- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE Zero Touch Provisioning (ZTP)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-29-2022 09:34 AM - edited 08-30-2022 06:04 AM
- About this article
- Create ise-ztp.img file
- ZTP Configuration for ISE 3.1
- ZTP Configuration for ISE 3.2 and newer
- Installing ISE using ise-ztp.img
- Cisco SNS CIMC Installation
- VMWare vCenter ISO Installation
- VMWare vCenter OVA Installation
- Nutanix CE ISO Installation
- Microsoft Hyper-V ISO Installation
- Linux KVM ISO Installation
- Installing ISE using OVA and VM Data (no ise-ztp.img file)
- Public Cloud Installations
- Cloud Platforms ZTP Configuration Format
- Amazon Web Services (AWS)
- Microsoft Azure Cloud
- Oracle Cloud Infrastructure (OCI)
- Verify ZTP configuration after Installation
- Can I use ZTP with ISE-PIC?
- Resources
About this article
ISE 3.1 introduces Zero Touch Provisioning (ZTP) as a more efficient means to complete the setup script which assigns the hostname, IP Address, DNS Server, NTP Server, etc. to your ISE Node.
ISE 3.2 adds the ability to use Public Key Authentication to access the CLI console of your ISE nodes. You can also use the ZTP configuration to skip the ping, DNS, and NTP checks during installation. As a security measure, since the ZTP configuration is plain text and contains the ISE Administrator level password, when using ZTP on ISE 3.2 and newer, you will be required to change your password the first time you log in to the Web Interface (GUI).
In this post, I will detail the ZTP process, what I have found to be roadblocks, and how to overcome them (roadblocks are shown in italics).
There are two main configurations for the ZTP process - one process uses the ise-ztp.img file and offers the most compatibility with more platforms; the other uses VMWare Native APIs known as VM Data. Which process you choose can depend on a few factors:
- SNS Appliance or VM Platform
- Version of VMWare vCenter installed
- Access to Linux (RHEL, CentOS, or Ubuntu) system with root access
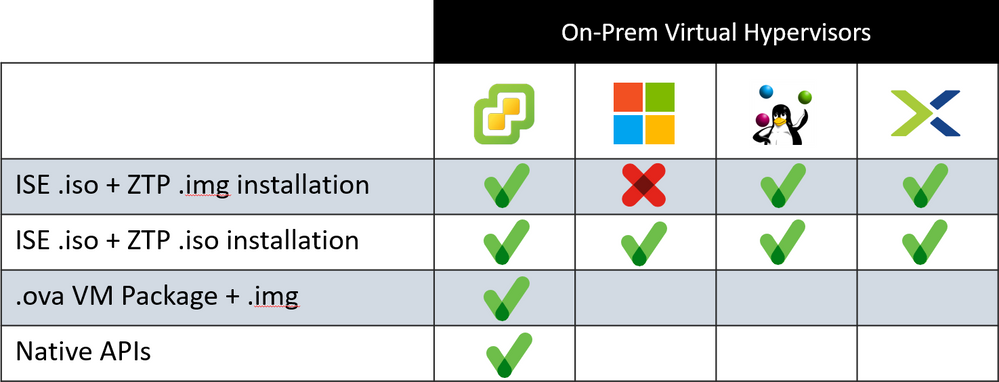
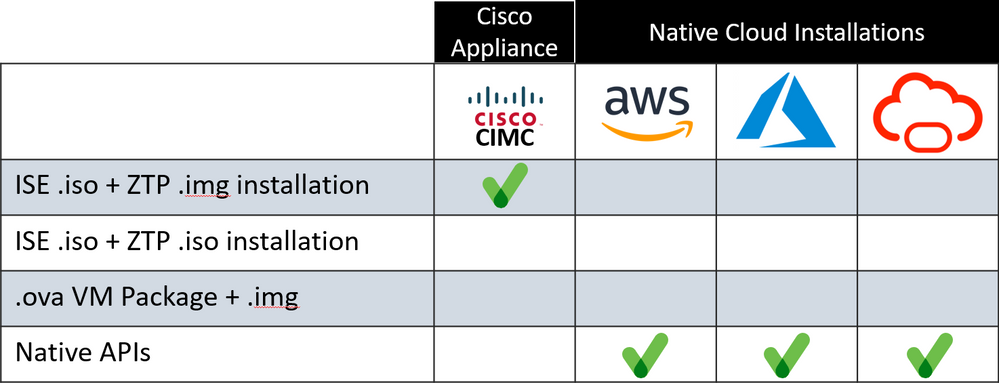
This table shows the methods I used to test the ZTP process on the different platforms. As of this writing, the Cisco Supported methods are only Cisco CIMC, VMware, AWS, Azure Cloud, and OCI, but I am hoping that changes soon. Note the red X in the Hyper-V column. This is explained in the section detailing Hyper-V installation, and is the reason that I had to add a row for ISE .iso + ZTP .iso installation, but that also allowed me to validate the .iso format for each on-prem patform.
ZTP was created with Cisco CIMC in mind and the use of the .img file for the ZTP configuration can be traced to this. The fact that the configuration MUST be a .img file for the CIMC process to work prompted its use in VMware. Since VMware and CIMC were the only platforms documented in the Installation Guide, and the .img file worked, there was no need to try other file types. That said, since the .img file is the Cisco Documented method and is referenced in the Installation Guide, it will be the default option used in this article. As you can see, the configuration as an .iso file works and can be used in any of the Virtual environments other than AWS.
The instructions for creating the .iso file rather than the .img file are in the Hyper-V section, since that is the only instance where it's required.
The minimum knowledge requirements to be able to use this guide are
- ISE installation practices
- Deploying Virtual Machines on your chosen platform (if applicable)
- Linux (RHEL, CentOS, or Ubuntu)
If you don't have access to a Linux system or cannot upgrade to vCenter 6.7U3j (6.7.0.45), but are on at least version 6.5, you can use the VM Data option. Yes, this option is a VMWare Only option, but that's due to the APIs that VMWare has exposed for use. You'll see that option at the bottom of this article in the section titled Installing ISE using OVA and VM Data (no ise-ztp.img file)
***The minimum versions noted for vCenter 6.7 are of my own experience and are NOT an official Cisco stance.***
Create ise-ztp.img file
Watch the video here:
Creating the ISE Zero Touch Provisioning (ZTP) Image File
The first process is the ZTP Configuration Image. This requires Access to a Linux system with sudo or root permissions. First we have to create the configuration file that will autocomplete the setup script for us.
The following is mandatory and must either be filled in or the line remarked (#) so it is ignored. Note that you can add ipv6 details, secondary and tertiary DNS and NTP servers.
ZTP Configuration for ISE 3.1
On August 26, 2022, new installation files for ISE 3.1 were uploaded to software.cisco.com containing an update to the ZTP process. The release notes for ISE 3.1 detail the changes and are shown in bold in the configuration below.
To identify whether you have the new "re-spin" of the installation media, the filenames of the new files will have "b" appended to the build number (for example, ise-3.1.0.518b.SPA.x86_64.iso and ISE-3.1.0.518b-virtual-SNS3615-SNS3655-300.ova)
hostname=<hostname of Cisco ISE>
ipv4_addr=<IPv4 address>
ipv4_mask=<IPv4 subnet>
ipv4_default_gw=<IPv4 gateway address>
#IPv6 optional
#ipv6_addr=<IPv6 address>
#ipv6_default_gw=<IPv6 gateway address>
domain=<cisco.com>
primary_nameserver=<IPv4 address>
#secondary and tertiary are optional
secondary_nameserver=<IPv4 address>
tertiary_nameserver=<IPv4 address>
primary_ntpserver=<IPv4 address or FQDN of the NTP server>
#secondary and tertiary are optional
secondary_ntpserver=<IPv4 address or FQDN of the NTP server>
tertiary_ntpserver=<IPv4 address or FQDN of the NTP server>
timezone=<timezone>
ssh=<true/false>
username=<admin> <--admin is the default for on-prem installations
password=<password># Skipping specific checks SkipIcmpChecks=true SkipDnsChecks=true SkipNtpChecks=true
*NOTE* - Only Plain password type is supported in the configuration file. Encrypted/hashed password in the key-value pair file for the ‘admin’ account is not supported.
This part of the configuration file goes beyond the setup script and REALLY saves time in a deployment. As you can see, you can create a repository, and from that repository, you can install a single patch and multiple hotpatches. The configuration file also allows for certain service to be enabled at the end of the installation.
#Repository Configuration are optional
repository_name=<repository name>
repository_protocol=<repository protocol>
repository_server_name=<IPv4 address>
repository_path=<repository path>
#Patch Information - optional
patch=<patch filename>
#HotPatches Information - optional
hotpatches=<hotpatch filename,comma separated list>
#services - optional
ers=<true/false>
openapi=<true/false>
pxgrid=<true/false>
pxGrid_Cloud=<true/false>
Only TFTP, HTTP, HTTPS and NFS repositories with no username/password are supported and the repository created during this script is not persistent, meaning that it will not exist in ISE after a reboot.
Note that I am installing Patch 1 for ISE 3.1 as well as the Log4jfix for 3.1 patch1. I've also enabled all of the optional services available through this configuration file.
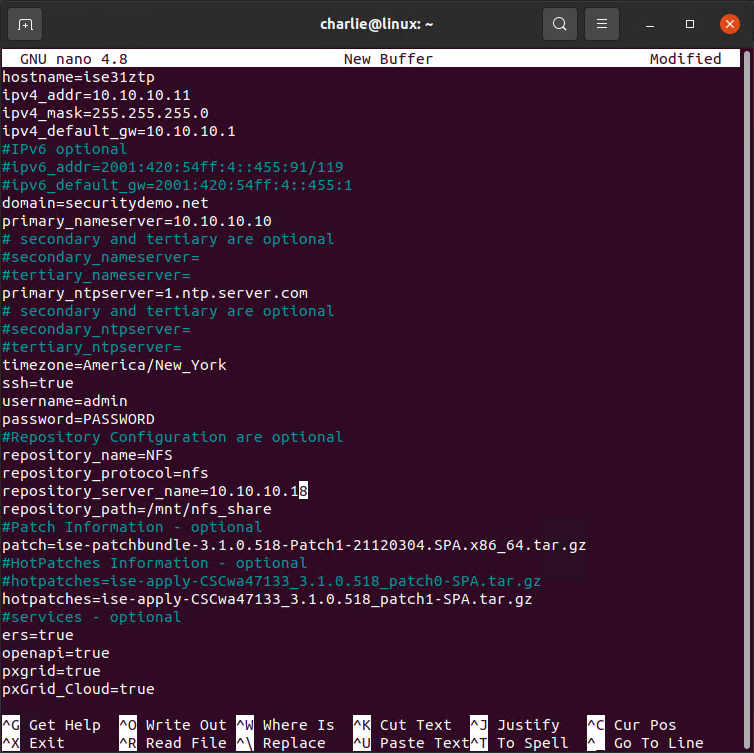
With all of these options, your full ISE 3.1 configuration file should look like this:
hostname=ise31ztp
ipv4_addr=10.10.100.11
ipv4_mask=255.255.255.0
ipv4_default_gw=10.10.10.1
#IPv6 optional
#ipv6_addr=2001:420:54ff:4::455:91/119
#ipv6_default_gw=2001:420:54ff:4::455:1
domain=securitydemo.net
primary_nameserver=10.10.10.10
# secondary and tertiary are optional
#secondary_nameserver=
#tertiary_nameserver=
primary_ntpserver=1.ntp.server.com
# secondary and tertiary are optional
#secondary_ntpserver=
#tertiary_ntpserver=
timezone=America/New_York
ssh=true
username=admin
password=PASSWORD
#Repository Configuration are optional
repository_name=NFS
repository_protocol=nfs
repository_server_name=10.10.10.18
repository_path=/mnt/nfs_share
#Patch Information - optional
patch=ise-patchbundle-3.1.0.518-Patch1-21120304.SPA.x86_64.tar.gz
#HotPatches Information - optional
#hotpatches=ise-apply-CSCwa47133_3.1.0.518_patch0-SPA.tar.gz
hotpatches=ise-apply-CSCwa47133_3.1.0.518_patch1-SPA.tar.gz
#services - optional
ers=true
openapi=true
pxgrid=true
pxGrid_Cloud=true
*NOTE* - Take care to ensure that the entry for the patch is "patch" - singular, while the entry for hotpatches is the plural, "hotpatches". Patch/hotpatch installation will fail if this is incorrect.
ZTP Configuration for ISE 3.2 and newer
hostname=<hostname of Cisco ISE>
ipv4_addr=<IPv4 address>
ipv4_mask=<IPv4 subnet>
ipv4_default_gw=<IPv4 gateway address>
#IPv6 optional
#ipv6_addr=<IPv6 address>
#ipv6_default_gw=<IPv6 gateway address>
domain=<cisco.com>
primary_nameserver=<IPv4 address>
#secondary and tertiary are optional
secondary_nameserver=<IPv4 address>
tertiary_nameserver=<IPv4 address>
primary_ntpserver=<IPv4 address or FQDN of the NTP server>
#secondary and tertiary are optional
secondary_ntpserver=<IPv4 address or FQDN of the NTP server>
tertiary_ntpserver=<IPv4 address or FQDN of the NTP server>
timezone=<timezone>
ssh=<true/false>
username=<admin> <--admin is the default for on-prem installations
password=<password>
#Public Key Authentication configuration is optional
public_key=<Public Key>
#Repository Configuration are optional
repository_name=<repository name>
repository_protocol=<repository protocol>
repository_server_name=<IPv4 address>
repository_path=<repository path>
#Patch Information - optional
patch=<patch filename>
#HotPatches Information - optional
hotpatches=<hotpatch filename,comma separated list>
#services - optional
ers=<true/false>
openapi=<true/false>
pxgrid=<true/false>
pxGrid_Cloud=<true/false>
#Skipping specific checks
SkipIcmpChecks=<true/false>
SkipDnsChecks=<true/false>
SkipNtpChecks=<true/false>
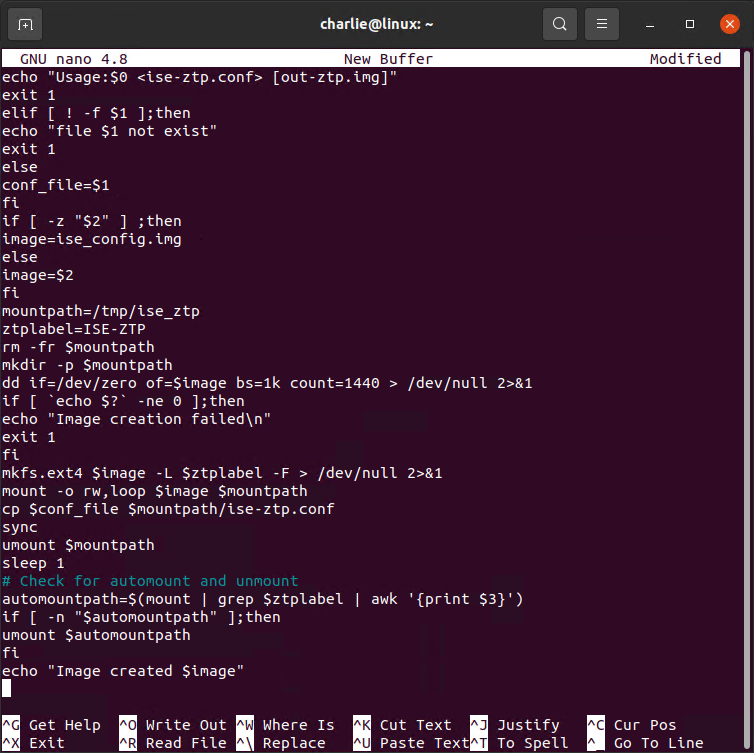
I usually stage this in a text editor on my Ubuntu VM. The next step it to grab the ZTP script from the ISE Installation Guide for your version. I've pasted it here for you:
#!/bin/bash
###########################################################
# This script is used to generate ise ztp image with ztp
# configuration file.
#
# Need to pass ztp configuration file as input.
#
# Copyright (c) 2021 by Cisco Systems, Inc.
# All rights reserved.
# Note:
# To mount the image use below command
# mount ise_ztp_config.img /ztp
# To mount the image from cdrom
# mount -o ro /dev/sr1 /ztp
#############################################################
if [ -z "$1" ];then
echo "Usage:$0 <ise-ztp.conf> [out-ztp.img]"
exit 1
elif [ ! -f $1 ];then
echo "file $1 not exist"
exit 1
else
conf_file=$1
fi
if [ -z "$2" ] ;then
image=ise_config.img
else
image=$2
fi
mountpath=/tmp/ise_ztp
ztplabel=ISE-ZTP
rm -fr $mountpath
mkdir -p $mountpath
dd if=/dev/zero of=$image bs=1k count=1440 > /dev/null 2>&1
if [ `echo $?` -ne 0 ];then
echo "Image creation failed\n"
exit 1
fi
mkfs.ext4 $image -L $ztplabel -F > /dev/null 2>&1
mount -o rw,loop $image $mountpath
cp $conf_file $mountpath/ise-ztp.conf
sync
umount $mountpath
sleep 1
# Check for automount and unmount
automountpath=$(mount | grep $ztplabel | awk '{print $3}')
if [ -n "$automountpath" ];then
umount $automountpath
fi
echo "Image created $image"
Once you have this script where you can paste it in your Linux system, open your favorite command-line text editor in Linux. I use nano, it's simple to use and utilizes easy to remember keyboard shortcuts.
Open nano
nano
Paste in the script from above
Ctrl+X to Exit
nano will ask if you want to save the file (at the bottom of the screen), enter Y
Save the file as
create_ztp_image.sh
Make this script executable by using the command
chmod +x create_ztp_image.sh
Open nano again and paste the configuration file
Ctrl+X to exit, Save the file as
ise-ztp.conf
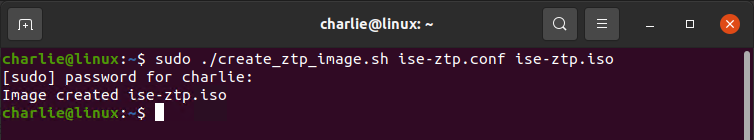
Now that you have the executable script and the configuration file, you can create the .img file. Issue the following command (this is where I hit my first stumbling block. All the ZTP documentation I found had no mention of 'sudo' for this command. This led to a bad .img file every time I tried to create it. Once I used the 'sudo' command, the file was perfect).
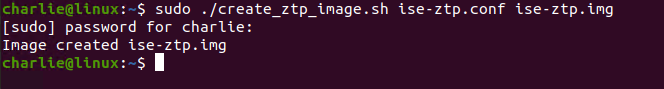
sudo ./create_ztp_image.sh ise-ztp.conf ise-ztp.img
You should receive confirmation of the ise-ztp.img file creation as seen here:
Great! Now you can use this .img file to install ISE 3.1. There are two methods for the ise-ztp.img script. The first is mounting the script as well as the ISE 3.1 .iso file. The second is mounting the ise-ztp.img after installation which you'll see as you continue reading.
Installing ISE using ise-ztp.img
Cisco SNS CIMC Installation
Watch the video here:
Install ISE on Cisco SNS through the CIMC using ZTP
Fist off, here are a few notes about the CIMC ZTP process:
-
ZTP works on the SNS appliance through Virtual Media only.
-
You must map the .img file in Virtual Media before mapping the ISO file.
-
Automatic installation in appliance is supported only with the .img file format.
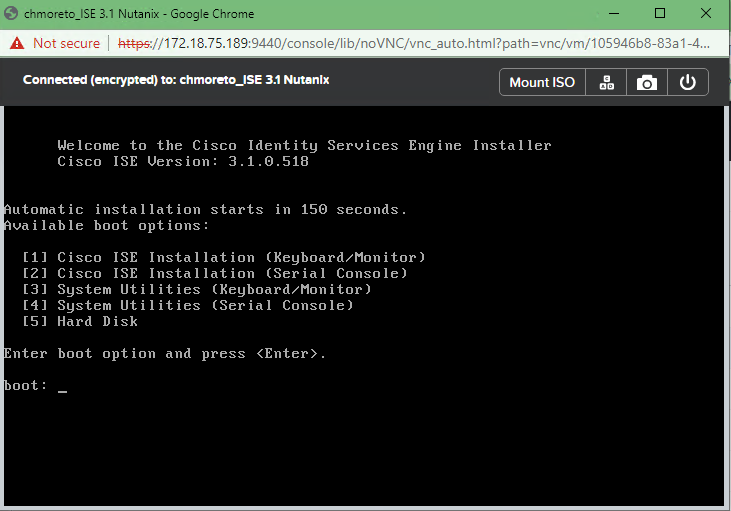
- Installation logs can be monitored through the serial console as ZTP works only through the serial console. It can be monitored from the KVM console after the setup prompt is displayed.
