In June we have had new additions to our growing list of Machine-Learning-powered Confirmed Threat detections provided by the Cognitive Intelligence engine. Thanks to the improvement made to our Machine Learning backend (see Machine Learning Backend Improved blog) we have added 9 net-new Confirmed Threat types (see list below) and increased detection rates for the previously existing Confirmed Threats in the past six months.
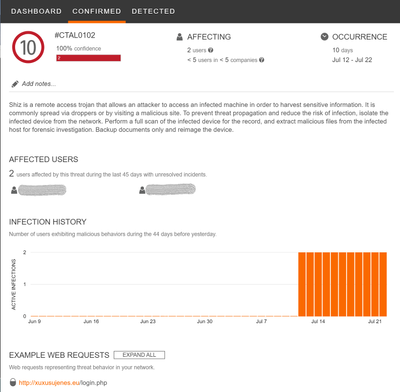 Example of Shiz remote access trojan recently detected in monitored network
Example of Shiz remote access trojan recently detected in monitored network
Newly Added Confirmed Threats
| Confirmed Threat ID |
Name |
Category |
Risk |
Description |
| CTAL0102 |
Shiz |
information stealer |
Critical |
Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. |
| CTAL0143 |
Vigorf |
information stealer |
High |
Vigorf trojan capable to establish a proxy server and steal sensitive information on a victim's computer. |
| CTAL0088 |
Mikey trojan |
trojan |
High |
Mikey is a trojan that installs itself on the system, collects information and communicates with a C2 server, potentially exfiltrating sensitive information. |
| CTAL0090 |
Spora ransomware |
ransomware |
High |
Spora encryps files, does not add any specific extensions. It also deletes volume shadow copy to avoid system restore point. It installs a startup link and modifies Internet Explorer proxies, also creates a html file with a dynamic filename. |
| CTAL0128 |
Bublik |
malware distribution |
High |
Bublik is a downloader that targets Windows hosts. Although it's primarily used as malware to distribute various banking trojans, it's also capable of extracting and exfiltrating sensitive information from the host. |
| CTAL0110 |
DNS Changer |
information stealer |
High |
DNS Changer modifies the DNS registry entries in Windows devices in order to replace the name servers on the host. The Trojan has backdoor functionality and, by bypassing Windows Powershell restrictions, can execute arbitrary commands on the infected device |
| CTAL0089 |
Neurevt |
information stealer |
High |
Neurevt or Beta Bot botnet. Beta Bot is a modular malware with diverse capabilities. Beta Bot can perform DDoS attacks, steal information, perform DNS blocking and redirection, send spam through Skype, and spread itself like a worm through removable USB devices. Threat can disable existing anti-virus solutions and is able to escalate privileges through social engineering methods. |
| CTAL0119 |
Coin miner variant |
cryptocurrency miner |
High |
Threat is being distributed through a Trojan downloader, that infects a computer to mine for Monero currency. It targets systems with high computational power, taking advantage of these capabilities to mine cryptocurrency. |
| CTAL0109 |
Nymaim |
malware distribution |
High |
Nymaim can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control domains to connect to additional payloads. |
Confirmed Threat Updates
Note that our newly introduced semi-automatic Indicator-of-Compromise (IoC) hunt processes (see Machine Learning Backend Improved blog) allowed us to increase the IoC coverage of existing Confirmed Threats. In June 2019 we added more than 1445 High risk IoCs and 160 Mid risk IoCs, covering 40+ different Confirmed Threat types. In particular, more than hundred IoCs have been added to each of the following Confirmed Threats: Razy trojan (high risk), Suppobox information stealer (high risk), Ramnit banking trojan (high risk).
