
- Method 3 : Using an external CA. You generate the CSR or the certifcate with the Public / Private keys. Then you upload the Certificate with the Public / Private Key.
Method 1
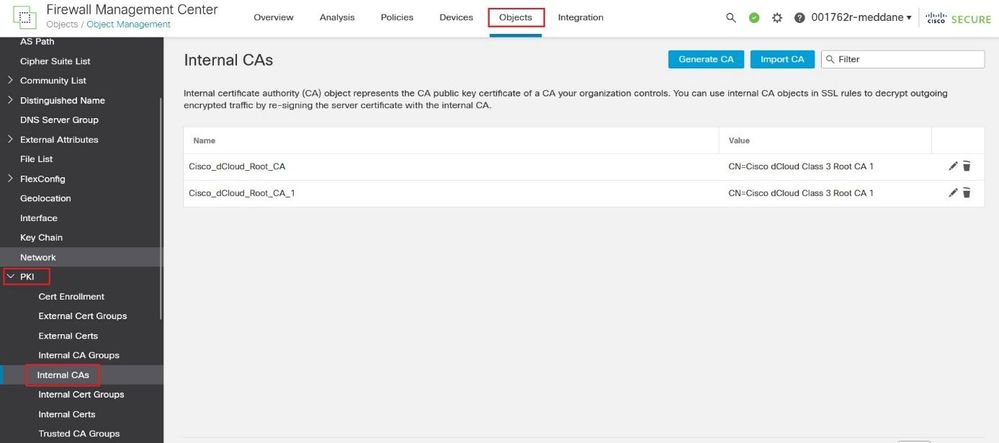
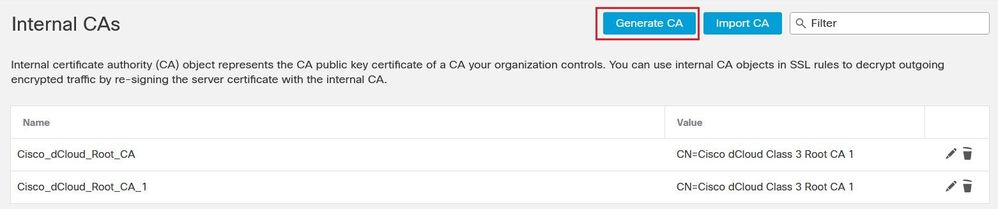
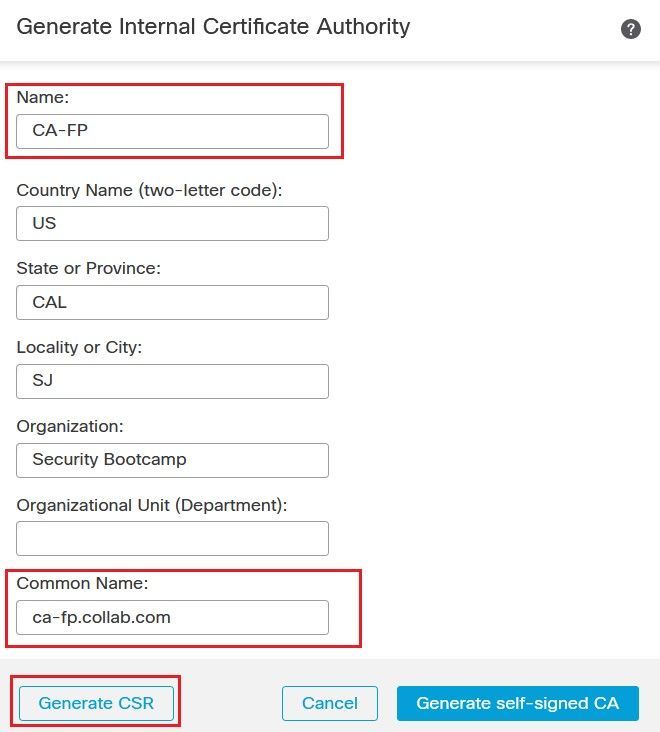
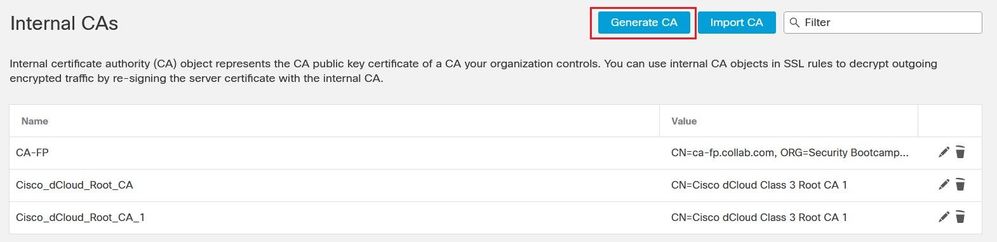
Navigate to Objects > Internal CAs. Click the Generate CA button to generate a Certificate Signing Request CSR.
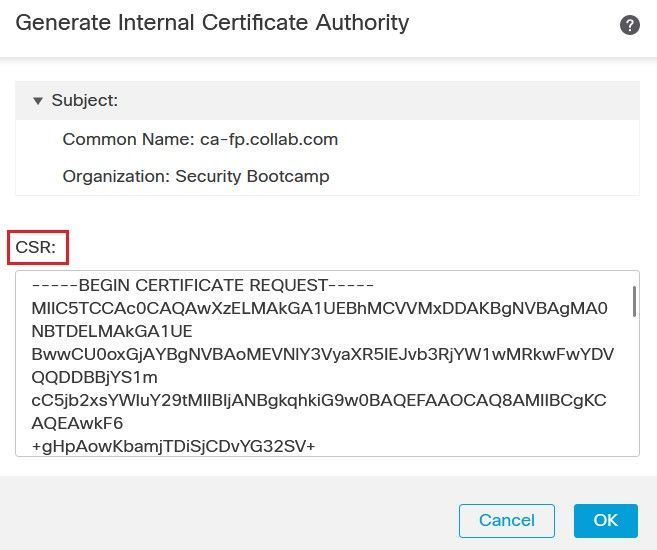
Populate the required field such the Common Name then click the Generate CSR button.
The CSR contains only the Public key, the Private key is kept in the firewall.
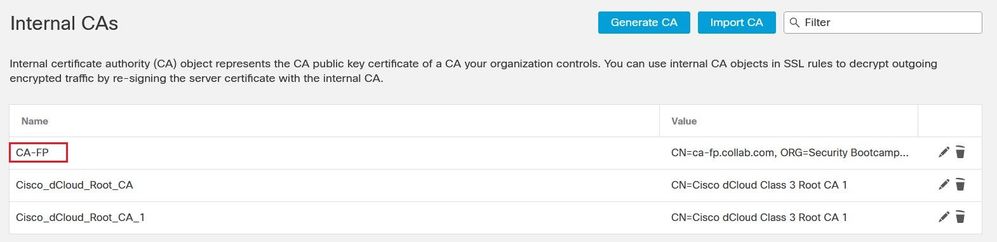
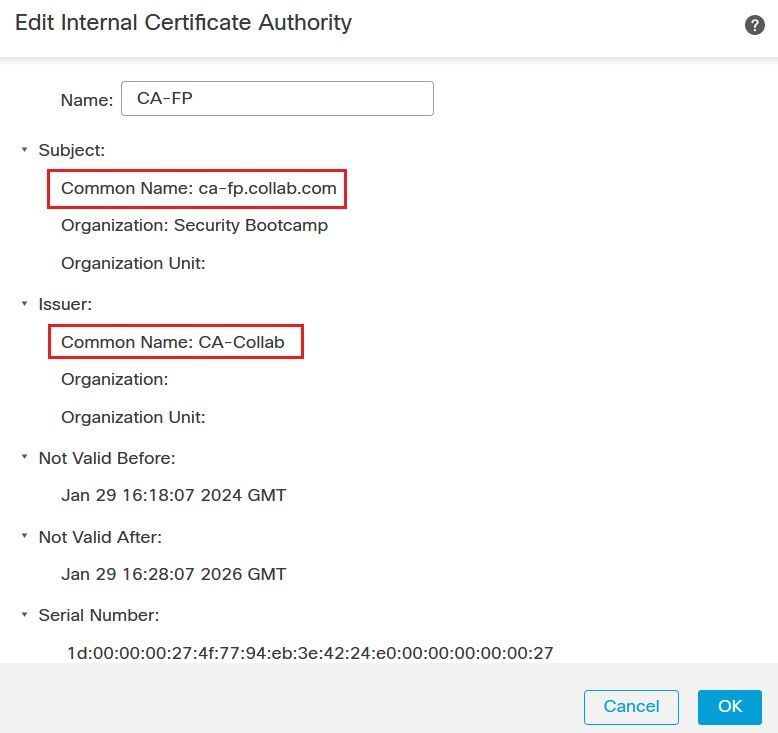
Access the CA-1 server, and submit the CSR, you need to select the Certificate Template Subordinate Certificate Authority to make this certificate as a CA so that the firewall can use it to sign the spoofed server certificate.
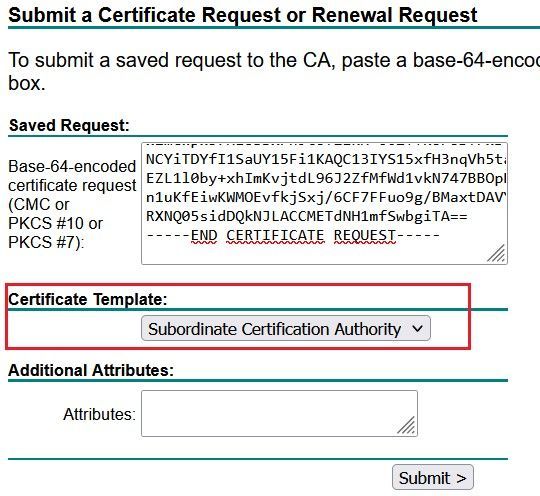
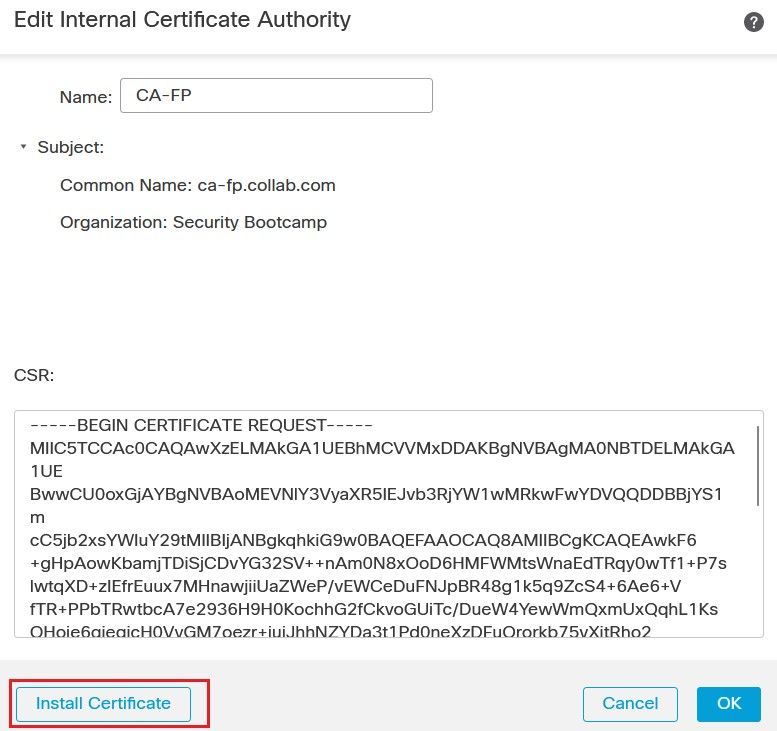
Retrieve the generated certificate from the CA-1 server. On the FMC GUI, edit the CSR and click Install Certificate button, then use the Browse button to upload the certificate.
Method 2
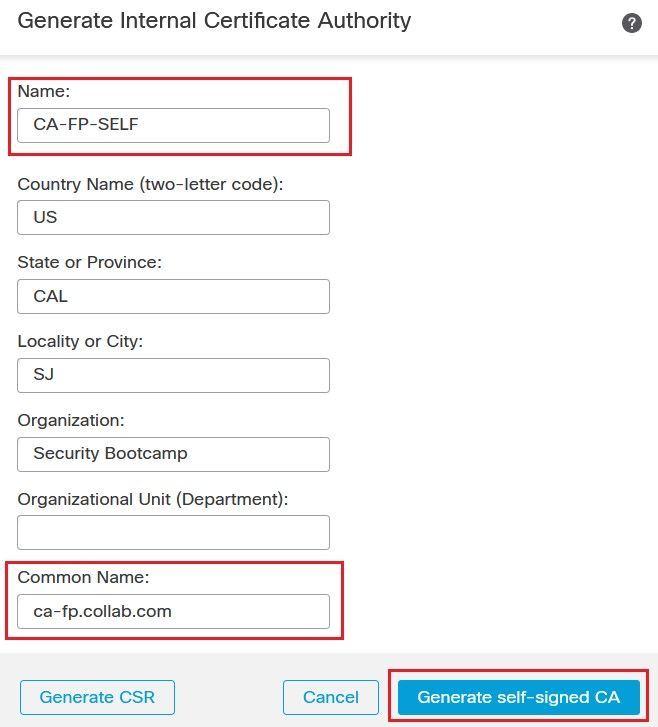
Generate a Self Signed Certificate, Click the Generate CA button, populate the required field such as the Common Name, then click on the Generate self-signed CA button. A certificate with role CA is generated automatically.
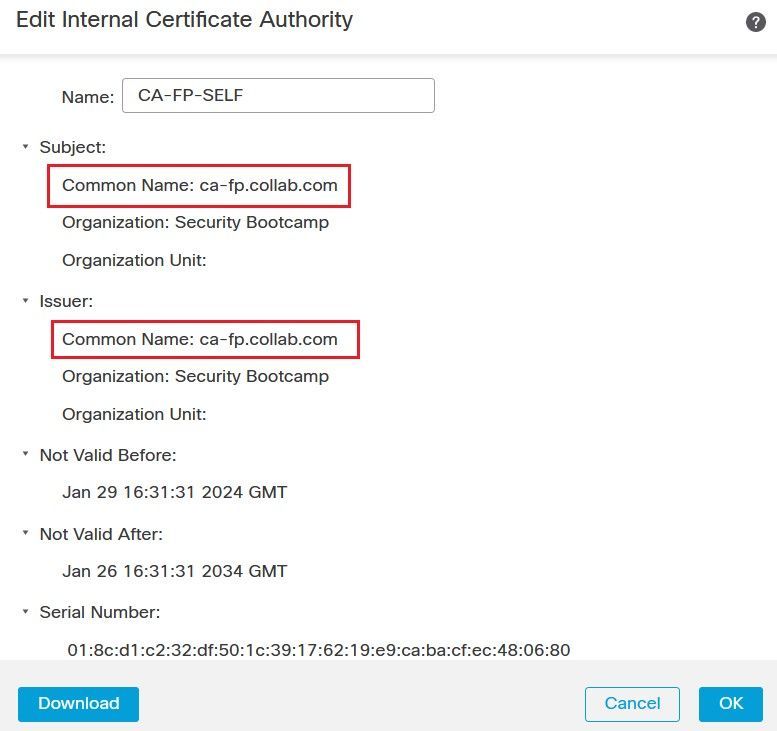
Method 3
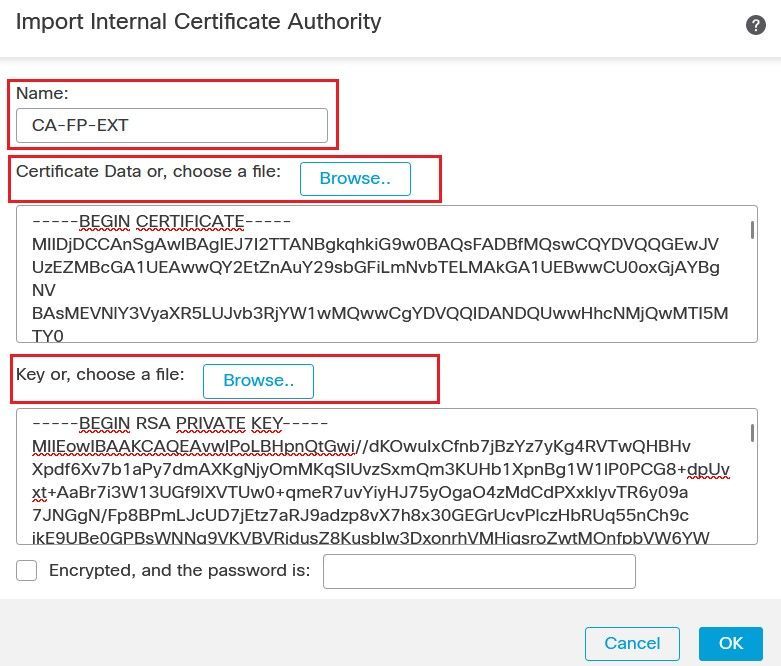
Access the CA-2 server command line, generate a certificate with the role CA. The CA-2 server generates the certificate including the public key and the Private key. With this method, you need to import both the certificate and the Private key into the firewall.
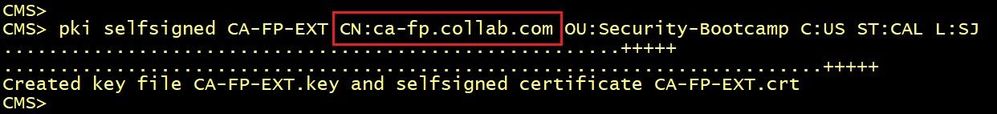
Retrieves the Certifcate and the Private key as shown below.
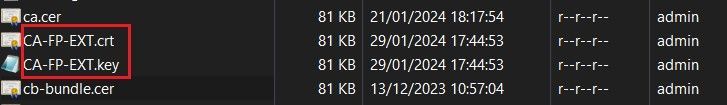
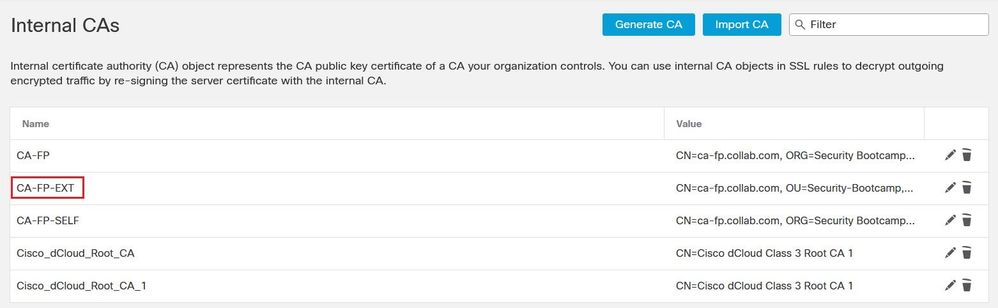
Click the Internal CA button. Upload the Certificate and the Private key files.
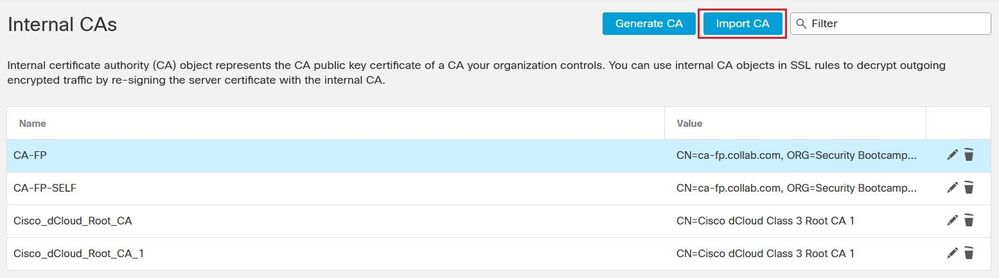
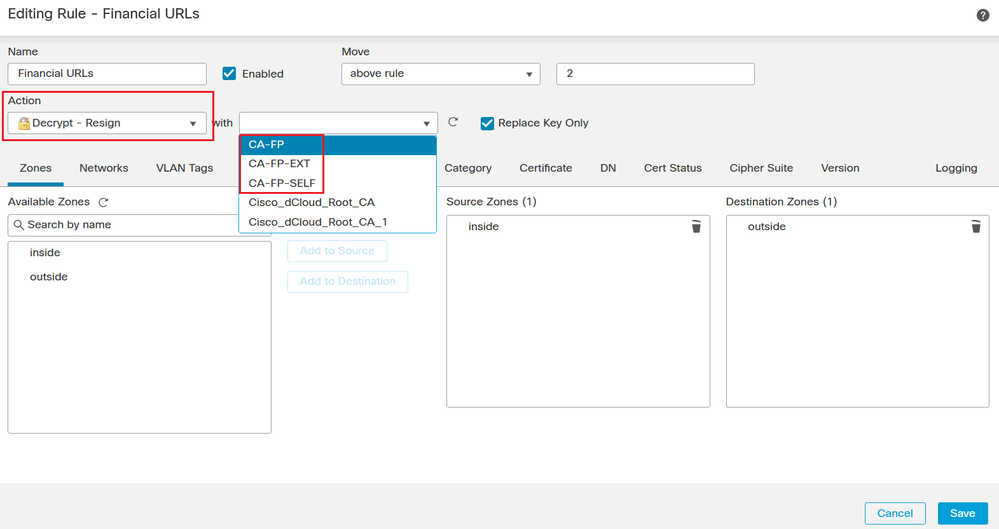
Now you can use an SSL Decryption Policy Rule with Decrypt-Resign and you can specify which Certificate the firewall will use to re-sign the spoofed certificate of the target internet server.