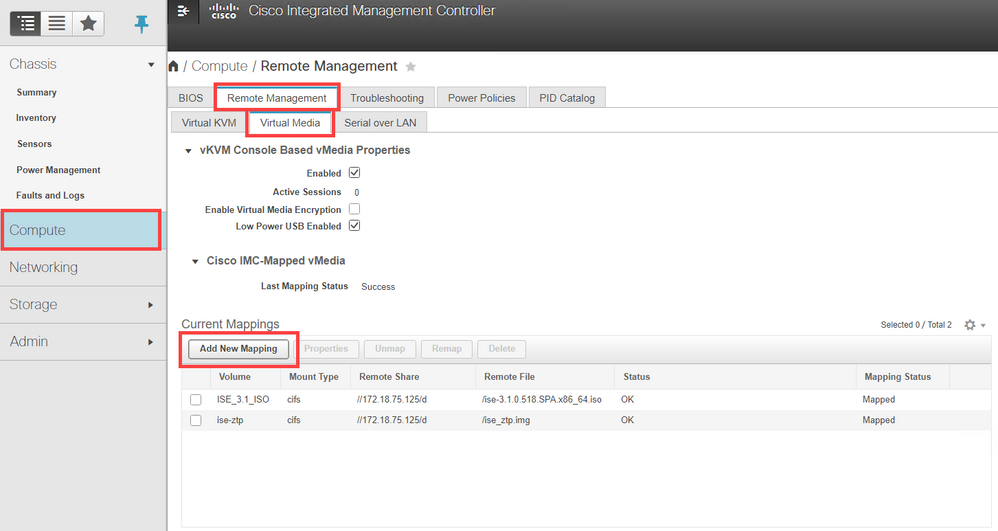
Now that we have that, log in to the CIMC and Navigate to Compute > Remote Management > Virtual Media. Click on Add New Mapping and add the .img file you created. Then add the ISE 31 ISO.
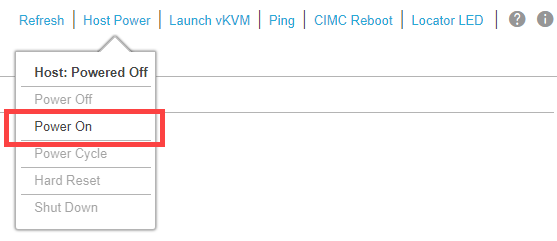
Next, Power On the SNS Server by going the Host Power > Power On.
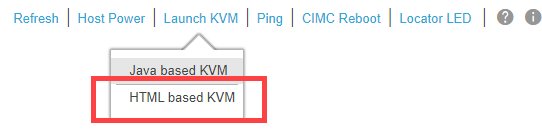
Then you can Launch vKVM > HTML based KVM. I use the HTML KVM as it's a touch faster and a better experience. The Java based KVM is deprecated in the newer versions of CIMC Firmware, so you may not even get the menu here, the system will just launch the HTML based KVM in the newer versions.
In the vKVM window, you can watch as the system boots. to ensure that the system boots to the Mapped Virtual Media, press F6 to enter the Boot Menu on this screen
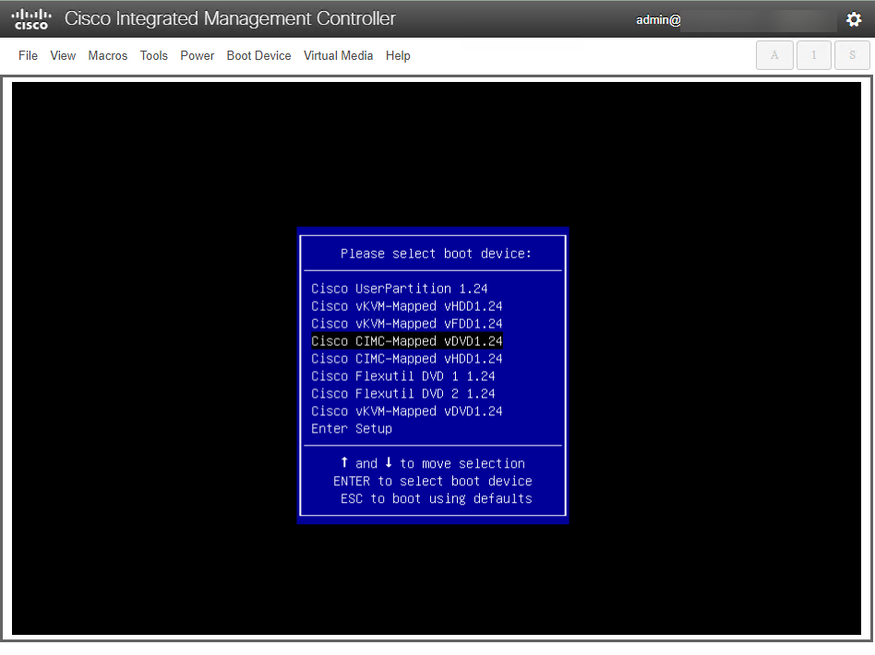
In the Boot Menu, you want to select the Cisco CIMC-Mapped vDVD. This process does not work with vKVM-Mapped DVD.
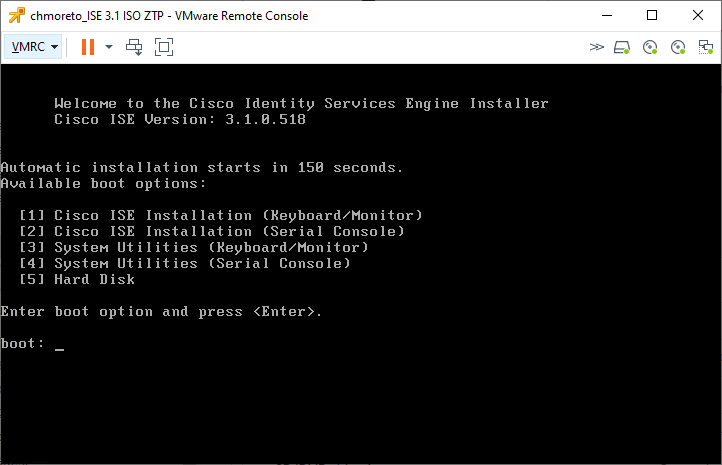
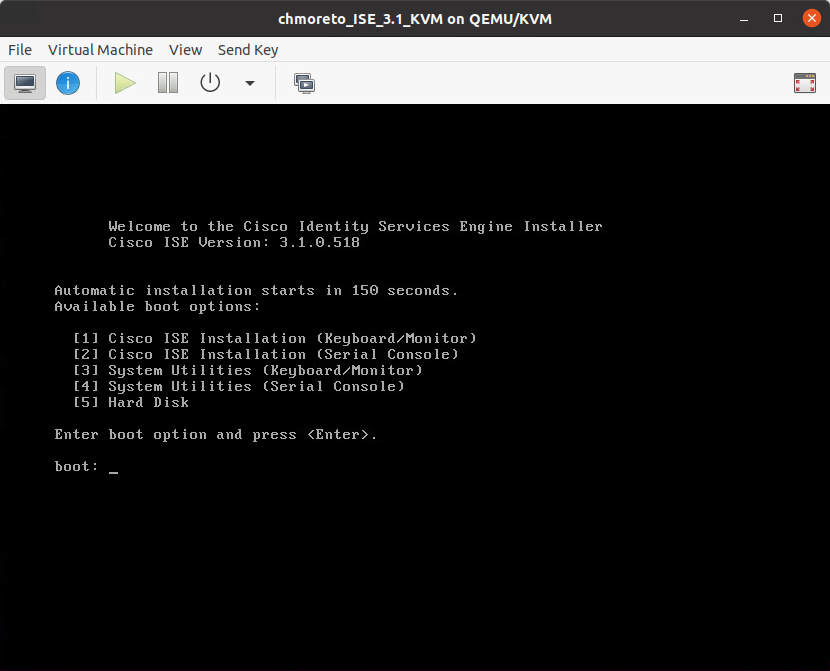
Here you will see the following Boot Options, the last one is the default and will be automatically selected after 150 seconds
Again, remember that installation logs can be monitored through the serial console as ZTP works only through the serial console. It can be monitored from the KVM console after the setup prompt is displayed.
Once the 'setup' prompt is displayed, you will see......
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the server will reboot. Now you can Verify ZTP configuration after installation.
VMWare vCenter ISO Installation
Watch the video here:
Using 4 Different Methods to Install ISE on VMware vCenter using ZTP
To deploy a vCenter VM using the ZTP method and installing ISE with an ISO, ensure that you are on at least vCenter version 6.7U3j (6.7.0.45) and then follow these steps.
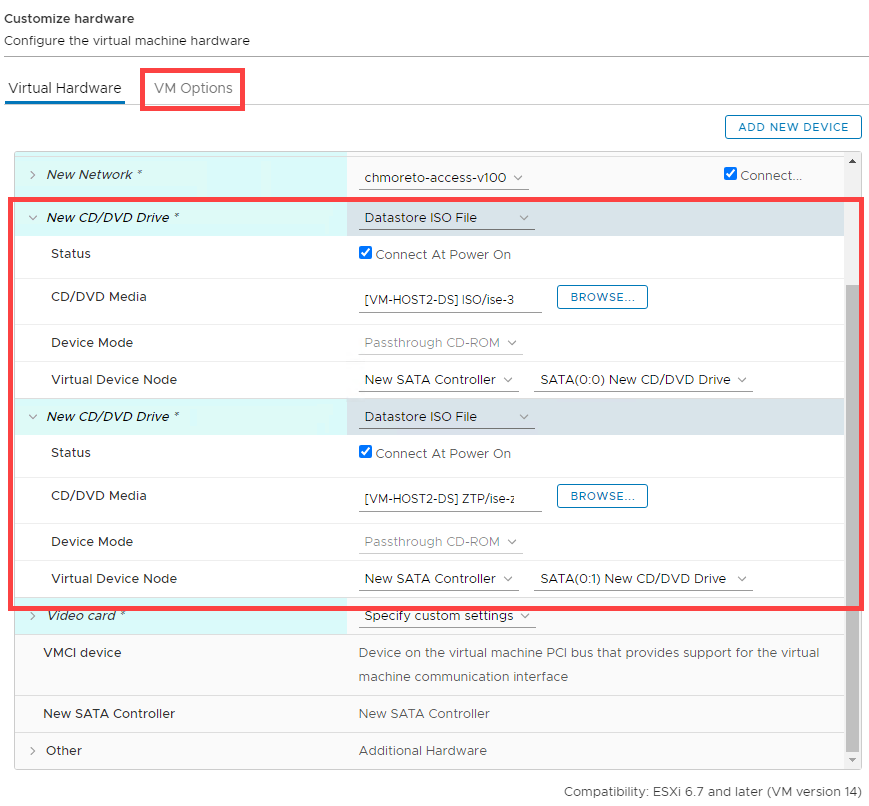
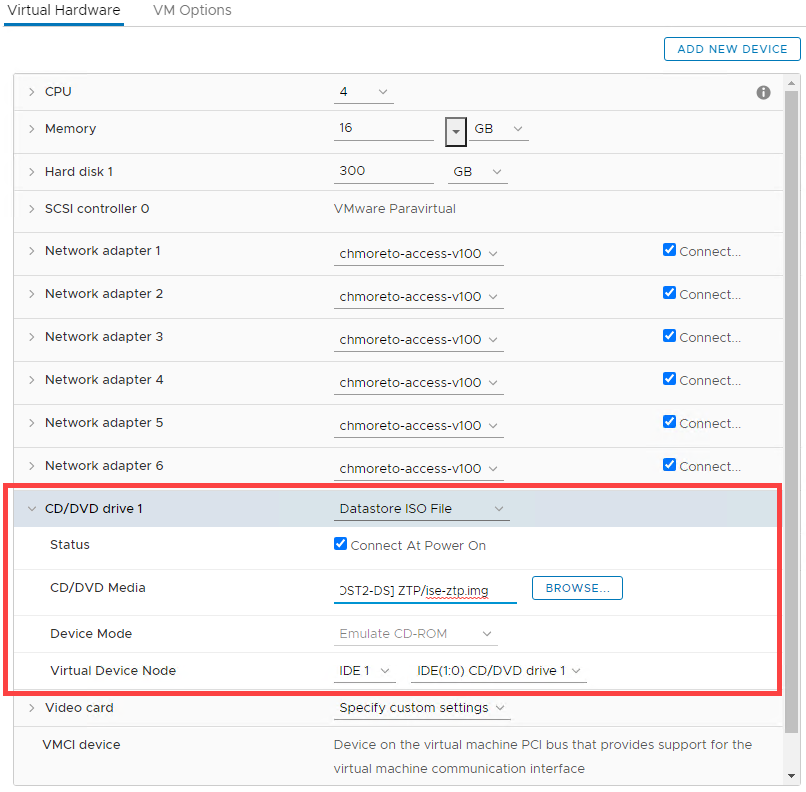
Upload the ISE 3.1 .iso and the ise-ztp.img files to the VMWare datastore. When creating the VM, make sure to add the following:
- Add New Device > CD/DVD Drive
- Expand the first CD/DVD Drive,
- Select Datastore ISO File > Choose the ISE 3.1 .iso File, select Connect At Power On
- Expand the second CD/DVD Drive
- Select Datastore ISO File > Choose the ise-ztp.img File, select Connect At Power On
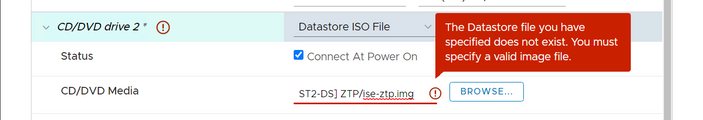
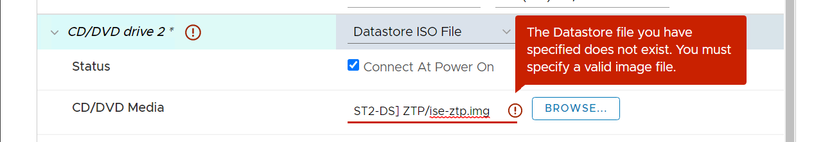
If you get the following error when adding the .img file, check your vCenter version.
I was using vCenter 6.7U3f (6.7.0.43) and encountered this error. I couldn't get the ISO/img process to complete no matter what I tried. After working with the engineering team, I found that they are using vCenter 6.7U3j (6.7.0.45) to test the settings. Once I upgraded (to vCenter 6.7U3p [6.7.0.51]), I was also able to get it to work as expected. This is the reason for the minimum version noted at the beginning of this section.
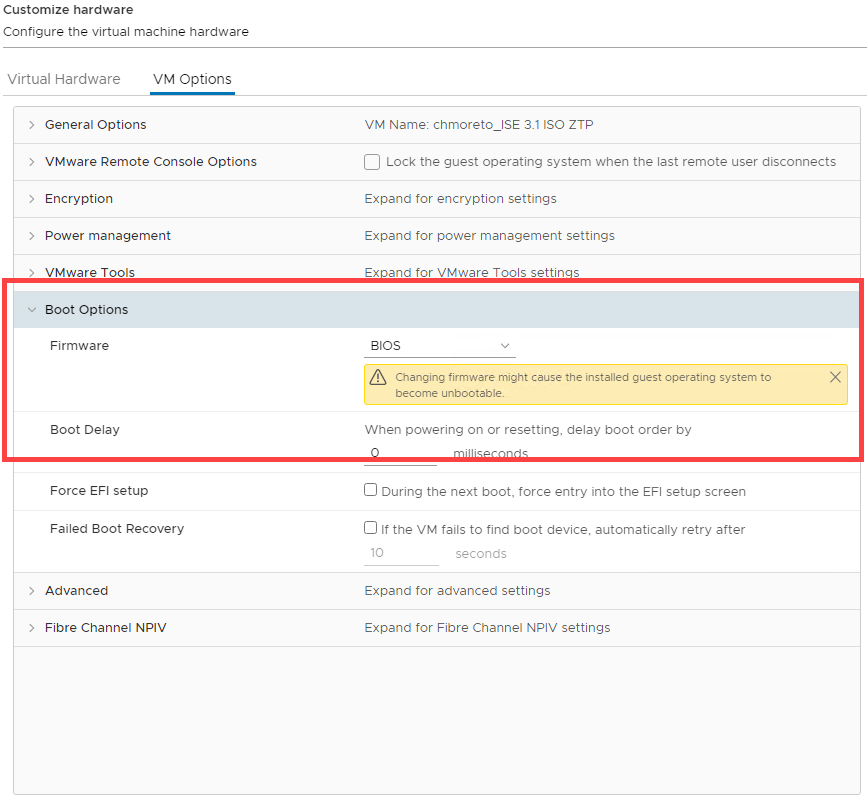
On the Customize Hardware screen, click VM Options. Expand Boot Options and change Firmware to BIOS.
Finish deploying the VM and power it on.
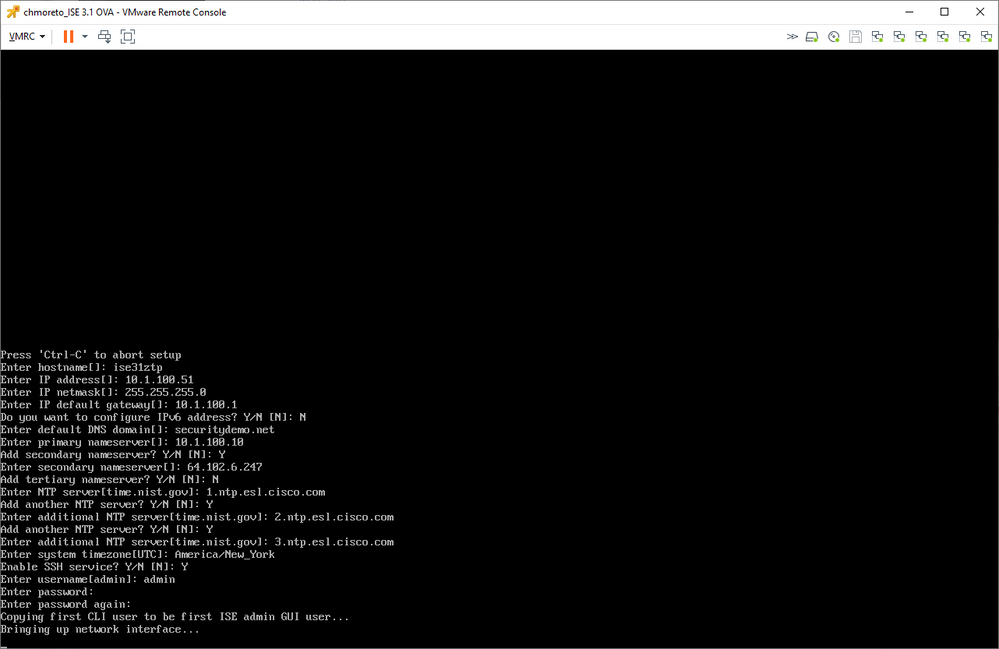
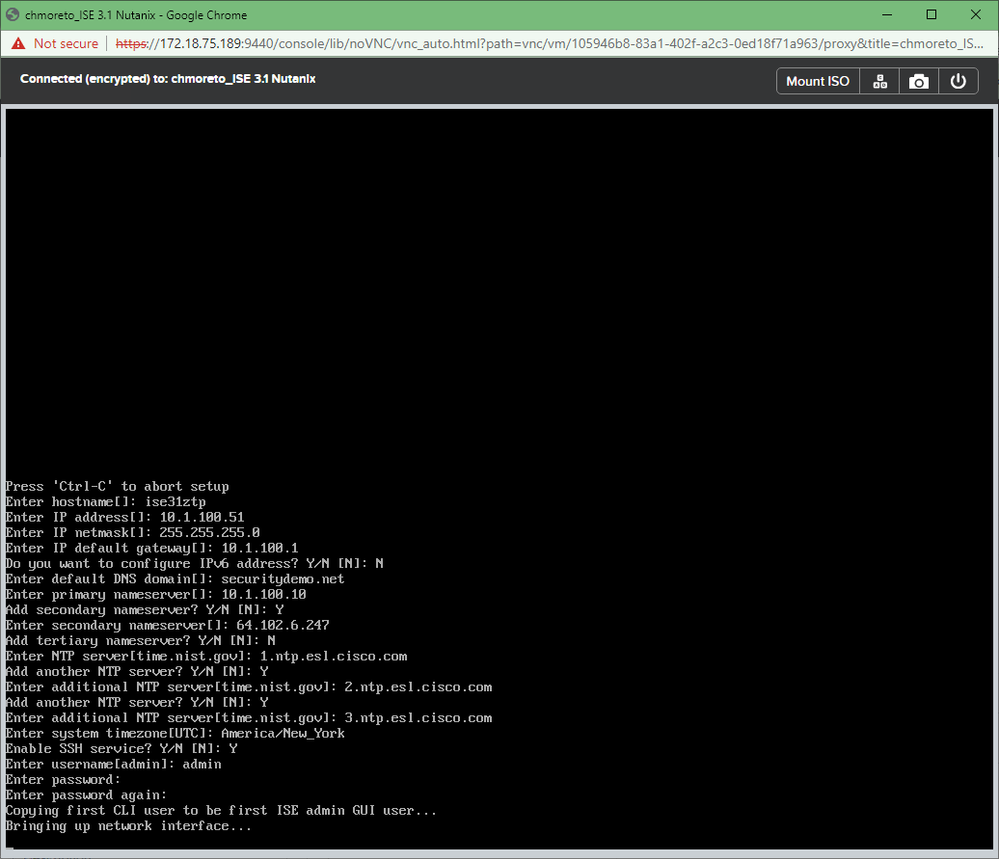
Though it doesn't say it, the default option here is the ZTP installation and it will automatically start after 150 seconds. Once the ISO portion of the installation completes, you will be presented with the setup prompt. It's not there long.
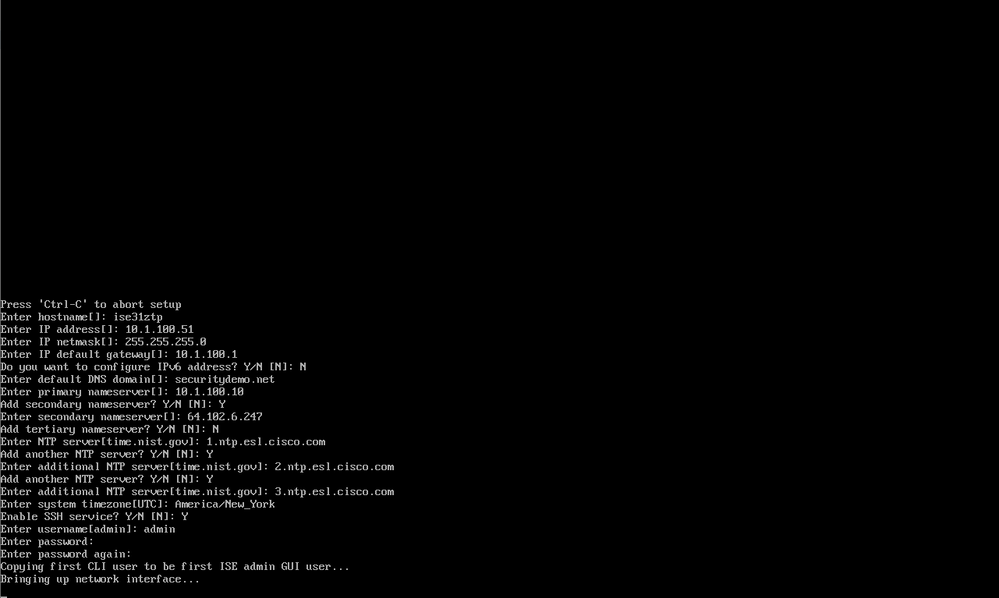
Followed quickly by this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
VMWare vCenter OVA Installation
Should you want to deploy your VMs using the OVA files that Cisco provides, you can certainly do so, just make sure you are using at least vCenter 6.7U3j (6.7.0.45) . Upload the ise-ztp.img file to the datastore and deploy the VM. Once the VM is provisioned in your vCenter, and before you power it on, Edit Settings of the VM and add expand the CD/DVD drive, select Datastore ISO File and choose the ise-ztp.img file. Enable Connect At Power On and click OK.
If you get the following error when adding the .img file, check your vCenter version.
I was using vCenter 6.7U3f (6.7.0.43) and encountered this error. I couldn't get the ISO/img process to complete no matter what I tried. After working with the engineering team, I found that they are using vCenter 6.7U3j (6.7.0.45) to test the settings. Once I upgraded (to vCenter 6.7U3p [6.7.0.51]), I was also able to get it to work as expected. This is the reason for the minimum version noted at the beginning of this section.
Power on the VM and as soon as the 'setup' prompt appears, you will see this screen
Followed quickly by this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
Nutanix CE ISO Installation
Watch the video here:
Installing ISE on Nutanix Community Edition (CE) using ZTP
The ISE 3.1 Installation Guide shows that the supported version of the Nutanix AHV Hypervisor is 20201105.2096, but the latest stable release of the Nutanix CE AHV Hypervisor is 20190916.276, so that's what I'm using. The noteworthy version, though is that the Nutanix Hypervisor to be used is their AHV Hypervisor.
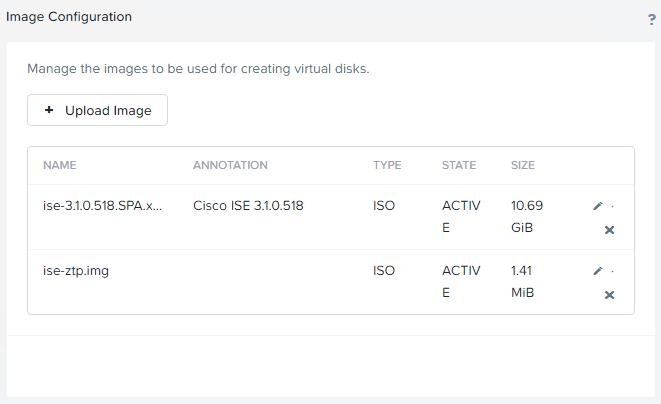
Let's get started. First, upload the ISE 3.1 .iso and the ise-ztp.img files to the Image Configuration. Note that the ise-ztp.img file is set as Type=ISO
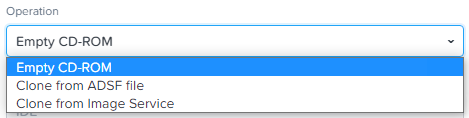
Then we can create the VM. Add the ISE 3.1 ISO in the first CD-ROM (ise.0). Choose the Clone from Image Service selection from the Operation dropdown.
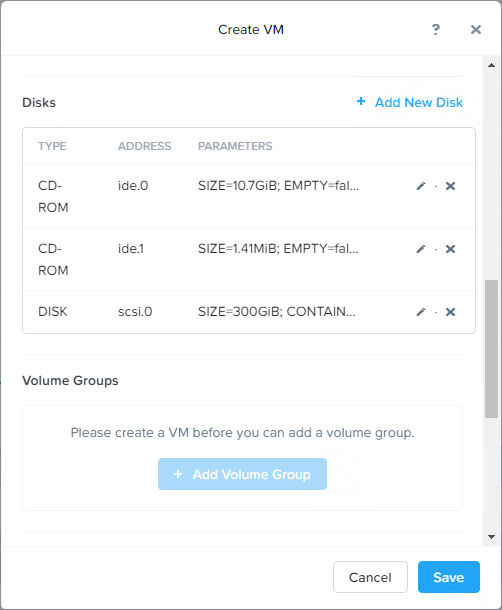
Click +Add New Disk. Add the ise-ztp.img as Type CD-ROM and Clone from Image Service for this file, as well. Also add the HD for the ISE installation, Networking and any other settings you need. Click Save.
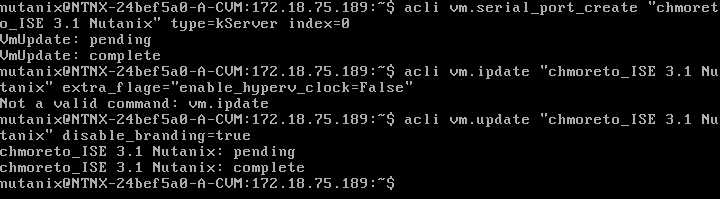
*NOTE* - BEFORE YOU POWER ON this VM, you MUST ssh into the CVM (any CVM in the Nutanix cluster) and issue the following commands. ISE will not install on Nutanix AHV without these commands. You must do this for every ISE VM.
acli vm.serial_port_create <vmName> type=kServer index=0
acli vm.update <vmName> extra_flags=”enable_hyperv_clock=False”
acli vm.update <vmName> disable_branding=true
Power on the VM, open the VNC Console, and you will see the boot menu.
Though it doesn't say it, the default option here is the ZTP installation and it will automatically start after 150 seconds.
Once the ISO portion of the installation completes, you will be presented with the setup prompt. It's not there long, then you will see this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
Microsoft Hyper-V ISO Installation
Watch the video here:
Installing ISE on Microsoft Hyper-V with ZTP
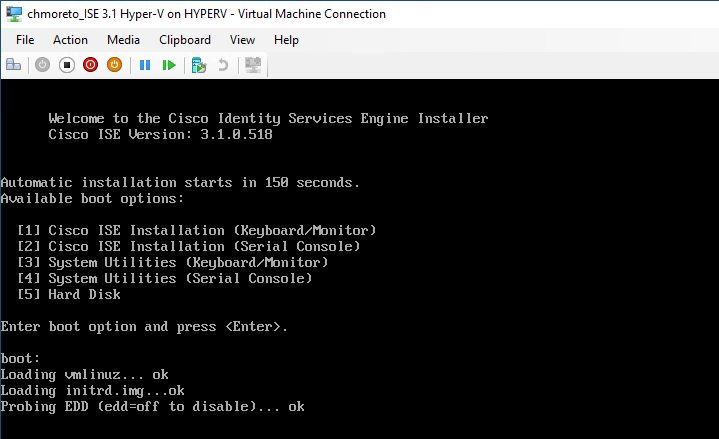
Microsoft does not allow for a .img file to be mounted in a virtual DVD Drive, and their only format for virtual floppy drive images is .vfd. I converted the .img file to a .vfd file and it did not work. Not only did it not work, the Hyper-V console for my ISE VM was stuck on this screen for over 3 hours. The ISE installation does NOT like the use of floppy drives!
Now that I know this, I went back to my linux workstation and issued the following command to create an .iso of the configuration file. (After this worked, I tried the same command to create a .vfd file, but that still failed)
sudo ./create_ztp_image.sh ise-ztp.conf ise-ztp.iso
You should receive confirmation of the ise-ztp.iso file creation as seen here:
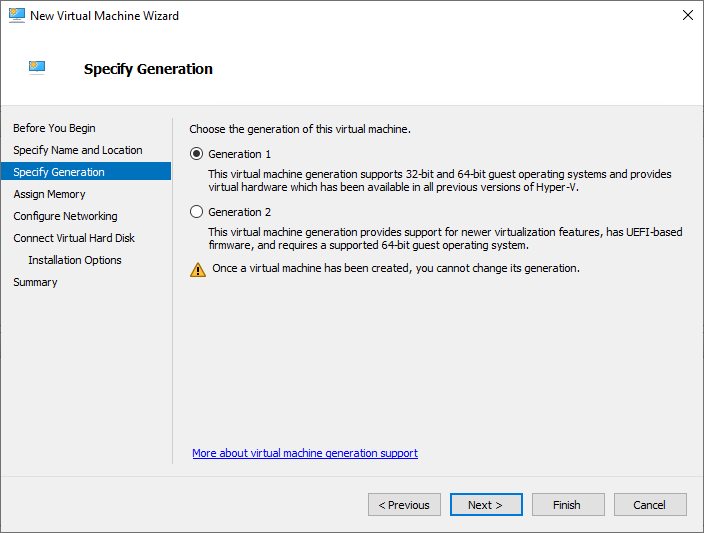
Armed with the newly created ise-ztp.iso file, you can create the VM and install ISE. When creating the Virtual Machine for ISE, be certain to specify that you want a Generation 1 virtual machine. This will default to a BIOS firmware instead of the UEFI-based firmware. It also allows for 32-bit and 64-bit processes and LEGACY Virtual Hardware, which is needed to mount the ISO file successfully.
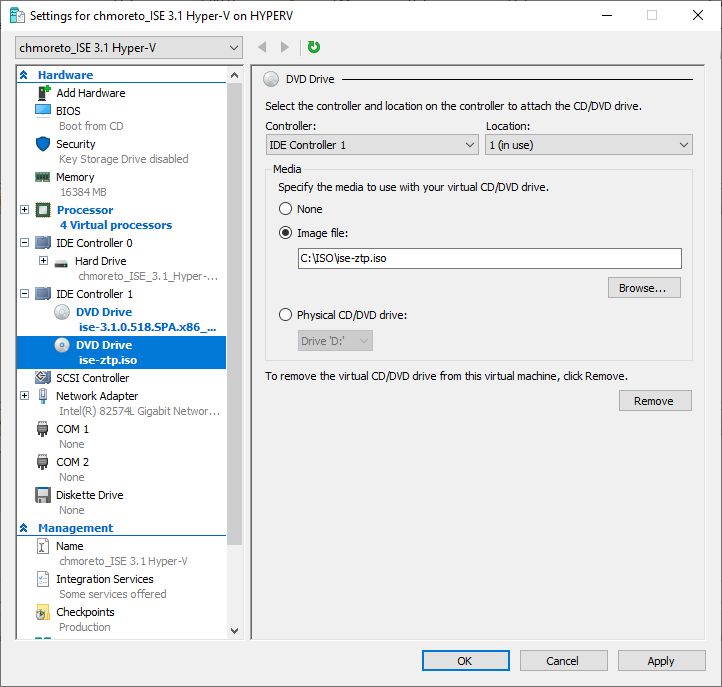
Once your virtual machine is created, open the Settings window before you power it on. Select the IDE Controller and Add a new DVD Drive. Mount the ISE 3.1 ISO into the primary drive and the ise-ztp.iso into the secondary (Location = 1)
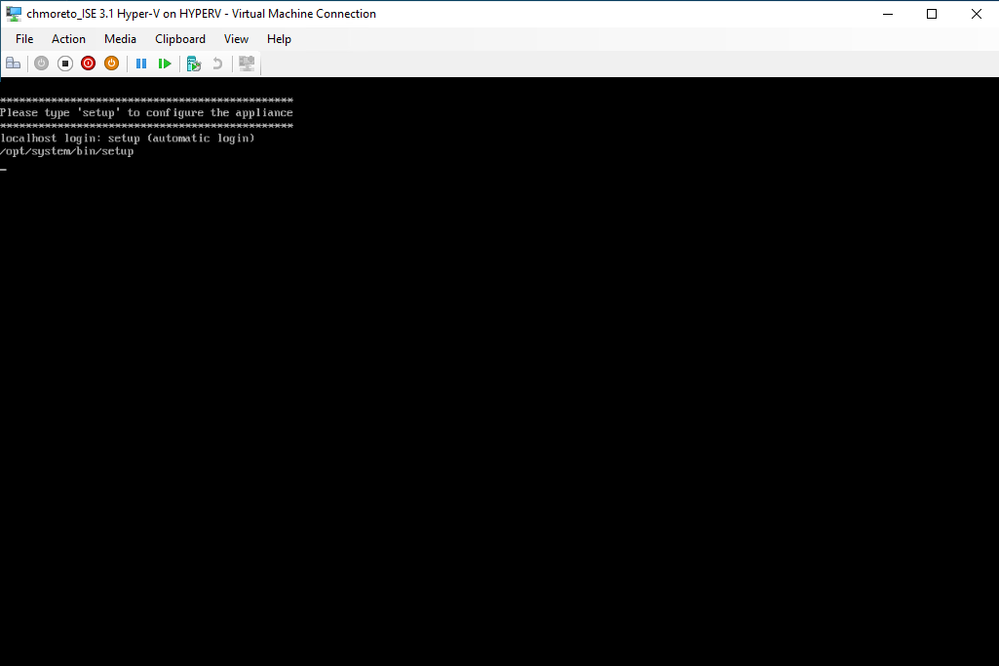
Click OK and power on the Virtual Machine, as soon as the 'setup' prompt appears, you will see this screen
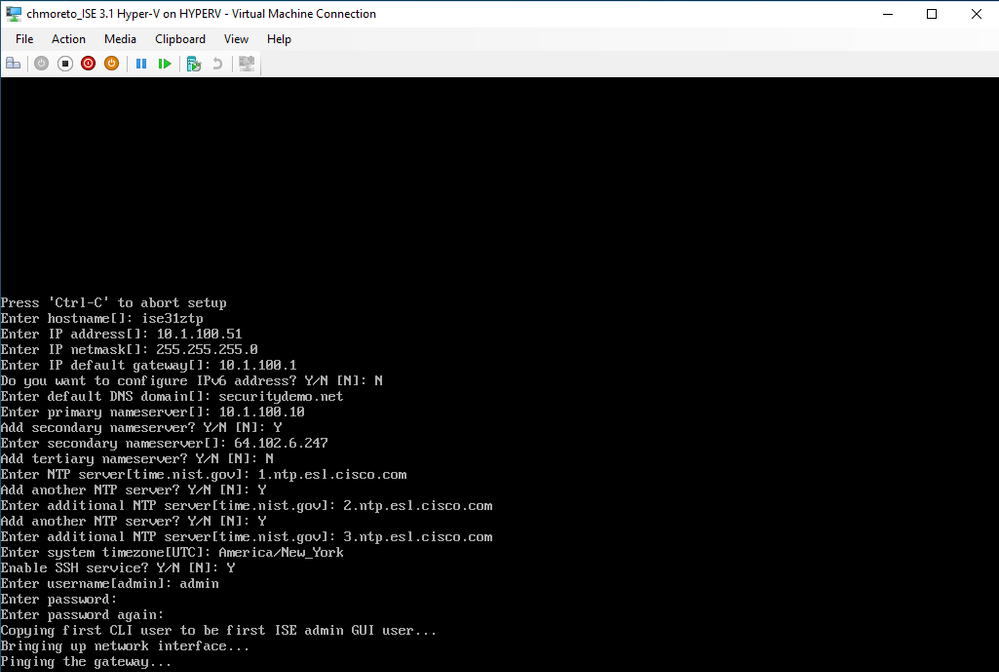
Followed quickly by this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
Linux KVM ISO Installation
Watch the video here:
Installing ISE on Ubuntu Linux KVM using ZTP
I used Ubuntu 20.04.3 with Virtual Machine Manager in my environment, though most Linux distros will have the framework for KVM. You can choose to use the command-line to interface with the VMs, but I chose to use a graphical interface. There are many to choose, I chose the one that seemed to be used a lot.
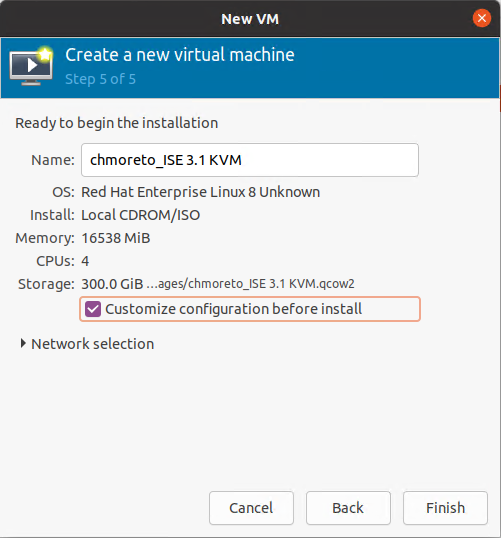
When creating the Virtual Machine, enable Customize configuration before install to add the secondary DVD Drive
Click the Add Hardware button and select CDROM, in the details of SATA CDROM1, map the ISE installation ISO file, in the details of SATA CDROM2, map the ise-ztp.img file and click Begin Installation. Open the console and you will see the boot menu.
Though it doesn't say it, the default option here is the ZTP installation and it will automatically start after 150 seconds.
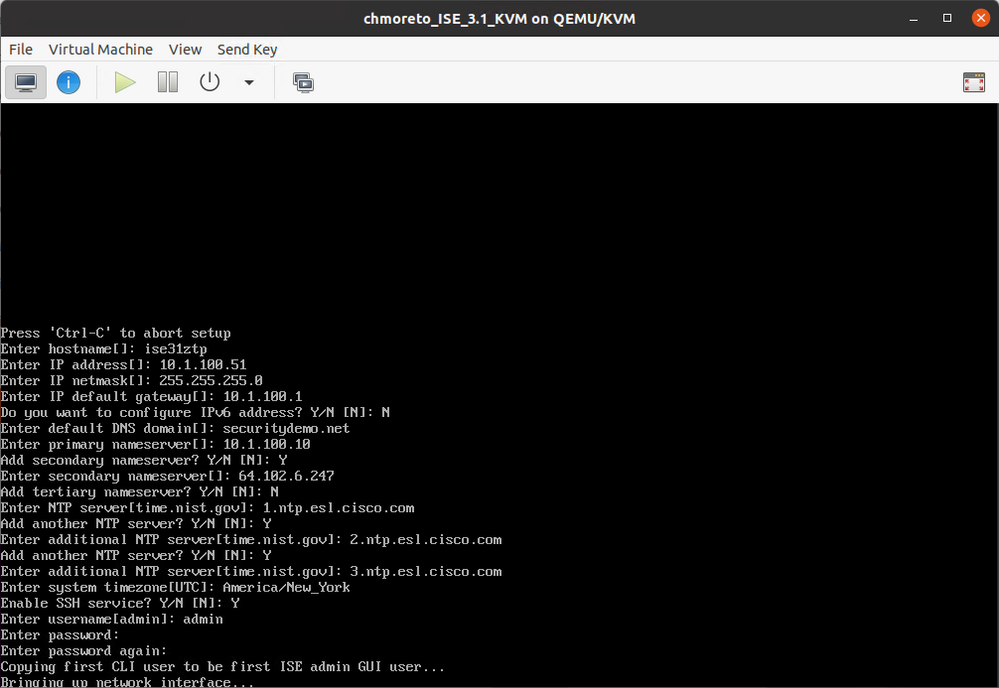
Once the ISO portion of the installation completes, you will be presented with the setup prompt. It's not there long, then you will see this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
Installing ISE using OVA and VM Data (no ise-ztp.img file)
Watch the video here:
Using 4 Different Methods to Install ISE on VMware vCenter using ZTP (Starts at VM Data)
If you don't have access to a Linux system or cannot upgrade to vCenter 6.7U3j (6.7.0.45), but are on at least vCenter version 6.5, you can use the VM Data option.
Provision the OVA file to vCenter. Stage your configuration file in notepad with all the settings you want.
hostname=ise31ztp
ipv4_addr=10.10.100.11
ipv4_mask=255.255.255.0
ipv4_default_gw=10.10.10.1
#IPv6 optional
#ipv6_addr=2001:420:54ff:4::455:91/119
#ipv6_default_gw=2001:420:54ff:4::455:1
domain=securitydemo.net
primary_nameserver=10.10.10.10
# secondary and tertiary are optional
#secondary_nameserver=
#tertiary_nameserver=
primary_ntpserver=1.ntp.server.com
# secondary and tertiary are optional
#secondary_ntpserver=
#tertiary_ntpserver=
timezone=America/New_York
ssh=true
username=admin
password=PASSWORD
#Repository Configuration are optional
repository_name=NFS
repository_protocol=nfs
repository_server_name=10.10.10.18
repository_path=/mnt/nfs_share
#Patch Information - optional
patch=ise-patchbundle-3.1.0.518-Patch1-21120304.SPA.x86_64.tar.gz
#HotPatches Information - optional
#hotpatches=ise-apply-CSCwa47133_3.1.0.518_patch0-SPA.tar.gz
hotpatches=ise-apply-CSCwa47133_3.1.0.518_patch1-SPA.tar.gz
#services - optional
ers=true
openapi=true
pxgrid=true
pxGrid_Cloud=true
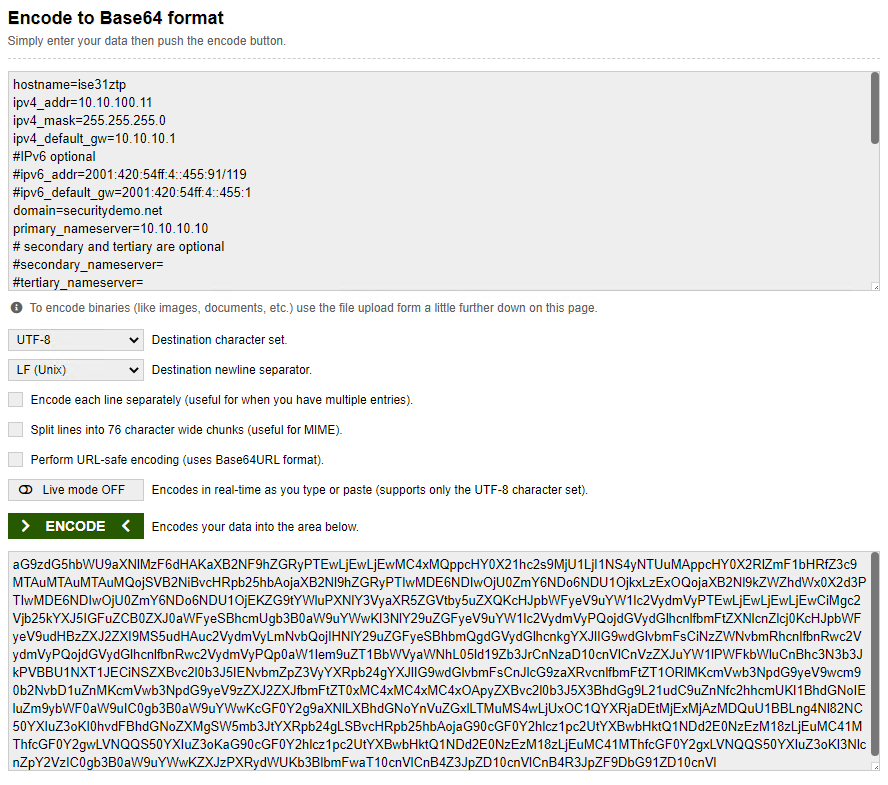
To use VM Data, we need to encode the configuration file to Base64 format. Copy the data from the text file and go to
Paste the configuration in to the top text window, leave the settings at their defaults and click the ENCODE button
Copy ALL the text from the encode window, edit settings of your VM, click VM Options, expand Advanced and click EDIT CONFIGURATION...
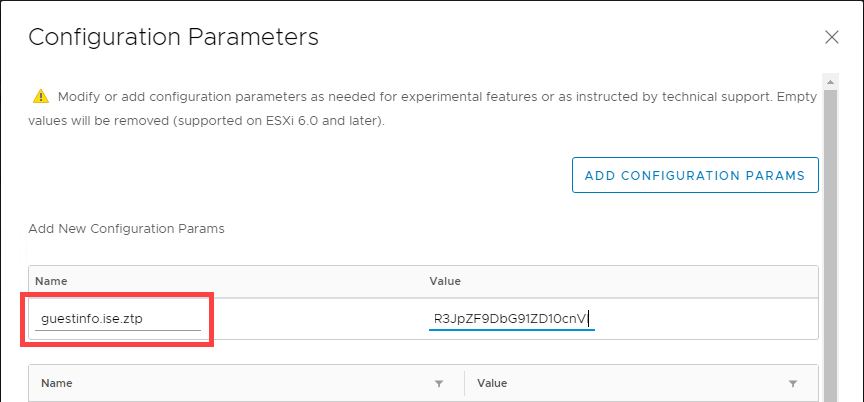
Then choose ADD CONFIGURATION PARAMS
A new section will appear. the Name MUST be guestinfo.ise.ztp - any other name and this new parameter will be ignored. Paste the Base64 encoded text string into the Value field.
Click OK, and power on the VM. As soon as the 'setup' prompt appears, you will see this screen
Followed quickly by this screen with the configuration items already filled.
Once this process finishes (it WILL take a bit longer - remember we are installing Patch 1 AND the Log4j fix before the final reboot) the VM will reboot. Now you can Verify ZTP configuration after installation.
Public Cloud Installations
For step-by-step instructions to install ISE on the supported Public Cloud Platforms, please visit Deploy Cisco ISE Natively on Cloud Platforms .
Be sure to note that beginning with ISE 3.2, ALL cloud platforms will assign a default username of ise admin to ISE installations. This cannot be changed, and adding a username to the User Data will be ignored.
Cloud Platforms ZTP Configuration Format
All cloud platforms use the same format for their ZTP configuration data. Note that the options for cloud platforms are more limited.
hostname=<hostname of Cisco ISE>
primarynameserver=<IPv4 address>
dnsdomain=<example.com>
ntpserver=<IPv4 address or FQDN of the NTP server>
timezone=<timezone>
password=<password>
ersapi=<yes/no>
openapi=<yes/no>
pxGrid=<yes/no>
pxgrid_cloud=<yes/no>
Amazon Web Services (AWS)
Installation on AWS is supported in ISE 3.1 and newer.
When provisioning an AMI instance of ISE on AWS, the Configure Instance Details page will have a radio button for User Data in the Advanced Details area. Select this and use the configuration file format from above to enter the details.
Microsoft Azure Cloud
Installation on Azure Cloud is supported in ISE 3.2 and newer.
When provisioning an ISE instance of ISE on Azure Cloud, the Advanced page will have a check box for
Oracle Cloud Infrastructure (OCI)
Installation on OCI is supported in ISE 3.2 and newer.
When provisioning an ISE instance of ISE on OCI, after inputting the SSH Keys and setting the Boot Volume size, click the Show advanced options link to expand that section. Choose the Management tab and select the Paste cloud-init script radio button. Use the configuration file format from above to enter the details.
Verify ZTP configuration after Installation
To verify the setup script entries are all configured correctly, a show running-config (sh run) will let you see them all. The entries in bold are set by the ZTP configuration.
ise31ztp/admin# sh run
Generating configuration...
!
hostname ise31ztp
!
ip domain-name securitydemo.net
!
ipv6 enable
!
interface GigabitEthernet 0
ip address 10.1.100.51 255.255.255.0
ipv6 address autoconfig
ipv6 enable
!
interface GigabitEthernet 1
shutdown
ipv6 enable
!
interface GigabitEthernet 2
shutdown
ipv6 enable
!
interface GigabitEthernet 3
shutdown
ipv6 enable
!
interface GigabitEthernet 4
shutdown
ipv6 enable
!
interface GigabitEthernet 5
shutdown
ipv6 enable
!
ip name-server 10.1.100.10 64.102.6.247
!
ip default-gateway 10.1.100.1
!
!
clock timezone America/New_York
!
ntp server 1.ntp.esl.cisco.com
ntp server 2.ntp.esl.cisco.com
ntp server 3.ntp.esl.cisco.com
!
username admin password hash $6$yfx58ck04N79TGMZ$aYT.464.22eH9IJJYKIHqjr59hnbYfQ9RNc6vwBFNXvWWXlcQYh1wbFSr268yc30W0M/bPkWQGrPhr9/.ExRE. role admin
!
!
service sshd enable
service sshd encryption-algorithm aes128-gcm@openssh.com chacha20-poly1305@openssh.com aes256-gcm@openssh.com aes128-ctr aes256-ctr
!
password-policy
lower-case-required
upper-case-required
digit-required
no-username
no-previous-password
password-expiration-enabled
password-expiration-days 45
password-expiration-warning 30
min-password-length 4
password-lock-enabled
password-lock-timeout 15
password-lock-retry-count 3
!
logging loglevel 6
!
conn-limit 5 port 9061
conn-limit 30 port 9060
!
!
icmp echo on
!
ise31ztp/admin#
To verify the optional installation of the patch and/or hotpatch, the show version history command will show you both
ise31ztp/admin# show version history
---------------------------------------------
Install Date: Fri Jan 28 16:54:22 EST 2022
Application: ise
Version: 3.1.0.518
Install type: Application Install
Bundle filename: ise.tar.gz
Repository: SystemDefaultPkgRepos
---------------------------------------------
Install Date: Fri Jan 28 17:50:18 EST 2022
Application: ise
Version: 1
Install type: Patch Install
Bundle filename: ise-patchbundle-3.1.0.518-Patch1-21120304.SPA.x86_64.tar.gz
Repository: NFS
---------------------------------------------
Install Date: Fri Jan 28 17:59:00 EST 2022
Application: Apply_CSCwa47133_3.1.0.518_patch1
Version: 1
Install type: Application Install
Bundle filename: ise-apply-CSCwa47133_3.1.0.518_patch1-SPA.tar.gz
Repository: NFS
---------------------------------------------
Install Date: Fri Jan 28 17:59:00 EST 2022
Application: Apply_CSCwa47133_3.1.0.518_patch1
Version: 1
Install type: Application Remove
ise31ztp/admin#
Whereas, the show version command will only verify the patch that has been installed
ise31ztp/admin# show version
Cisco Application Deployment Engine OS Release: 3.1
ADE-OS Build Version: 3.1.0.135
ADE-OS System Architecture: x86_64
Copyright (c) 2005-2021 by Cisco Systems, Inc.
All rights reserved.
Hostname: ise31ztp
Version information of installed applications
---------------------------------------------
Cisco Identity Services Engine
---------------------------------------------
Version : 3.1.0.518
Build Date : Mon Aug 9 16:28:55 2021
Install Date : Fri Jan 28 16:44:01 2022
Cisco Identity Services Engine Patch
---------------------------------------------
Version : 1
Install Date : Fri Jan 28 17:50:18 2022
ise31ztp/admin#
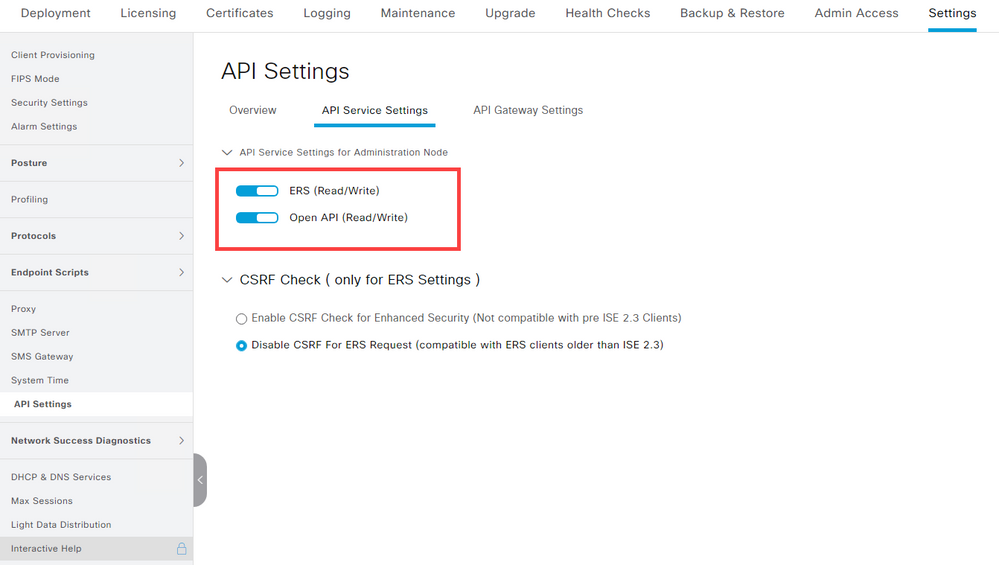
To verify that the services listed in the configuration were enabled, Log in to the Web GUI and navigate to Administration > System > Settings > API Settings and choose the API Service Settings tab.
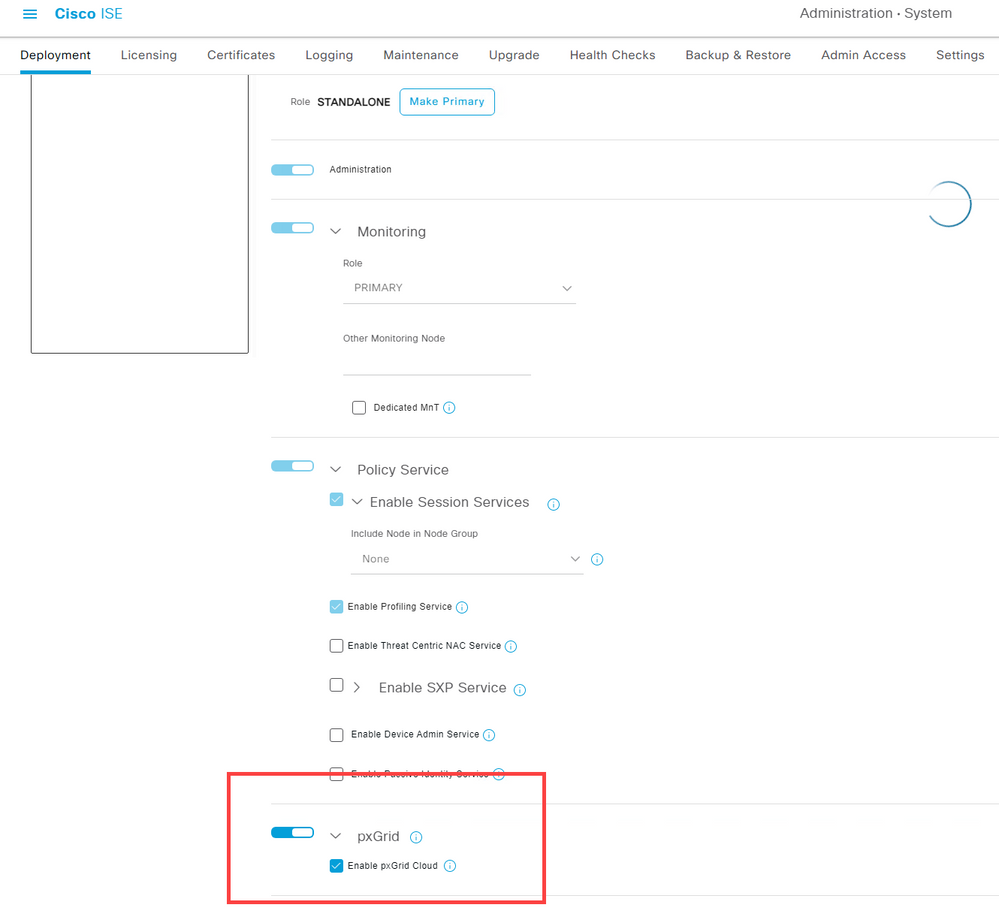
Then navigate to Administration > System > Deployment and choose the ISE Node. Scroll all the way down to verify pxGrid and pxGrid Cloud.
Can I use ZTP with ISE-PIC?
Yes! You CAN use the ZTP methods detailed above with ISE-PIC, too! Just remember to use the patch for ISE-PIC if you do install one through the ZTP process.
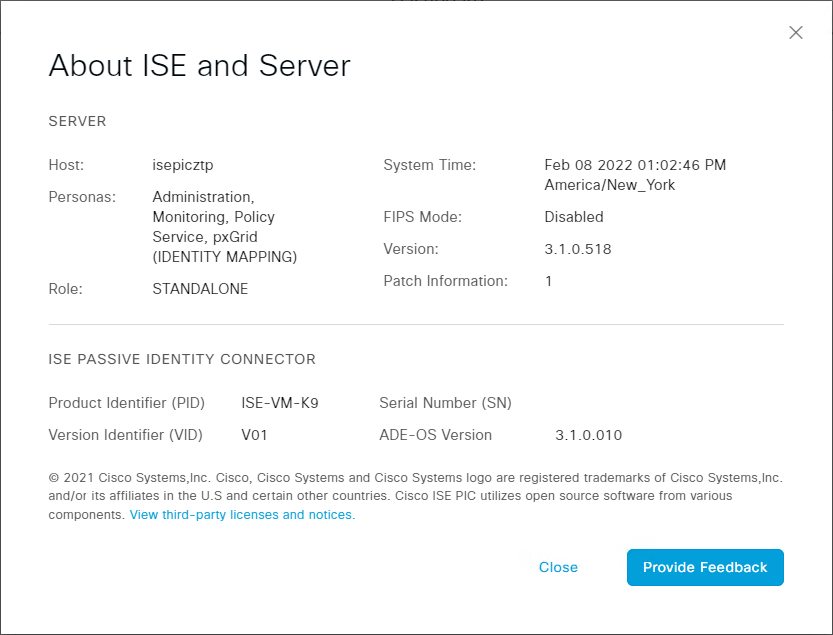
Here is a screenshot of the About ISE Passive Identity Connector window:
Here is the output from show version history:
isepicztp/admin# show version history
---------------------------------------------
Install Date: Tue Feb 8 11:33:50 EST 2022
Application: ise
Version: 3.1.0.518
Install type: Application Install
Bundle filename: ise.tar.gz
Repository: SystemDefaultPkgRepos
---------------------------------------------
Install Date: Tue Feb 8 12:36:05 EST 2022
Application: ise
Version: 1
Install type: Patch Install
Bundle filename: ise-pic-patchbundle-3.1.0.518-Patch1-21120304.SPA.x86_64.tar.gz
Repository: NFS
---------------------------------------------
Install Date: Tue Feb 8 12:45:44 EST 2022
Application: Apply_CSCwa47133_3.1.0.518_patch1
Version: 1
Install type: Application Install
Bundle filename: ise-apply-CSCwa47133_3.1.0.518_patch1-SPA.tar.gz
Repository: NFS
---------------------------------------------
Install Date: Tue Feb 8 12:46:59 EST 2022
Application: Apply_CSCwa47133_3.1.0.518_patch1
Version: 1
Install type: Application Remove
isepicztp/admin#
You can see that the Log4j fix was installed, as well. I have also added the output from show version:
isepicztp/admin# show version
Cisco Application Deployment Engine OS Release: 3.1
ADE-OS Build Version: 3.1.0.135
ADE-OS System Architecture: x86_64
Copyright (c) 2005-2021 by Cisco Systems, Inc.
All rights reserved.
Hostname: isepicztp
Version information of installed applications
---------------------------------------------
Cisco Identity Services Engine
---------------------------------------------
Version : 3.1.0.518
Build Date : Mon Aug 9 16:28:55 2021
Install Date : Tue Feb 8 11:21:30 2022
Cisco Identity Services Engine Patch
---------------------------------------------
Version : 1
Install Date : Tue Feb 08 12:36:05 2022
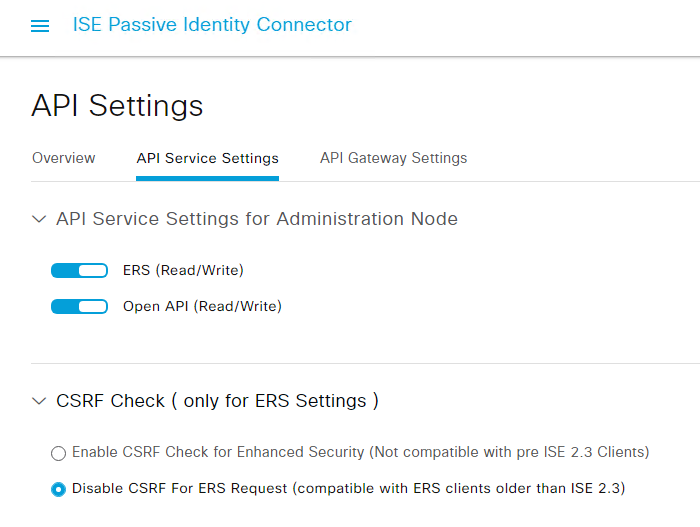
Navigate to Settings > API Settings > API Service Settings to verify the API services were enabled
In ISE-PIC, pxGrid is enabled by default, and there is currently to connection to - or setting for - pxGrid Cloud, so you can either remark out the lines for these services or delete them altogether.
Resources
- ISE 3.1 Installation Guide
- Install and Setup ISE 3.1 using Zero Touch Provisioning (ZTP)
- How to Install and Configure an NFS Server on Ubuntu
***The minimum versions noted for vCenter 6.7 are of my own experience and are NOT an official Cisco stance.***
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent stuff. In my opinion this should replace the official section of the Cisco ISE 3.1 Installation Guide which was not as helpful or nearly as detailed as this Guide. And the Official ZTP Tech Note (which seems to be based on Charlie's Guide?) also could use an update, especially on the nuances of VMWare vCenter version and the .img issue.
I also noted that Charlie recommends using BIOS instead of UEFI for the VM installs (the Install Guide again confused me into thinking I 'must use EFI' - after reading it again, it appears that EFI is only needed if HDD > 2 TB)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, thanks for posting this. I'm wondering if Charlie Morton or anyone else can help with an issue I'm having. I’ve been hitting the same issue in VMware with the auto install hanging that you were having on Hyper-V.
I've tried esxi 6.5 and 6.7 (v6.7.0.51000), and 7.0, and different physical servers, mounting the Cisco provided iso for installation as instructed.
Every single time the install hangs at the "Probing EDD ...." line just like the Hyper-V example, and I've let it sit for up to 20 hours but it never resolves. If I manually select option 1, it installs correctly.
Is there some special config that I'm missing?
As a side note, for the setup piece I've been using powerCLI to add an advanced configuration parameter with the "guestinfo.ise.ztp" setup script encoded in base64 (per this document: https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/217536-install-and-setup-ise-3-1-using-zero-tou.html#anc11). The auto install hangs whether or not this setting is in place though.
Thanks for your help.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: