- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco ISE Sponsor Portal authentication via JumpCloud SSO
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-30-2023 03:44 PM - edited 08-30-2023 03:47 PM
- What is JumpCloud?
- Introduction
- Components Used
- High Level Flow
- Configuration Steps
- JumpCloud User/Group Configuration
- ISE Initial SAML Configuration
- JumpCloud SSO Configuration
- Update ISE Configuration
- User Experience
- Logs and Troubleshooting
- Browser Debugging
- ISE Debugging
- Additional Observations
What is JumpCloud?
JumpCloud is a cloud-based open directory solution that offers, among others, features such as Cloud Directory, Multi-Factor Authentication (MFA), Single Sign-On (SSO), and Mobile Device Management (MDM).
For more information on JumpCloud, please see www.jumpcloud.com.
Introduction
This article intends to provide example configuration for authenticating users logging into the Cisco ISE Sponsor Portal against JumpCloud using SAML/SSO.
The content assumes the reader is familiar with Cisco ISE basic functionality as well as the Guest/Sponsor features. If you are new to Cisco ISE or these features, please see the available documentation as well as the ISE Webinars available from the link below.
https://cs.co/ise-resources#Learn
Components Used
This configuration was tested in a Non-Production lab environment using the following components:
- Cisco ISE version 3.2 patch 3
- Firefox 116.0.3
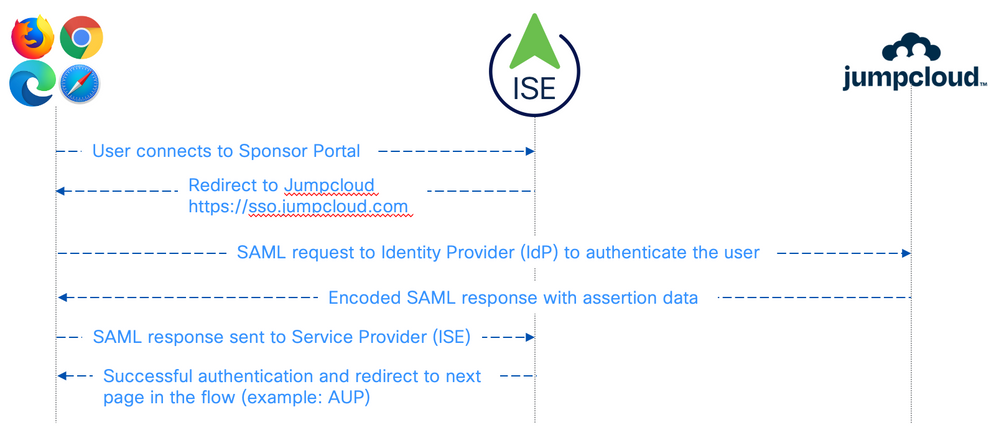
High Level Flow
The following diagram illustrates the high level communication flow for the SAML/SSO authentication for the Sponsor Portal.
Configuration Steps
JumpCloud User/Group Configuration
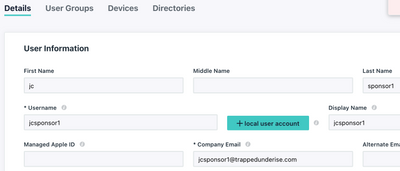
Create a JumpCloud user to be used for the Sponsor login
- In the JumpCloud portal, navigate to User Management > Users
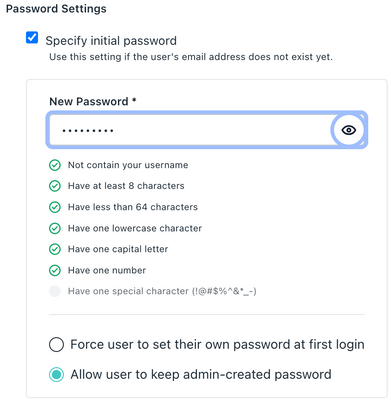
- Create the user account and set the initial password
** The "allow user to keep admin-created password" option was used in this example for simplicity only
Example:
- Click Save User and specify the desired Activation option (Schedule Activation, Activate Now, Activate Later)
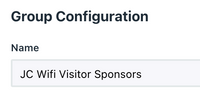
Create a Group for the Sponsor Users
- Navigate to User Management > User Groups
- Create the Group, add the User(s), and click Save
Example:
ISE Initial SAML Configuration
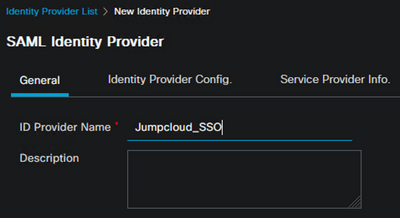
In ISE, add the SAML IdP
- Navigate to Administration > Identity Management > External Identity Sources > SAML Id Providers
- Click Add, define the name, and click Submit
Example:
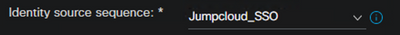
Create or update the Sponsor Portal
- Navigate to Work Centers > Guest Access > Portals & Components > Sponsor Portals
- Select the Sponsor Portal or create a new portal
- In the Identity Source Sequence drop-down, select the SAML IdP
- Configure any other required settings and click Save
Example:
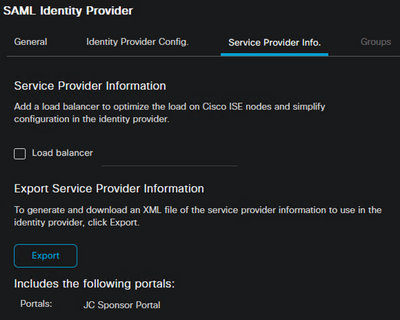
Update the SAML IdP in ISE
- Navigate back to Administration > Identity Management > External Identity Sources > SAML Id Providers and select the IdP
- Select the Service Provider Info tab and Export the SP information
- Save the zip file to a local folder and unzip the files
Example:
JumpCloud SSO Configuration
Create the SSO Application
- In the JumpCloud portal, navigate to User Authentication > SSO
- Locate the Cisco ISE application and click Configure
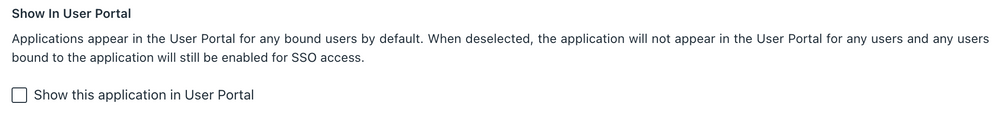
- On the General Info tab, define the Display Label
- Untick the box for "Show this application in User Portal"
** This step is taken to avoid user confusion. ISE only supports SP-initiated SAML flows, so initiating connection to the Sponsor Portal from the JumpCloud portal will fail.
- On the SSO tab, click the Upload Metadata button and browse to the XML file extracted from the zip file in the prior step
- JumpCloud will update the SP Entity ID and ACS URLs with the ones present in the uploaded XML file
Example:
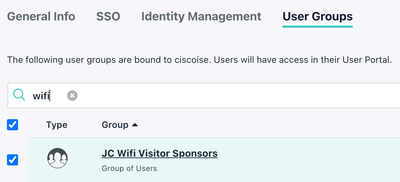
- In the User Groups tab, select the Sponsor Group and click Activate
Example:
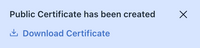
JumpCloud will create a public certificate and pop a message with a link to download the certificate. When testing this flow, it was not found to be necessary to upload this certificate to ISE.
- In the SSO application, on the SSO tab, click Export Metadata and save the XML file to a local folder
Update ISE Configuration
Update the SAML IdP
- In ISE, navigate back to Administration > Identity Management > External Identity Sources > SAML Id Providers and select the IdP
- Select the Identity Provider Config tab and import the JumpCloud Metadata XML file exported in the prior step
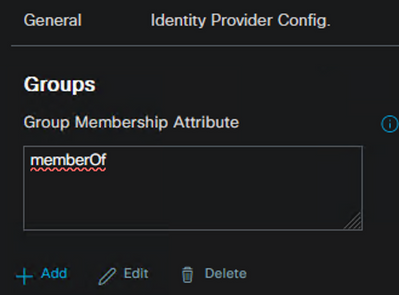
- Select the Groups tab
- In the Group Membership Attribute box, type memberOf and click Add
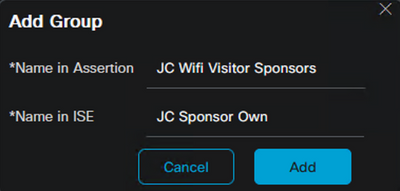
- Populate the Group name from JumpCloud for the Name in Assertion
- Define a Group name in ISE for the Name in ISE
- Click Add and Save
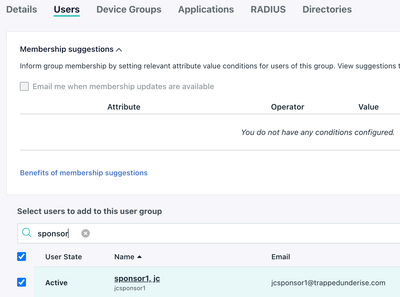
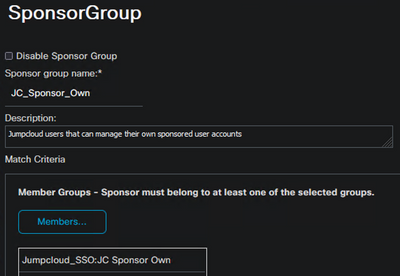
Configure the Sponsor Group Membership
- Navigate to Work Centers > Guest Access > Portals & Components > Sponsor Groups
- Select an existing Sponsor Group or create a new group
- Click on Members and add the group defined above that maps to the JumpCloud group
- Configure the desired Sponsor permissions (in this example, we only allow the Sponsor to manage accounts they have created)
- Configure any other required settings and click Save
User Experience
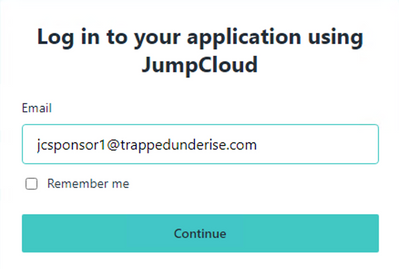
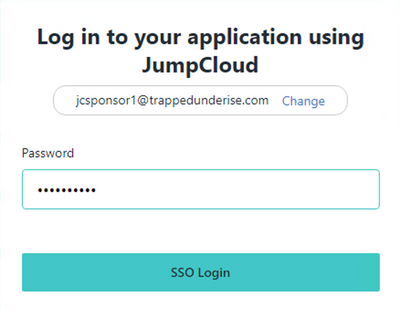
When the user opens a browser and connects to the 'friendly FQDN' configured for the Sponsor Portal (jcsponsor.ise.trappedunderise.com; in this example), they will be redirected to the JumpCloud SSO login portal to enter their email and password.
Example:
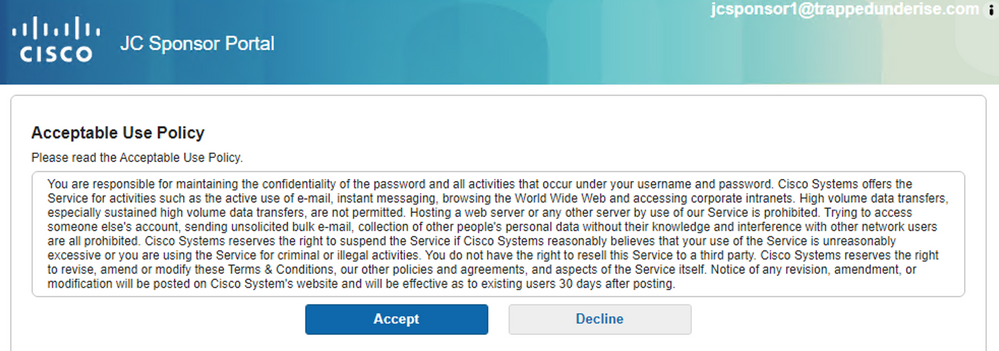
Upon successful login, the browser will be redirected back to the Sponsor Portal and display the next page in the configured portal flow; in this case, the Acceptable Use Policy.
Example:
Logs and Troubleshooting
Browser Debugging
More detail on the SAML flow can be seen by using the SAML-tracer extension in Firefox, or another similar browser tool.
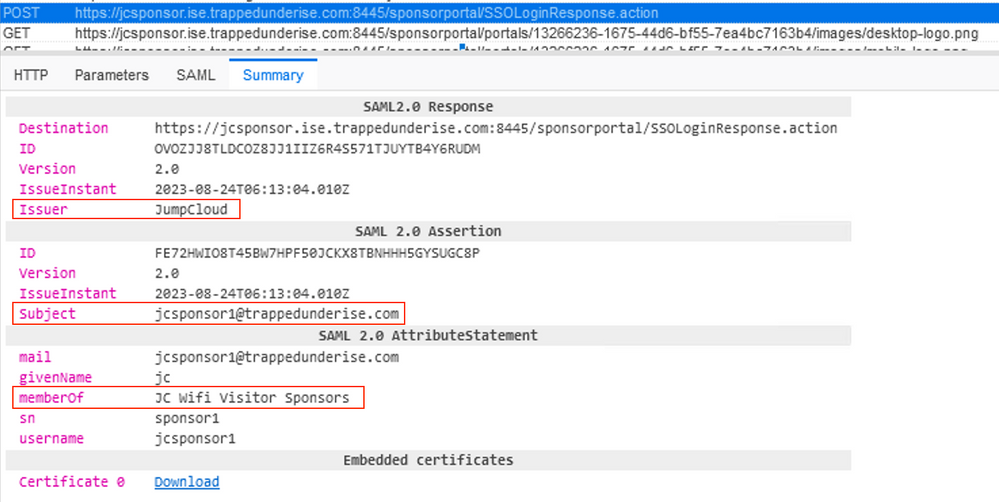
In this example, when the SAML response from JumpCloud is redirected back to ISE through the browser, you can see the POST message for the SSOLoginResponse.action target.
In the Summary tab, the following information can be seen from the assertion data sent by JumpCloud:
- Issuer = JumpCloud
- Subject = jcsponsor1@trappedunderise.com (our user's email address used for logging into the JumpCloud SSO)
- MemberOf = JC Wifi Visitor Sponsors (our JumpCloud group name)
- Other attributes provided by JumpCloud
ISE Debugging
To see the details on the ISE side, the Debug Wizard can be used to set the necessary logs to Debug level.
- Navigate to Operations > Troubleshoot > Debug Wizard
- Click Add to create a new Debug Profile
- Specific a Name (example: SAML) and set the following Components to Debug Log Level:
- guestaccess
- opensaml
- portal-web-action
- saml
- sponsorportal
- Click Save
- When prompted to enable the Profile on an ISE node now, click Enable
- Select the PSN(s) that will be used for the Sponsor Portal flow and click Save
- Browse to the Sponsor Portal web page and navigate through the login flow
- After completing the flow, navigate to the Operations > Troubleshoot > Download Logs page in ISE
- Select the ISE node that serviced the Sponsor Portal flow, and select the Debug Logs tab
- Scroll down to the ise-psc Debug Log Type and click the ise-psc.log link (without the datestamp; which are older logs)
- Download the zip file, extract the ise-psc.log file, and open in your editor of choice
Initial redirection to the SAML IdP from the Sponsor Portal
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cisco.cpm.saml.framework.SAMLUtils -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Jumpcloud_SSO
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cisco.cpm.saml.framework.SAMLUtils -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://sso.jumpcloud.com/saml2/ciscoise
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cisco.cpm.saml.framework.SAMLUtils -::::- SPProviderId for Jumpcloud_SSO is: http://CiscoISE/13266236-1675-44d6-bf55-7ea4bc7163b4
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cisco.cpm.saml.framework.SAMLUtils -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Jumpcloud_SSO
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - providerId (as should be found in IdP configuration):http://CiscoISE/13266236-1675-44d6-bf55-7ea4bc7163b4
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - returnToId (relay state):_13266236-1675-44d6-bf55-7ea4bc7163b4_DELIMITERportalId_EQUALS13266236-1675-44d6-bf55-7ea4bc7163b4_SEMIportalSessionId_EQUALS8aa0a2b7-57ed-4409-aa50-b59c04a2134f_SEMItoken_EQUALS49WXXFLSZ5GV9NOM02CFAOQO6G536GNY_SEMI_DELIMITERjcsponsor.ise.trappedunderise.com
2023-08-25 09:37:39,196 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-7][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - spUrlToReturnTo:https://jcsponsor.ise.trappedunderise.com:8445/sponsorportal/SSOLoginResponse.action
SAML response from the browser
2023-08-25 09:37:40,389 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:portalId=13266236-1675-44d6-bf55-7ea4bc7163b4;portalSessionId=8aa0a2b7-57ed-4409-aa50-b59c04a2134f;token=49WXXFLSZ5GV9NOM02CFAOQO6G536GNY;
2023-08-25 09:37:40,389 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_13266236-1675-44d6-bf55-7ea4bc7163b4_DELIMITERportalId=13266236-1675-44d6-bf55-7ea4bc7163b4;portalSessionId=8aa0a2b7-57ed-4409-aa50-b59c04a2134f;token=49WXXFLSZ5GV9NOM02CFAOQO6G536GNY;_DELIMITERjcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,389 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:jcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,389 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Is redirect requiered: InitiatorPSN:jcsponsor.ise.trappedunderise.com This node's host name:ise32-2 LB:null request Server Name:jcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,390 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- To compare address obj with requestServerName - hostAddress:192.168.222.52 hostName:jcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,390 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- This node is the initiator (jcsponsor.ise.trappedunderise.com) this node host name is:jcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,390 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://javax.xml.XMLConstants/feature/secure-processing'
2023-08-25 09:37:40,390 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://apache.org/xml/features/disallow-doctype-decl'
2023-08-25 09:37:40,392 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Beginning to decode message from inbound transport of type: org.opensaml.ws.transport.http.HttpServletRequestAdapter
2023-08-25 09:37:40,392 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML relay state of: _13266236-1675-44d6-bf55-7ea4bc7163b4_DELIMITERportalId_EQUALS13266236-1675-44d6-bf55-7ea4bc7163b4_SEMIportalSessionId_EQUALS8aa0a2b7-57ed-4409-aa50-b59c04a2134f_SEMItoken_EQUALS49WXXFLSZ5GV9NOM02CFAOQO6G536GNY_SEMI_DELIMITERjcsponsor.ise.trappedunderise.com
2023-08-25 09:37:40,392 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Getting Base64 encoded message from request
2023-08-25 09:37:40,392 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Parsing message stream into DOM document
2023-08-25 09:37:40,394 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Unmarshalling message DOM
2023-08-25 09:37:40,394 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Starting to unmarshall Apache XML-Security-based SignatureImpl element
2023-08-25 09:37:40,394 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Constructing Apache XMLSignature object
2023-08-25 09:37:40,394 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding canonicalization and signing algorithms, and HMAC output length to Signature
2023-08-25 09:37:40,394 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding KeyInfo to Signature
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Message succesfully unmarshalled
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML message
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.saml2.binding.decoding.BaseSAML2MessageDecoder -::::- Extracting ID, issuer and issue instant from status response
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- No security policy resolver attached to this message context, no security policy evaluation attempted
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Successfully decoded message.
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Checking SAML message intended destination endpoint against receiver endpoint
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Intended message destination endpoint: https://jcsponsor.ise.trappedunderise.com:8445/sponsorportal/SSOLoginResponse.action
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Actual message receiver endpoint: https://jcsponsor.ise.trappedunderise.com:8445/sponsorportal/SSOLoginResponse.action
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML decoder's URIComparator - [https://jcsponsor.ise.trappedunderise.com:8445/sponsorportal/SSOLoginResponse.action] vs. [https://jcsponsor.ise.trappedunderise.com:8445/sponsorportal/SSOLoginResponse.action]
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- SAML message intended destination endpoint matched recipient endpoint
2023-08-25 09:37:40,397 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: statusCode:urn:oasis:names:tc:SAML:2.0:status:Success
Parsing of Assertion attributes received from JumpCloud
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : mail
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured, Attribute=<mail> add value=<jcsponsor1@trappedunderise.com>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute<mail> value=<jcsponsor1@trappedunderise.com>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : givenName
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured, Attribute=<givenName> add value=<jc>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute<givenName> value=<jc>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : objectGUID
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute=<objectGUID> has no value in the response
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : memberOf
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured, Attribute=<memberOf> add value=<JC Wifi Visitor Sponsors>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute<memberOf> value=<JC Wifi Visitor Sponsors>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : sn
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured, Attribute=<sn> add value=<sponsor1>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute<sn> value=<sponsor1>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : userPrincipalName
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute=<userPrincipalName> has no value in the response
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name : username
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured, Attribute=<username> add value=<jcsponsor1>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute<username> value=<jcsponsor1>
Caching the Group attribute from JumpCloud as ExternalGroup
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.cfg.IdentityProviderMgr -::::- getDict: Jumpcloud_SSO
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]: read Dict attribute=<ExternalGroups>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute <mail> NOT configured in IdP dictionary, NOT caching
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute <givenName> NOT configured in IdP dictionary, NOT caching
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [cacheGroupAttr] Adding to cache ExternalGroup values=<JC Wifi Visitor Sponsors>
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute <sn> NOT configured in IdP dictionary, NOT caching
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Attribute <username> NOT configured in IdP dictionary, NOT caching
2023-08-25 09:37:40,400 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [storeAttributesSessionData] idStore=<Jumpcloud_SSO> userName=jcsponsor1@trappedunderise.com>
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:getEmail] The email attribute not configured on IdP
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: email attribute value:
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLFacadeImpl:: IDP Groups in SAML assertion: [JC Wifi Visitor Sponsors]
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: found signature on the reponse
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Retrieve [CN=JumpCloudSAMLUser, OU=JumpCloudSAMLIdP, O=Cisco, L=Boulder, ST=CO, C=US] as signing certificates
2023-08-25 09:37:40,401 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: loginInfo:SAMLLoginInfo: name=jcsponsor1@trappedunderise.com, format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, sessionIndex=cd2ba616-862e-496b-8934-4b998d534345, time diff=-208, attributeValues=null
2023-08-25 09:37:41,168 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - Session:null IDPResponse:
IdP ID: Jumpcloud_SSO
Subject: jcsponsor1@trappedunderise.com
Group: JC Wifi Visitor Sponsors
SAML Status Code:urn:oasis:names:tc:SAML:2.0:status:Success
SAML Success:true
SAML Status Message:null
SAML email:
SAML Exception:nullUserRole : SPONSOR
Authenticating the User for the Portal
2023-08-25 09:37:41,172 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - about to call authenticateSAMLUser messageCode:null subject:jcsponsor1@trappedunderise.com
2023-08-25 09:37:41,322 INFO [RMI TCP Connection(3085)-127.0.0.1][[]] api.services.server.role.RoleImpl -::::- Fetched Role Information based on RoleID: 6dd3b090-8bff-11e6-996c-525400b48521
2023-08-25 09:37:41,330 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [SAMLSessionDataCache:getGroupsOnSession] idStore=<Jumpcloud_SSO> userName=<jcsponsor1@trappedunderise.com>
2023-08-25 09:37:41,330 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [getAttributeOnSession] idStore=<Jumpcloud_SSO> userName=<jcsponsor1@trappedunderise.com> attributeName=<Jumpcloud_SSO.ExternalGroups>
2023-08-25 09:37:41,330 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - added user groups from SAML response to AuthenticationResult, all retrieved groups:[JC Wifi Visitor Sponsors]
2023-08-25 09:37:41,330 DEBUG [https-jsse-nio-192.168.222.52-8445-exec-2][[]] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Authenticate SAML User - result:PASSED
Additional Observations
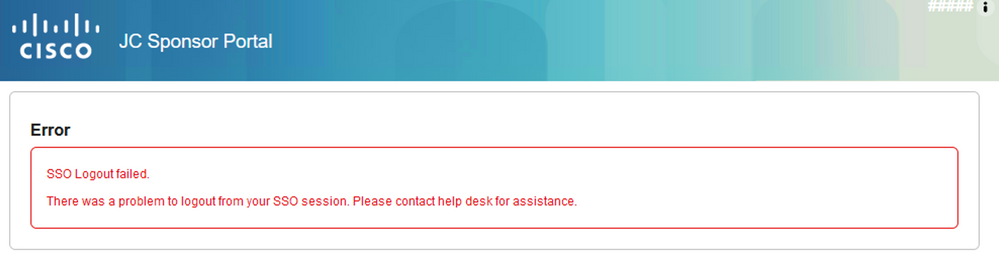
When attempting to logout of the Sponsor Portal, the following error is seen.
This is expected behaviour due to the fact that JumpCloud does not support a Logout URL in the SSO Application at this time.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: