- Cisco Community
- Technology and Support
- Security
- Security Blogs
- Securely Connecting Your Industrial Networks: A Companion to DLBTEC-54
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
Virtually every industry is looking to transform digitally. Why? The answer is simple: because digital transformation enables data driven decisions and every decision that’s driven by data is better than one that isn’t. If a manufacturer wants to increase production, the method can be found in the data. If a shipper wants to increase efficiency, the path can be found in the data. If a refiner wants to increase safety, the solution is to be found in the data. However, finding these insights in the data means first gathering the data, then analyzing the data, and then applying machine-learning to the data. A well-proven formula for gathering data is to converge all endpoints onto a single IP network.
However, in industrial networks, the data often originates in difficult-to-reach places. For example, data may be found in solar farms in the middle of deserts, where excessive heat can melt ordinary networking equipment. Alternatively, it may be found in frozen wastelands where the bitter cold may prevent typical electronic systems from even booting up. Or perhaps it may be found in seaports where moisture and salt-fog enjoy eroding electronic circuits as a pastime. Or perhaps it may be found in large open-pit mines where thick dust can clog up the fans needed to cool electronic systems within mere minutes. Or perhaps it may be found in manufacturing plant floors where shock, vibration and electromagnetic interference are commonplace. Or perhaps it may be found in refineries where the slightest spark caused by electronic equipment could cause a dangerous explosion to occur.
Given these challenges common in industrial networks, how can this data to be efficiently gathered, so that it can be analyzed, and insights gleaned from it?
Beyond environmental challenges, there is the critical challenge of securing the industrial network. Consider the impact that just a few recent cyber attacks have had on industrial operations:
- June 27, 2017: Pharmaceutical giant rocked by $1.3B ransomware attack
- August 17, 2017: Cyberattack cost shipping giant as much as $300 million and disrupted operations for 2 weeks
- September 20, 2017: Leading Overnight Shipper Cuts Profit Forecast on 300 Million Hit from Cyberattack
- March 18, 2018: Cyber Attack on Saudi Plant Designed to Cause Explosion
- March 19, 2019: $75M Targeted Attack on Operations Shuts Down One of the World’s Biggest Aluminum Producers
- December 30, 2019: Ransomware shuts down US maritime facility
- January 10, 2020: Bahraini oil company reportedly attacked by new ‘Dustman’ disk wiper
- March 5, 2020: Steel maker’s North American operations are down after a ransomware infection
As can be seen by these headlines, when cyber attacks disrupt operations, the cost can be in the tens-of-millions—if not hundreds-of-millions—of dollars. Additionally, it bears mentioning that not all of these attacks were incidental infections of malware; but rather, some of these attacks were very deliberately targeted against operations (case in point the March 2019 attack on one of the world’s largest suppliers of aluminum). Another disturbing new reality is that the intent of these attacks is not always to cost companies money, but some have a far more serious and sinister intent, such as causing physical damage (case in point, the March 2018 attack against a Saudi oil plant that was designed to cause an explosion).
As such, the need to securely connect industrial networks is a very relevant and top-of-mind concern spanning across all industry verticals. But how is this to be done? Cisco offers a three-part answer to this challenge, by presenting our customers a proven technology stack to meet these requirements:
- Start with the right hardware
- Use the right software
- Leverage architectural integrations
Let’s examine each of these elements in turn.
Start with the Right Hardware
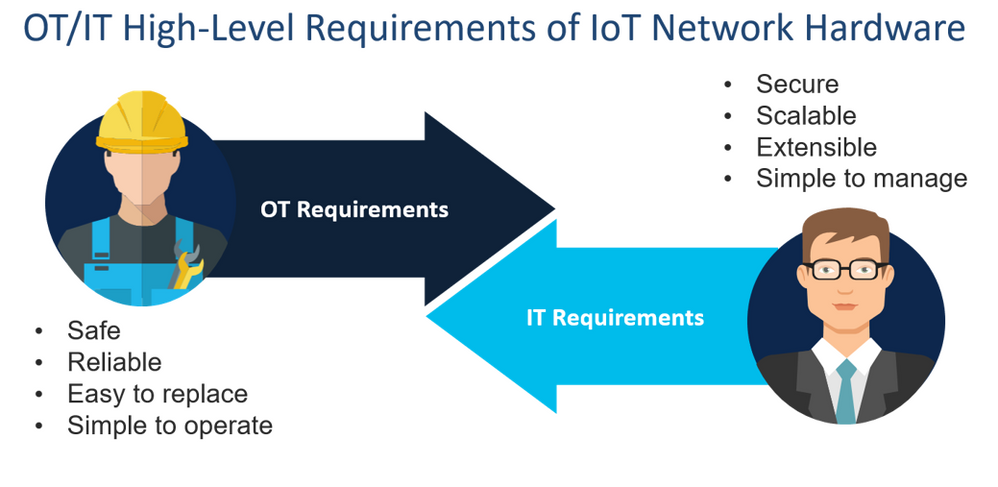
When it comes to industrial hardware requirements, it is important to recognize that there are two key personas whose demands must be met:
- Operational Technology (OT)—responsible for the operations of the company, such as manufacturing the cars, digging the mines, delivering the power or refining the oil, etc.
- Informational Technology (IT)—responsible for supporting OT personnel in their operations and for securing the networks while gathering, analyzing and learning from the data
These two personals have very different priorities and concerns. For example, OT priorities focus on employee safety, production output and efficiency, equipment reliability, and operational simplicity; whereas IT priorities may focus instead on network security and scalability, extensibility and management simplicity.
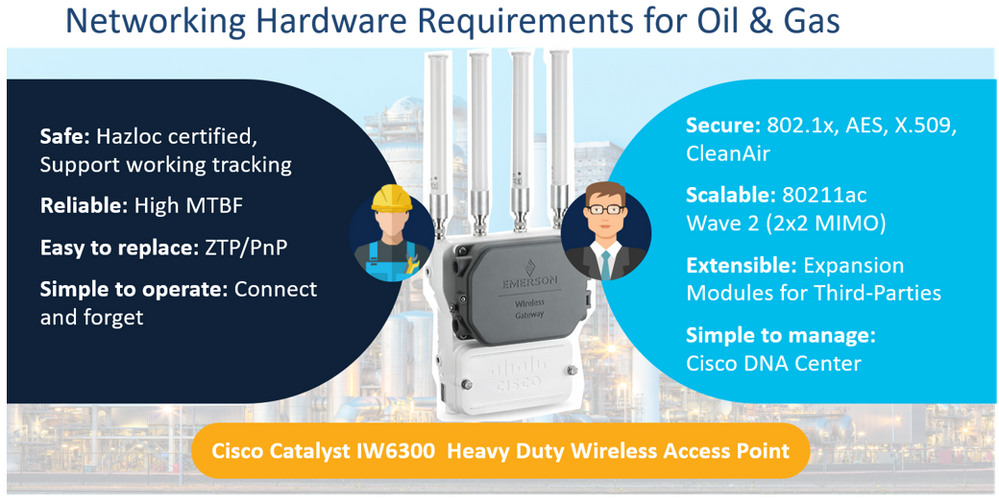
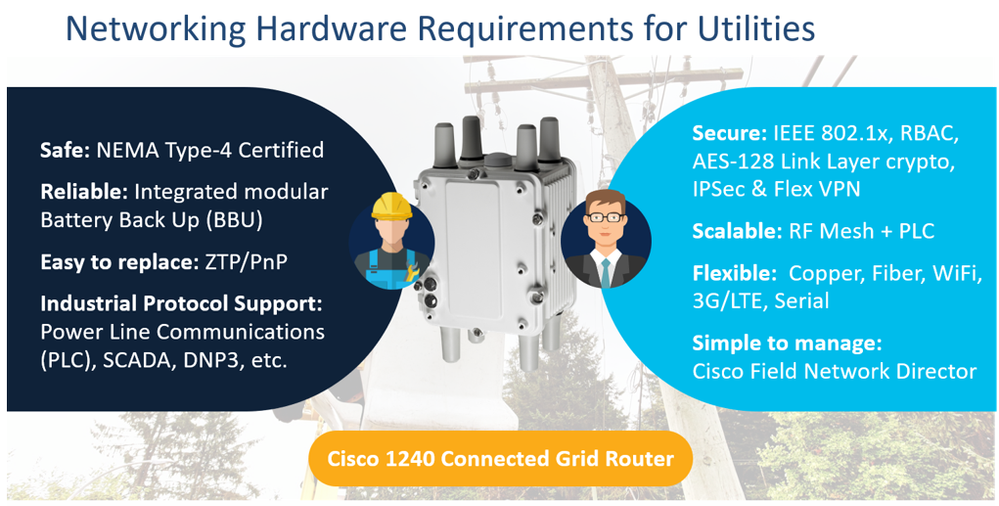
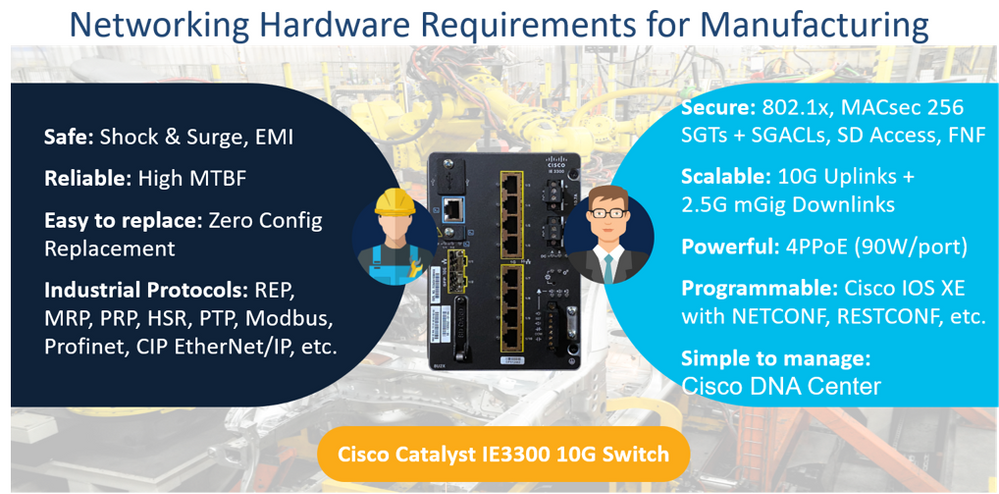
As such, these priorities of these respective personas result in diverse feature requirements placed on the networking hardware to be found in these environments, as shown in the following figures.
Specific to security, there are certain features that need to be delivered in hardware. For example, to ensure secure communications over Ethernet links, MACsec 256 link-layer encryption may be used; however, to deploy this functionality at Gigabit, Multi-Gigabit or even 10 Gigabit speeds requires dedicated hardware in Cisco Industrial Ethernet (IE) switches. Similarly, efficiently delivering IPSec encryption at scale in Cisco Industrialized Routers (IR) requires hardware-acceleration. And finally, ensuring that the software running on these network devices has not been tampered with requires a hardware trust anchor, such as the anti-theft, anti-counterfeiting and anti-tamper chip that is embedded deep within Cisco IE/IR network devices to provide these with an immutable identity (with an IEEE 802.1 AR Secure UDI X.509 Certificate), as well as secure storage for certificates and objects, and certifiable entropy for Random Number Generation (RNG).
Use the Right Software—Part 1: Cisco IOS XE
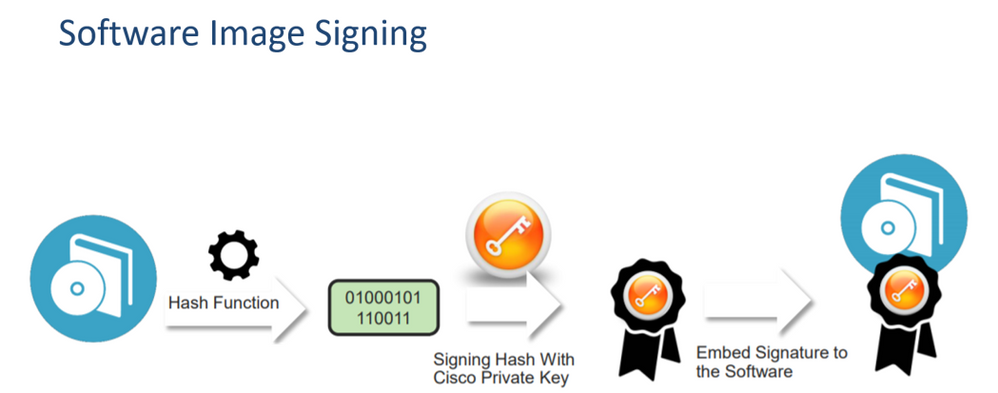
Before we can activate software features to implement network security functions, we must ensure that the software itself is secure and has not been tampered with. Therefore, to build on the Trustworthy Systems foundation laid by the hardware trust anchor, Cisco digitally signs and verifies their software images to ensure the integrity of these.
The Software Image Signing process is done by performing a hash of the final software image binary file and then encrypting this hash with Cisco’s private key, producing a digital signature. This digital signature is then embedded within the software itself.
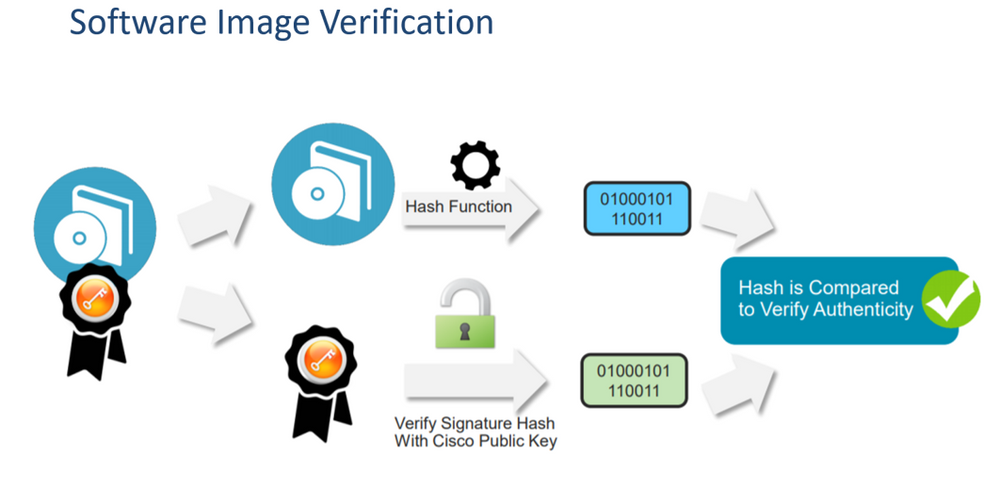
Then, when a device begins its Secure Boot Process, the it will:
- Independently compute a hash on the binary file, and
- Decrypt the digital signature with Cisco’s public key to reveal the hash computed by Cisco
If the result of these operations is identical, then this proves that the software is authentic and has not be tampered with.
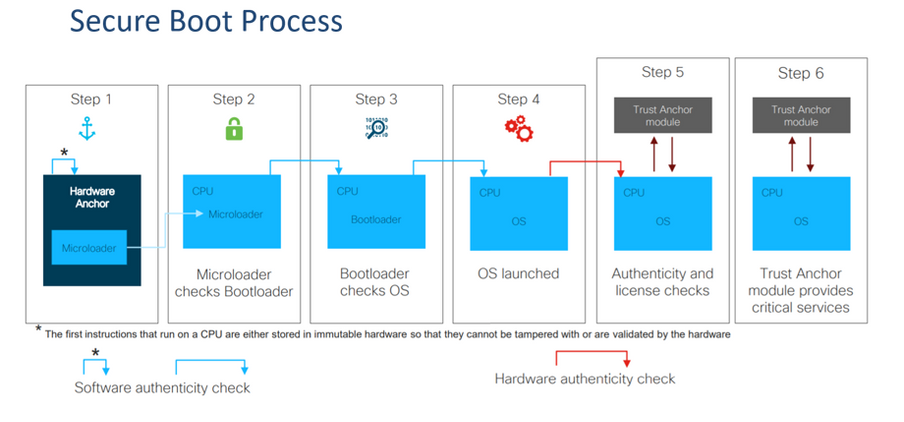
Software Image verification is just part of Cisco’s Secure Boot Process. Once a system boots, the software in turn verifies the authenticity of the network hardware, as well as additional security checks.
Now that the software has securely loaded on the device, the network administrator has at his or her disposal the most powerful and secure networking operating system in the industry: Cisco IOS XE, which contains over 1300 security feature commands and keyword options.
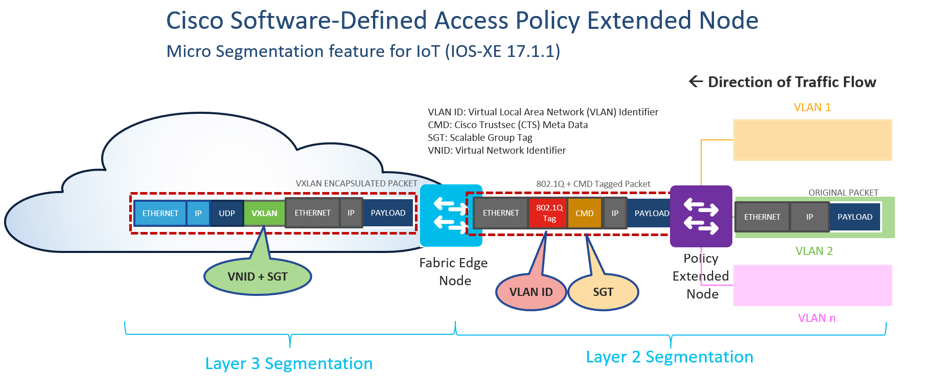
The Cisco IOS XE security toolset is simply too vast to cover in detail, as it represents over 30 years of security networking experience and innovation. As an example of the power of these features, we can examine one that is specific to the needs of IoT: Software-Defined Access Policy Extended Node.
Software Defined Access Policy Extended Node was introduced in Cisco IOS XE in 17.1.1 (in January of 2020). The challenge this feature addresses is the need to perform macro-and micro-segmentation in IoT environments, where the memory and performance platform-requirements of running SD Access Fabric Edge node functionality (where such segmentation is typically performed) are not available. As such, this feature leverages lighter-weight Layer 2 technologies (such as IEEE 802.1Q tagging for macro-segmentation with Cisco Trustsec MetaData tagging for micro-segmentation) and maps these to Layer 3 technologies already present at Fabric Edge devices (such as VXLAN encapsulation, containing a Virtual Network Identifier [VNID] for macro-segmentation and a Scalable Group Tag [SGT]for micro-segmentation) to deliver an end-to-end segmentation solution all the way to the IoT edge. Incidentally, this underlying functionality makes possible the Intent-Based Networking segmentation solution discussed later in this paper.
Not only does Cisco IOS XE support over 1300 security features natively, it also supports application-hosting in containers so that these can run on networking devices. Leveraging this application-hosting capability, Cisco has recently delivered an OT-specific security solution which we will now discuss, namely Cisco Cyber Vision.
Use the Right Software—Part 2: Cisco Cyber Vision
Cisco offers a powerful solution for OT security called Cisco Cyber Vision. Before discussing this solution, it may be helpful to recap some of the key challenges in the OT security space.
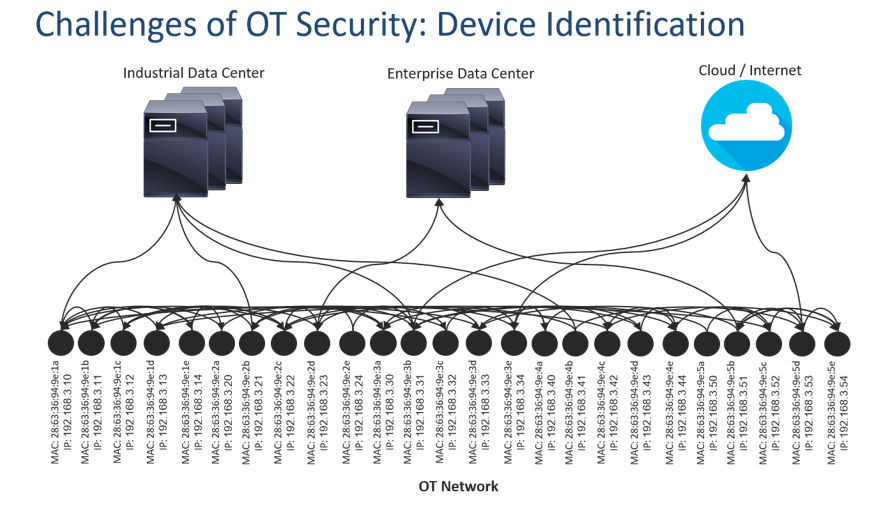
The first key security challenge in OT environments is device identification. Many customers keep device inventories via a manual process of periodically updating these into spreadsheets. Such an approach is often incomplete, out of date and error prone. Additionally, key details of devices may never be gathered, such as the current firmware levels and the associated security vulnerabilities of these. However, device identification is a critical first step towards securing the industrial network, because if devices are simply represented as MAC or IP addresses, the administrator may see how these are communicating between themselves, but would be oblivious if the communications were legitimate or harmful. Similarly, if flows from such devices were noted to be sent and received beyond the local networks, there would be no indication if these flows were benign (such as a machine periodically sending diagnostics data to its builder) or harmful (such as an infected machine reaching out to a command-and-control server to further propagate an cyber attack).
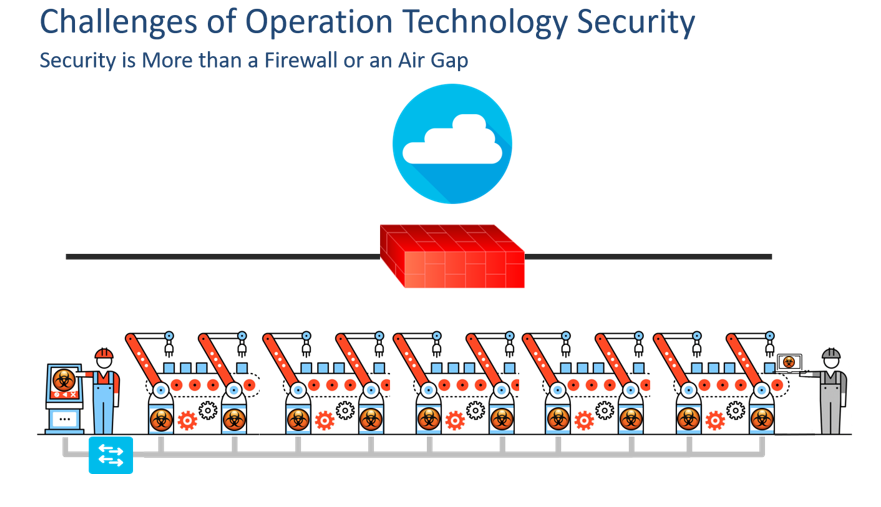
Another OT security challenge is overcoming the prevailing mindset that once an OT network is separated from the Internet via either an air gap or a firewall, then no further security concern exists. This mindset does not consider the malware that often walks in through the front door, residing on the uncontrolled laptops of technicians brought in to periodically update the firmware of the machines connected to the OT network. These OT networks are typically wide, flat, and unsegmented Layer 2 networks. As such, once such laptops connect to these, malware spreads laterally—completely unimpeded—gaining increasing footholds within the network by exploiting the typically unpatched and out-of-date operating systems common in these OT environments.
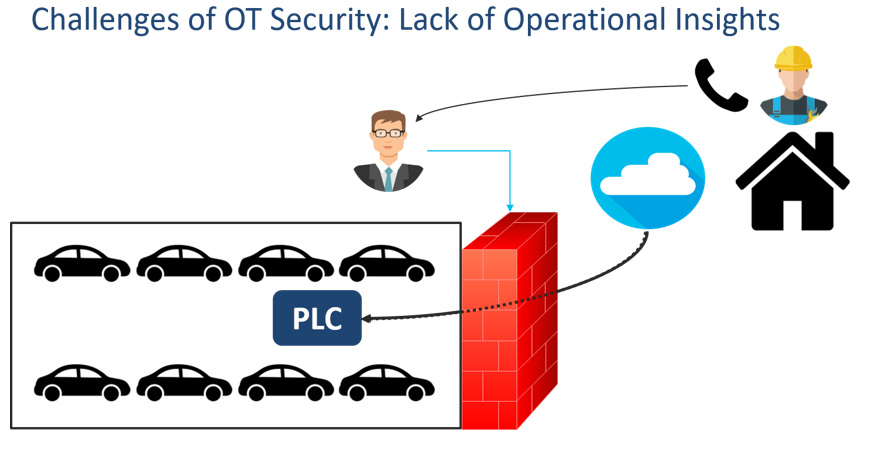
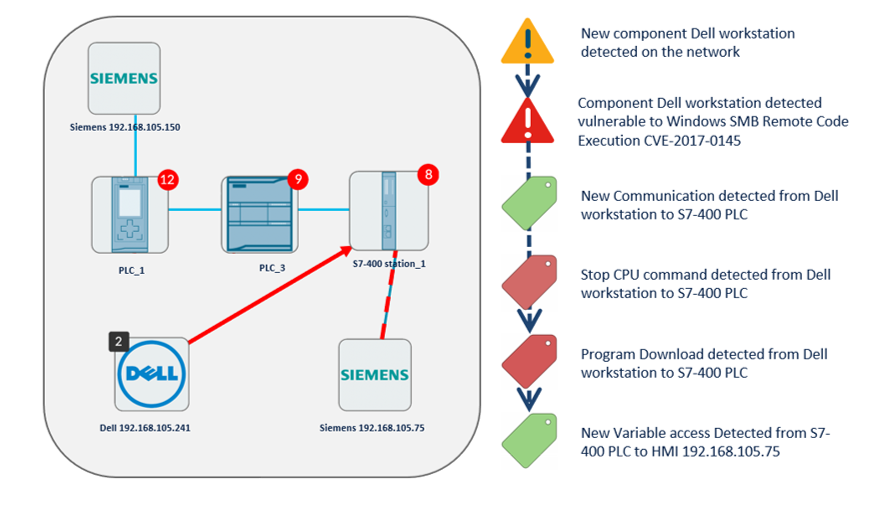
Another OT-specific security concern is the lack of operational insights to be found in these environments. For a true-story example, consider the case of a European auto manufacturer running an early field trial of Cisco Cyber Vision. At the end of the trial, Cyber Vision reported that an unusual event had recently taken place: specifically that a programmable logic controller (PLC) running on the plant floor had recently been loaded with a new program and that this new program had been loaded from a system that had an IP address that was external to the company. The plant supervisor dismissed the insight as untrue, as there were procedures, protocols, and even firewalls in place to prevent such events from happening. However, subsequent investigation did confirm that a production line employee did indeed make the change to the PLC from his home. To do so, he called a friend in the IT department to punch a temporary hole in the firewall (which, incidentally, was closed up again after the new program was loaded). While the actions were well-intentioned and not malicious, the key takeaway for this customer was the realization that they had a complete lack of visibility to such events—well-intentioned or otherwise.
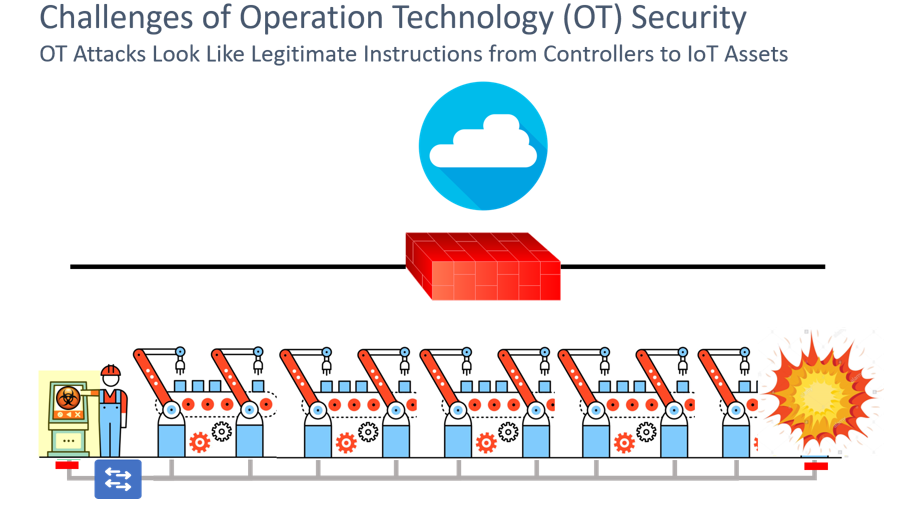
A final challenge that we’ll discuss in the OT security landscape is that cyber attacks in this space may not have the same digital fingerprints commonly found in IT-targeted cyber attacks; rather OT cyber attacks can come from trusted sources communicating with trusted endpoints using trusted protocols that are issuing valid commands. For example, consider the case where a supervisory station infected with malware issues a command to an IoT device under its control—say a turbine—using the vendor-specific industrial protocol to instruct it to “spin faster”. The security policy would allow for this communication to take place; after all, this is a trusted server using a trusted protocol and sending a legitimate command. However, the speed that the turbine is now instructed to spin may be unsafe, which could in turn cause physical damage, disrupting operations and possibly even causing injury. How does an operator detect and protect himself from such subtle, yet dangerous, attacks?
The OT security industry offers two general approaches to meeting security challenges:
- Add a hardware sensor to the OT network—however, this solution does not scale, as now customers need to deploy, operate and support not only their network infrastructure but also supplementary security infrastructure
- Span network traffic to a centralized hardware sensor—however, again this solution presents scalability concerns, but this time at the cost of bandwidth rather than hardware; in low bandwidth environments or in metered-bandwidth environments this may be a non-starter, simply due to the incremental costs involved; however, even in Ethernet environments many customers are already bandwidth-pressed (demanding 10G uplinks and Multi-Gigabit downlinks) and are averse to effectively doubling their bandwidth requirements to support this approach
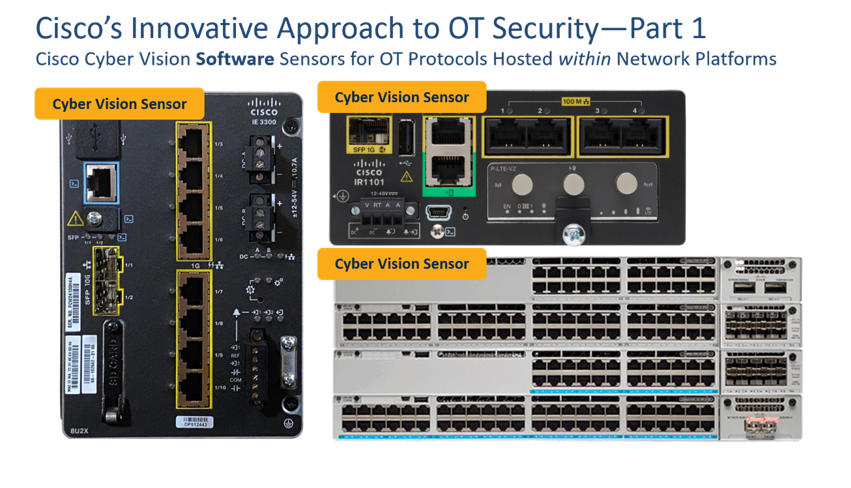
In contrast to these industry-approaches, Cisco Cyber Vision provides innovation in three key areas. The first is that Cisco doesn’t require customers to install dedicated hardware sensors, but rather virtualizes their sensor to run as an application on network infrastructure, such as Cisco Catalyst Industrial Ethernet (IE) switches or Cisco ISR Industrial Routers (IR) or even Cisco Catalyst 9300 switches (which may be found in some industrial environments, albeit in temperature-controlled cabinets/rooms). Cisco’s unique approach of using a software sensor for OT protocols is not only an industry-first, but also the most scalable solution in this space, as it allows for the security solution to simply scale with the network infrastructure itself.
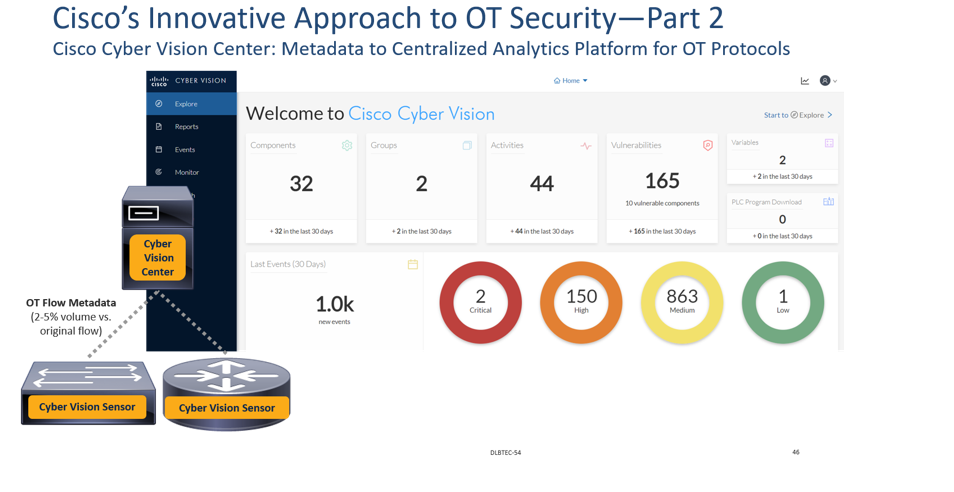
The second part of Cisco’s innovative approach is the use of distributed analytics and OT flow metadata to minimize bandwidth impact. The Cyber Vision Sensors running on the network devices perform deep packet inspection (DPI) on all OT flows. However, rather than mirroring these flows to a central analytics engine—the Cisco Cyber Vision Center—these sensors summarize OT flows as metadata, not unlike NetFlow records. However, the metadata Cyber Vision uses far exceeds the data contained in NetFlow records. NetFlow primarily catalog the 5-tuples of an IP flow (i.e. the Source IP Address, the Destination IP address, the Source Port, the Destination Port and the Layer 4 Protocol [typically TCP or UDP]) as well as the amount of packets/bytes sent. Cisco Cyber Vision goes far beyond this by detailing attributes of the devices sending and receiving the flows, the OT protocols used, the commands sent and received, and even the specific variables that these commands reference. As an analogy, while NetFlow can tell you who is talking to who, Cyber Vision metadata can tell you not only who is talking to who, but also the languages they are speaking, as well as specific details of their conversation. And the summary of these flows is highly efficient, typically consuming only 2-5% of incremental bandwidth.
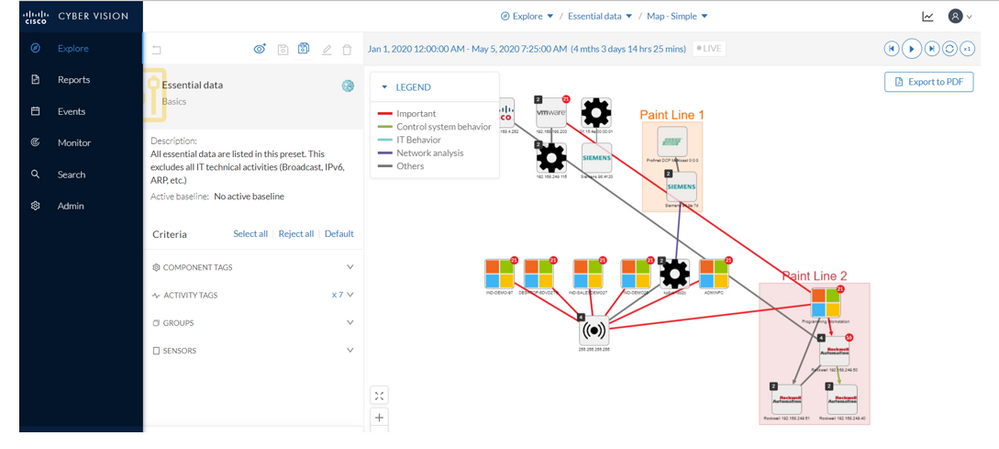
The Cisco Cyber Vision Center, in turn, compiles and analyzes all the metadata sourced from all network devices running the Cyber Vision Sensor and presents these to the operator. In such a manner, Cyber Vision identifies all devices running in the OT network and illustrates how these are communicating with each other.
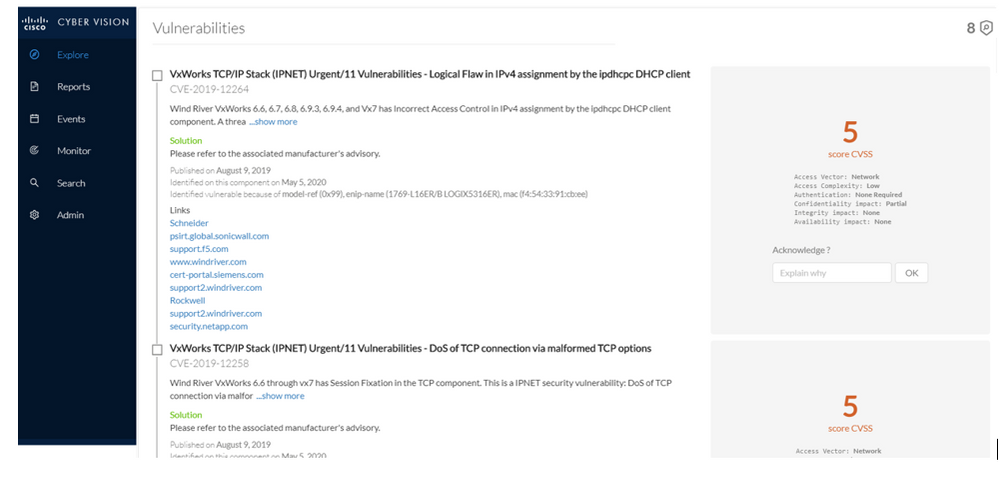
Additionally, Cyber Vision brings long-overdue IT security hygiene to OT environments by identifying known security vulnerabilities of each platform according to its software or firmware version.
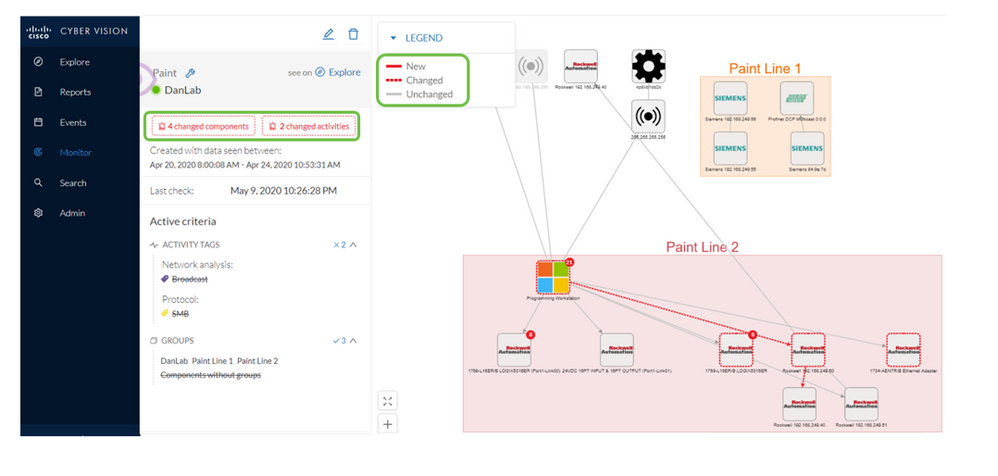
Additionally, Cyber Vision provides operational insights by abstracting vendor-specific industrial protocol operations into “Activity Tags” that summarize the actions being performed, and thus providing a common language for OT and IT to describe operational events.
And finally, all operational events are recorded within a time-series database. This makes it possible for operators can “go back in time” to troubleshoot events. Additionally, the time series database makes it possible to baseline the network to identify what is normal for a specific environment. This baseline can subsequently be leveraged as a reference benchmark to identify anomalies. Anomalies can include devices that have been added or removed from the network, new communication flows that have not yet been observed over the network or even new variables that are being used in conjunction with operational commands (e.g. as described in the example of the turbine that is being instructed to “spin faster” until an unsafe situation has been created).
However, the greatest strength of Cisco Cyber Vision, its architectural integration capabilities, will now be discussed.
Integrate Your Architectures
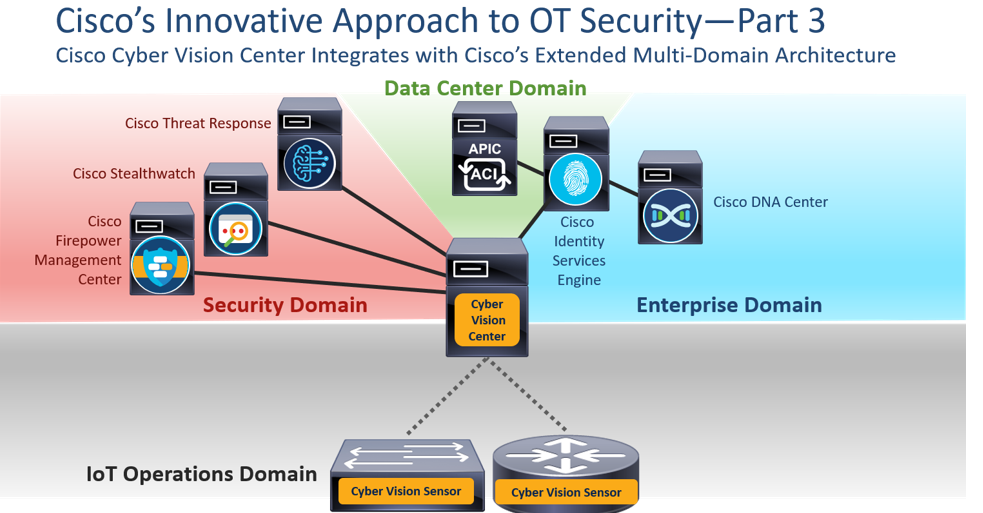
The third key area of innovation that Cisco Cyber Vision brings to industrial networks is its ability to integrate with multi-domain architectures, providing customers with new capabilities and options that are far greater than the sum of the parts of the individual software components. For example, Cisco Cyber Vision can integrate the OT domain with the Security domain, as well as the Enterprise domain and even the Data Center domains.
Let us consider some of these integrations in turn.
Cisco Cyber Vision Integration with Cisco Threat Response
Integrating Cisco Cyber Vision with Cisco Threat Response (CTR) provides a solution to one of the OT security challenges that was introduced earlier in this paper, specifically identifying whether a given OT communication is benign (such as a machine delivering diagnostics information to a machine builder) or harmful (such as a compromised machine reaching out to a command-and-control server).
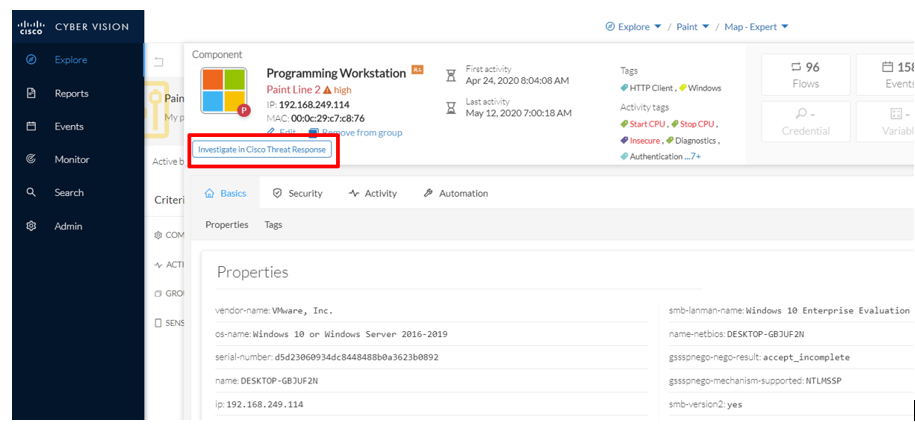
From within Cyber Vision, any given device can be investigated via CTR with a single click.
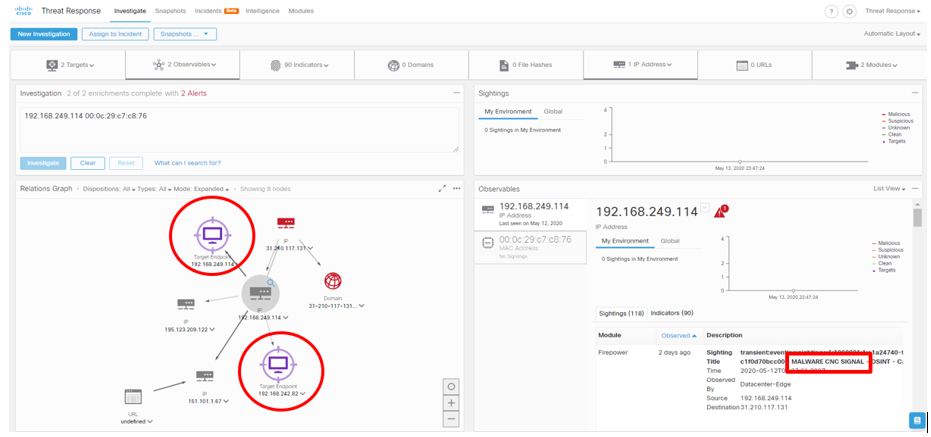
Clicking on the button presented above will result in a contextual cross-launch into CTR, where the device’s activity will be investigated from all available data sources, which can include Cisco Stealthwatch and Cisco Talos Intelligence Group. In the example provided below, we see that the workstation has been in communication with a command-and-control (“CNC”) server due to a malware infection.
Cisco Cyber Vision Integration with Cisco Stealthwatch
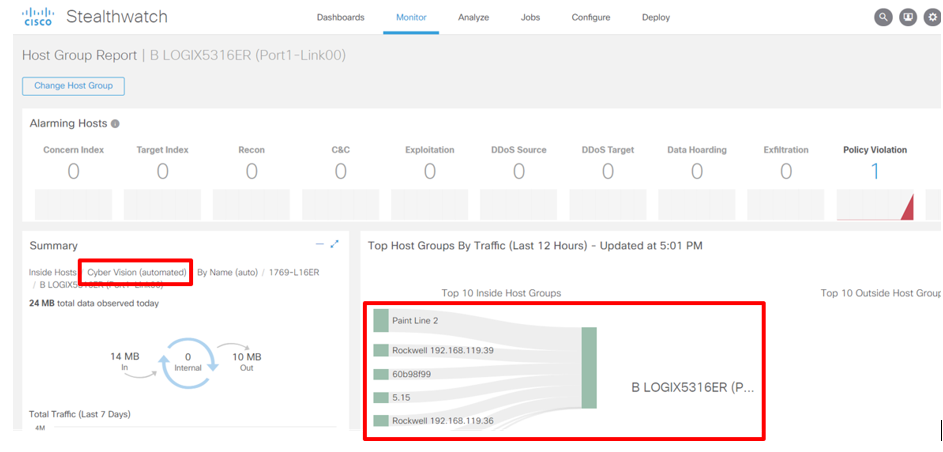
Cisco Stealthwatch provides visibility into IP flows within an organization. When an IP flow originates from an OT device, the operator is not provided sufficient context about what that device is, and as such, cannot determine if the flow is legitimate or illegitimate. To this end, Cyber Vision can enrich host-groups in Stealthwatch with granular device context obtained from Cyber Vision, allowing operators to easily identify flows mapped to industrial endpoints with host-group attributes. Additionally, operators can use host-group attributes, like Cells and Zones, to create alarms for inter cell/zone traffic violations.
Cisco Cyber Vision Integration with Cisco Firepower Management Center
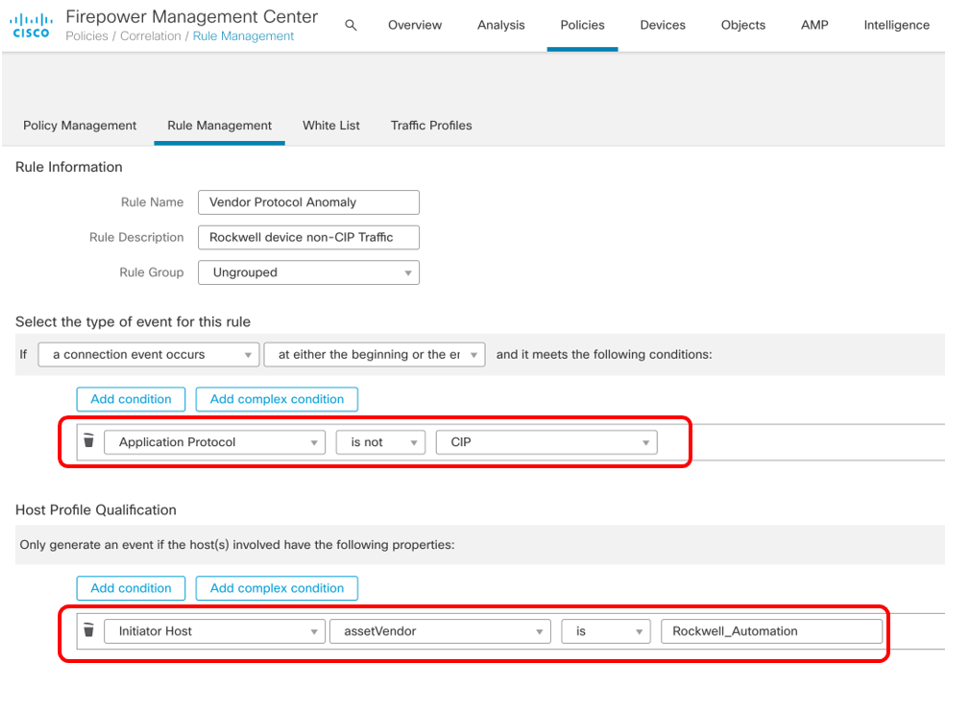
Integrating Cisco Cyber Vision with Cisco Firepower Management Center (FMC) allows for not only the detection of violations, but also the ability to enforce policy to prevent these. For example, Cyber Vision cam map the identity of industrial devices to hosts in FMC for use in correlation policy or to named objects (such as PLC, I/O, Drive, etc.) in FMC for use in access policy. Additionally, through a direct integration with Firepower Threat Defense (FTD), flows that Cyber Vision has identified as anomalous can be killed via FMC.
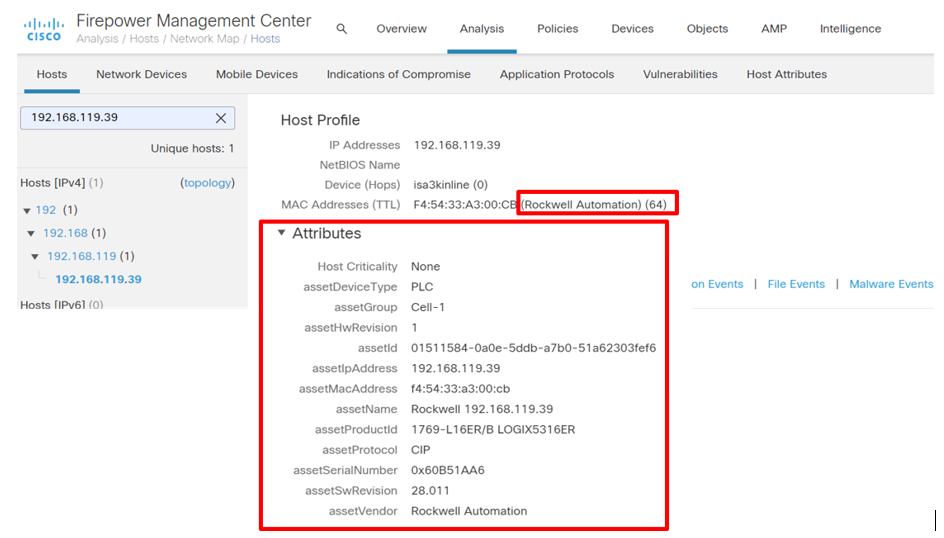
In the example below, device attribute data obtained from Cyber Vision is being ingested by FMC.
In turn, these detailed device attributes can be used in policy enforcement, as in the following screen which shows a policy violation if a flow from a device from Rockwell Automation is not using the Common Industrial Protocol (CIP), which is the default protocol that such a device should use. Without the Cyber Vision integration, such an advanced and granular policy would not be able to be constructed, nor enforced.
Cisco Cyber Vision Integration with Cisco Identity Services Engine
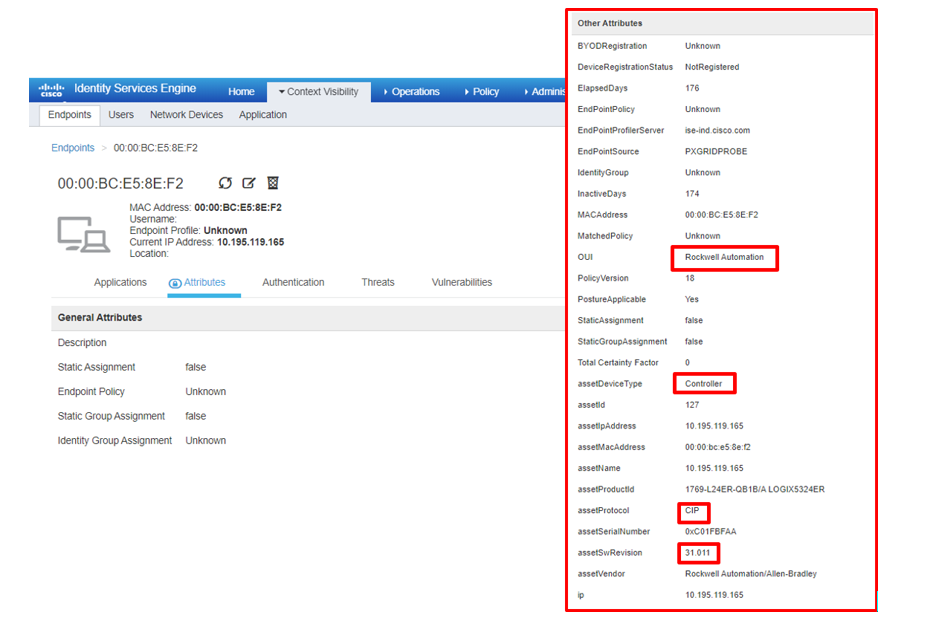
Another example of an architectural integration that enriches policy is the integration of Cisco Cyber Vision with Cisco Identity Services Engine (ISE). On its own, ISE would be aware of OT endpoints by their MAC address and IP addresses only. However, constructing access policies with these attributes alone would be inordinately complex and brittle (as IP addresses can change whenever a new DHCP lease is issued and even MAC addresses can change when devices are hot-swapped to quickly resume operations).
However, endpoint attributes in ISE can be enriched with context provided by Cyber Vision, as is shown below. On its own, ISE would only see the device as an endpoint with MAC address of 00:00:BC:E5:8E:F2 and IP address of 10.195.119.169. However, with context provided by Cyber Vision, it now understands this device to be a Rockwell Automation programmable logic controller that uses the CIP protocol and has a firmware version of 31.011 (among other attributes).
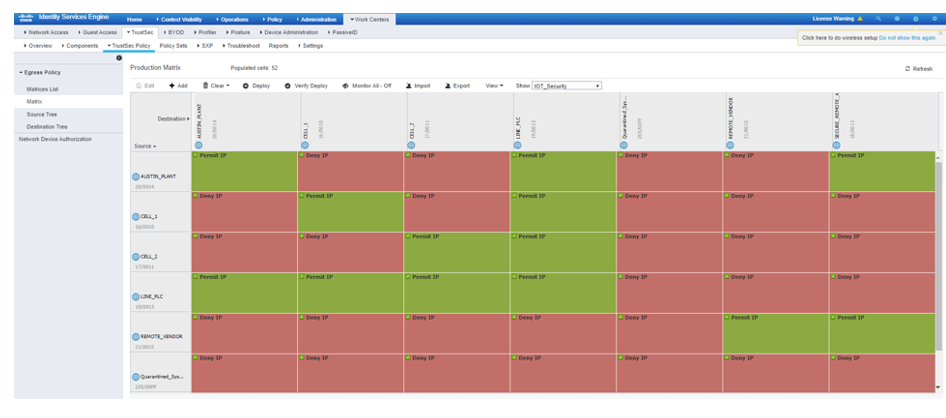
Each of these attributes obtained by Cyber Vision can be leveraged to profile the device and assign a Scalable Group Tag (SGT) in ISE. For example, SGTs may be assigned to devices in a particular location (e.g. “Austin Plant”) or within a particular Zone (e.g. “Zone 1”) or within even a specific Cell (e.g. “Cell 2”). SGTs may also be mapped to vendors (e.g. “Rockwell Automation”), device-types (e.g. “PLC”) or even firmware versions (e.g. “31.011”). Profiling devices according to such attributes and then representing this profile with a SGT provides policy administrators tremendous options, flexibility and granularity in policy expression and enforcement. For example, this approach can be used to not only enforce communication zones between cells, but can also define how machines are to communicate within a cell, which is also referred to as micro-segmentation.
Cisco Cyber Vision Integration with Cisco DNA Center
Finally, as Cyber Vision, ISE and DNA Center all communicate over the Platform Exchange Grid (pxGrid), any SGTs defined in ISE are also available in Cisco DNA Center for policy. However, Cisco DNA Center does far more than administer policy, it brings Intent-Based Networking solutions to the enterprise and the extended enterprise, including automation, analytics, and machine-learning.
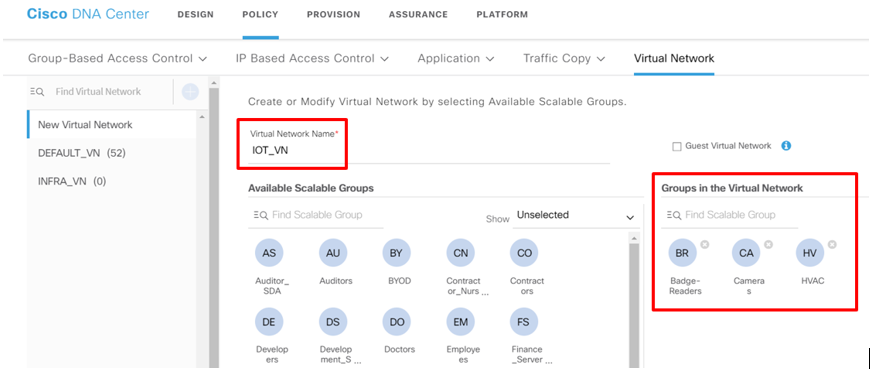
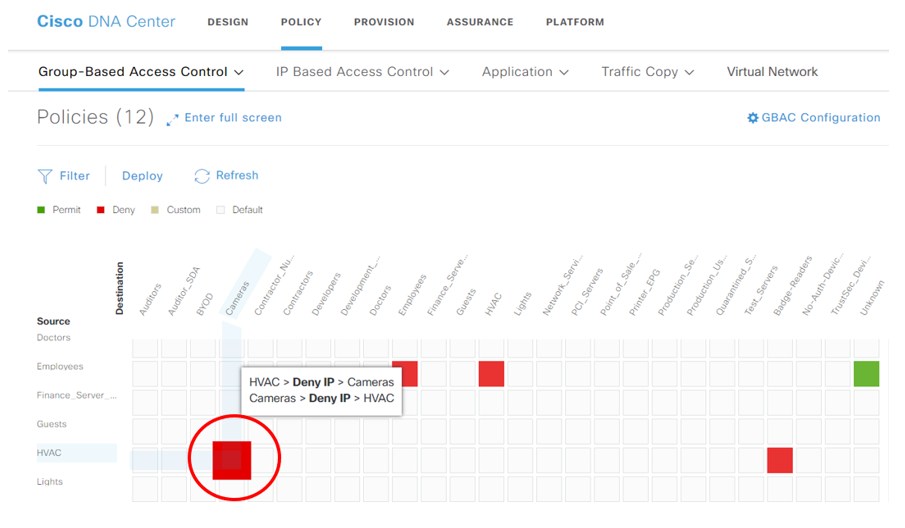
For example, using this integration the enterprise can be extended to the IoT edge by using Intent Based Networking solutions like Software-Defined Access. SD Access easily enables macro-segmentation of networks, so that – for example – IoT devices can share the same physical infrastructure with other virtual networks, while remaining logically isolated from the same. Creating and deploying a virtual network is as simple as giving it a name (e.g. “IOT_VN”) and dragging-and-dropping the Scalable Groups that are intended to be assigned to the virtual network, as shown below.
Additionally, micro-segmentation policies are similarly very easy to express and enforce within Cisco DNA Center. By default, all devices within a virtual network can communicate with each other. However, restrictions on these communications can be enforced via micro-segmentation policies. Authoring a micro-segmentation policy is a matter of four simple steps:
- Giving the policy a name
- Selecting the Source Scalable Group
- Selecting the Destination Scalable Group
- Selecting the Traffic Contract (e.g. Permit or Deny, etc.)
The Journey to Securing Your Industrial Networks
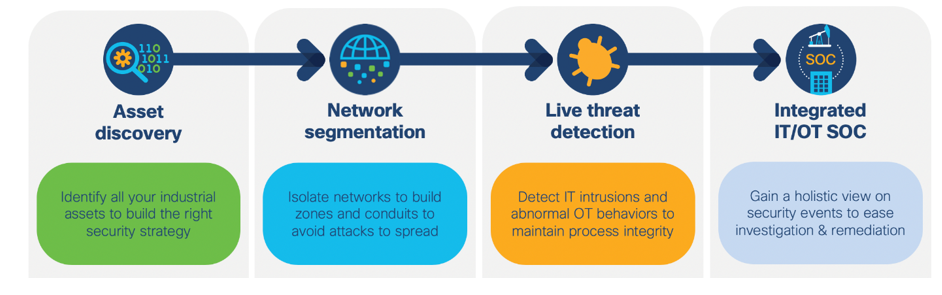
This paper has presented a lot of technology options – but where should you begin? Cisco recommends the following approach to securing your industrial network.
- Start by using Cisco Cyber Vision to discover your assets, as once you have identified these then you will be able to build the right security strategy for your OT network. Cyber Vision will also enable you to visualize your traffic patterns to identify segmentation boundaries.
- Segment your network to isolate communication zones and conduits and prevent malware from spreading laterally. Segmentation could be done at a local level using Cisco ISA3000 industrial firewalls or even at a micro-segmentation level by leveraging the integration with Cisco Identity Services Engine. However, the journey doesn’t end here.
- Detect OT threats as they happen by leveraging Cyber Vision’s capabilities to identify abnormal OT behaviors to maintain process integrity.
- Integrate your IT/OT SOC to gain a holistic view of security events and to expedite and simplify investigation and remediation.
Summary and Key Takeaways
To summarize, there are three key steps to securely connect your industrial network:
- Start with the right hardware
- Use the right software
- Integrate your architectures
Cisco networking hardware meets not only the security, scalability, and extensibility requirements of IT, but also the demanding industry-specific requirements of OT.
Additionally, Cisco is unmatched in networking security, having been an innovator in this space for over 30 years. Cisco Cyber Vision in particular brings unparalleled visibility, scalability and policy-flexibility to industrial networks, providing operators with device identification, operational insights, anomaly detection and architectural integrations.
Finally, begin the journey to securing your industrial networks by:
- Discovering your OT assets
- Segmenting your OT network
- Detecting OT Threats, and
- Integrating your IT/OT SOC
Want to learn more about Cisco IoT Hardware?
- View DGTL-PSOIOT-2002 “How to Build an Industrial Switch” on June 18
Want to learn more about Cisco Cyber Vision?
- View DGTL-PSOIOT-2200 “Securing Industrial Networks: Intro to Cisco Cyber Vision” on June 18
Want to kick the tires?
- Cisco Cyber Vision, CTR, ISE, DNAC are all available for on-demand demos at dcloud.cisco.com
Want to learn more about Cisco IoT products and solutions?
Visit cisco.com/go/iot
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: